Socially Engineered / Social Engineering Scams [Updated]
A SCARS™ Guide
Originally published: May 2018
You have probably heard the term “Social Engineering’ before, but what is it?
Social Engineering Is …
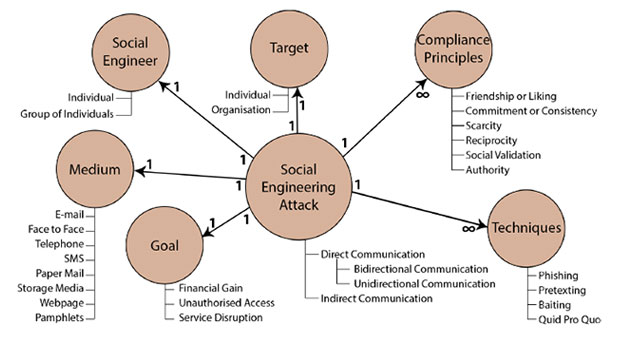
Social engineering, in the context of information security, refers to the psychological manipulation of people into performing actions or divulging confidential information.
It is a type of confidence trick (scam) for the purpose of information gathering, fraud, or system access, it differs from a traditional “con” in that it is often one of many steps in a more complex fraud scheme.
The term “social engineering” as an act of psychological manipulation of a human, is also associated with the social sciences, but its usage has caught-on among scammers, computer and information security professionals.
Social engineering is the art of manipulating people so they give up confidential information. The types of information these criminals are seeking can vary, but when individuals are targeted the criminals are usually trying to trick you into giving them your passwords or bank information, or access your computer to secretly install malicious software–that will give them access to your passwords and bank information as well as giving them control over your computer.
Criminals use social engineering tactics because it is usually easier to exploit your natural inclination to trust than it is to discover ways to hack your software. For example, it is much easier to fool someone into giving you their password than it is for you to try hacking their password (unless the password is really weak).
Security is all about knowing who and what to trust. It is important to know when and when not to take a person at their word and when the person you are communicating with is who they say they are. The same is true of online interactions and website usage: when do you trust that the website you are using is legitimate or is safe to provide your information?
Ask any security professional and they will tell you that the weakest link in the security chain is the human who accepts a person or scenario at face value. It doesn’t matter how many locks and deadbolts are on your doors and windows, or if have guard dogs, alarm systems, floodlights, fences with barbed wire, and armed security personnel; if you trust the person at the gate who says he is the pizza delivery guy and you let him in without first checking to see if he is legitimate you are completely exposed to whatever risk he represents.
Social Engineering Can Be Used For Good And Bad
As an attack vector, social engineering has been utilized in many different crime areas and cybercrime is no exception. In fact, many internet security companies continuously highlight the human factor as the weakest link in cybersecurity. Influencing people into acting against their own interest or the interest of an organization is often a simpler solution than resorting to malware or hacking.
Both law enforcement and the financial industry indicate that social engineering continues to enable attackers who lack the technical skills, motivation to use them or the resources to purchase or hire them. Additionally, targeted social engineering allows those technically gifted to orchestrate blended attacks bypassing both human and hardware or software lines of defense.
Key Threats Social Engineering Is Involved In:
- Romance Scams »
- Sextortion »/ Online Extortion
- CEO Fraud / Business Email Compromise (BEC) Scams »
- Phishing / Spearphishing »
- Advanced fee fraud (419) »
EVERY PERSON IN THE WESTERN WORLD KNOWS SOMEONE WHO HAS FALLEN FOR SOCIAL ENGINEERED SCAMS
Social Engineering Fraud
Criminals exploit a person’s trust in order to find out their banking details, passwords or other personal data.
Scams are carried out online – for example, by email or through social networking sites – by telephone, or even in person.
Some Examples Of Social Engineering Fraud
Social engineering fraud can be divided into two main categories:
Mass frauds, which use basic techniques and are aimed at a large number of people;
Targeted frauds, which have a higher degree of sophistication and are aimed at very specific individuals or companies.
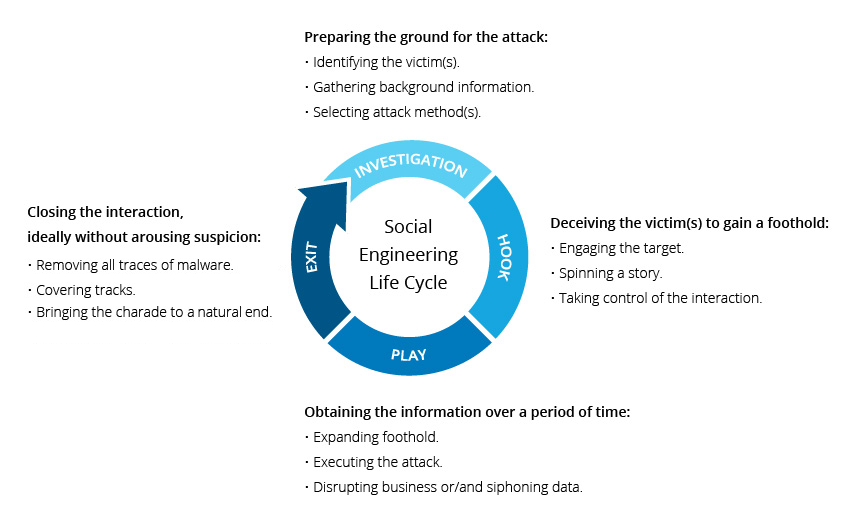
While the scams themselves differ, the methods used by criminals generally follow the same four steps:
- Gathering information
- Developing a relationship
- Exploiting any identified vulnerabilities
- Execution
Amongst The Well-Known Types Of Social Engineering Scams There Are:
TELECOM FRAUD
Fraudsters obtain the phone number of an individual, often an elderly person, then call them pretending to be a family member or public service and claiming to be in urgent need of cash.
They ask for money to be deposited in a designated bank account or delivered by hand in order to settle a traffic accident claim, loan shark debt, or other pressing financial need.
EMAIL SCAMS
Pretexting involves creating a scenario to engage a targeted victim; for example, impersonating a bank manager or tax inspector to convince the target to share personal information such as account numbers or passwords. This type of scam requires the criminal to conduct research on the victim, in order for the story to appear plausible.
Phishing uses a more generic scenario which is sent to a large number of people in an attempt to draw in as many victims as possible. This is usually done by e-mail and appears as if it comes from a legitimate source that many people frequent, such as popular online shopping websites, e-mail companies or computer tech support companies. The same techniques can also be executed by phone (Vishing) or by text message (SMishing).
BEC / CEO FRAUD / MANAGER FRAUD
Fraudsters gather publicly available information – usually through the Internet – about the company to be targeted.
They find out details of the Head of the company, and those managers and employees who are authorized to handle cash transfers.
The criminals use this data in order to impersonate the head of the company and coerce employees into making an urgent and high-value cash transfer to a designated bank account.
HACKING OF EMAIL ACCOUNTS
A cybercriminal hacks into an individual’s e-mail account and sends messages to their friends, relatives or colleagues claiming to be in trouble, for example, and needing money.
The recipient is unaware that the e-mail is not actually coming from the person they know, making them more inclined to assist – and thereby assist the criminal in gaining money or accessing their accounts.
SWEEPSTAKES OR LOTTERIES
A person receives a message along the following lines: ‘Congratulations, you are the grand prize winner! To claim your prize, all you need to do is pay a processing fee so we can release your winnings.’
Very often, names of popular companies or organizations are misused to give the lottery a trustworthy impression.
Despite making the requested payment, the victims never receive the expected prize winnings.
Other Kinds of Social Engineering On The Local Level – Scammer Techniques Include:
- Forensic Recovery – Analysis of non-securely disposed materials (USB keys, hard drives);
- Quid Pro Quo – Exchange of sensitive information under a misunderstanding or false pretenses;
- Baiting – Leaving an infected storage device to be picked up and plugged into a computer;
- Tailgating – Following someone to access secured premises;
- Diversion Theft – Redirecting a courier or transport delivery to another location.
What Does a Social Engineering Attack Look Like?
EMAIL FROM A FRIEND
If a criminal manages to hack or socially engineer one person’s email password they have access to that person’s contact list–and because most people use one password everywhere, they probably have access to that person’s social networking contacts as well.
Once the criminal has that email account under their control, they send emails to all the person’s contacts or leave messages on all their friend’s social pages, and possibly on the pages of the person’s friend’s friends.
Taking advantage of your trust and curiosity, these messages will:
- Contain a link that you just have to check out–and because the link comes from a friend and you’re curious, you’ll trust the link and click–and be infected with malware so the criminal can take over your machine and collect your contacts info and deceive them just like you were deceived
- Contain a download of pictures, music, movie, document, etc., that has malicious software embedded. If you download–which you are likely to do since you think it is from your friend–you become infected. Now, the criminal has access to your machine, email account, social network accounts, and contacts, and the attack spreads to everyone you know. And on, and on.
EMAIL FROM ANOTHER TRUSTED SOURCE
Phishing attacks are a subset of social engineering strategy that imitates a trusted source and concocts a seemingly logical scenario for handing over login credentials or other sensitive personal data. According to Webroot data, financial institutions represent the vast majority of impersonated companies and, according to Verizon’s annual Data Breach Investigations Report, social engineering attacks including phishing and pretexting (see below) are responsible for 93% of successful data breaches.
Using a compelling story or pretext, these messages may:
- Urgently ask for your help. Your ’friend’ is stuck in country X, has been robbed, beaten, and is in the hospital. They need you to send money so they can get home and they tell you how to send the money to the criminal.
- Use phishing attempts with a legitimate-seeming background. Typically, a phisher sends an e-mail, IM, comment, or text message that appears to come from a legitimate, popular company, bank, school, or institution.
- Ask you to donate to their charitable fundraiser or some other cause. Likely with instructions on how to send the money to the criminal. Preying on kindness and generosity, these phishers ask for aid or support for whatever disaster, political campaign, or charity is momentarily top-of-mind.
- Present a problem that requires you to “verify” your information by clicking on the displayed link and providing information in their form. The link location may look very legitimate with all the right logos, and content (in fact, the criminals may have copied the exact format and content of the legitimate site). Because everything looks legitimate, you trust the email and the phony site and provide whatever information the crook is asking for. These types of phishing scams often include a warning of what will happen if you fail to act soon because criminals know that if they can get you to act before you think, you’re more likely to fall for their phishing attempt.
- Notify you that you’re a ’winner.’ Maybe the email claims to be from a lottery, or a dead relative, or the millionth person to click on their site, etc. In order to give you your ’winnings’ you have to provide information about your bank routing so they know how to send it to you or give your address and phone number so they can send the prize, and you may also be asked to prove who you are often including your social security number. These are the ’greed phishes’ where even if the story pretext is thin, people want what is offered and fall for it by giving away their information, then having their bank account emptied, and identity is stolen.
- Pose like a boss or coworker. It may ask for an update on an important, proprietary project your company is currently working on, for payment information pertaining to a company credit card, or some other inquiry masquerading as a day-to-day business.
BAITING SCENARIOS
These social engineering schemes know that if you dangle something people want, many people will take the bait. These schemes are often found on Peer-to-Peer sites offering a download of something like a hot new movie, or music. But the schemes are also found on social networking sites, malicious websites you find through search results, and so on.
Or, the scheme may show up as an amazingly great deal on classified sites, auction sites, etc.. To allay your suspicion, you can see the seller has a good rating (all planned and crafted ahead of time).
People who take the bait may be infected with malicious software that can generate any number of new exploits against themselves and their contacts, may lose their money without receiving their purchased item, and, if they were foolish enough to pay with a check, may find their bank account empty.
RESPONSE TO A QUESTION YOU NEVER HAD
Criminals may pretend to be responding to your request for help from a company while also offering more help. They pick companies that millions of people use such as a software company or bank. If you don’t use the product or service, you will ignore the email, phone call, or message, but if you do happen to use the service, there is a good chance you will respond because you probably do want help with a problem.
For example, even though you know you didn’t originally ask a question you probably a problem with your computer’s operating system and you seize on this opportunity to get it fixed. For free! The moment you respond you have bought the crook’s story, given them your trust, and opened yourself up for exploitation.
The representative, who is actually a criminal, will need to ’authenticate you’, have you log into ’their system’ or, have you log into your computer and either give them remote access to your computer so they can ’fix’ it for you, or tell you the commands so you can fix it yourself with their help–where some of the commands they tell you to enter will open a way for the criminal to get back into your computer later.
CREATING DISTRUST
Some social engineering is all about creating distrust, or starting conflicts; these are often carried out by people you know and who are angry with you, but it is also done by nasty people just trying to wreak havoc, people who want to first create distrust in your mind about others so they can then step in as a hero and gain your trust, or by extortionists who want to manipulate information and then threaten you with disclosure.
This form of social engineering often begins by gaining access to an email account or another communication account on an IM client, social network, chat, forum, etc. They accomplish this either by hacking, social engineering, or simply guessing really weak passwords.
- The malicious person may then alter sensitive or private communications (including images and audio) using basic editing techniques and forward these to other people to create drama, distrust, embarrassment, etc. They may make it look like it was accidentally sent, or appear like they are letting you know what is ’really’ going on.
- Alternatively, they may use the altered material to extort money either from the person they hacked or from the supposed recipient.
There are literally thousands of variations to social engineering attacks. The only limit to the number of ways they can socially engineer users through this kind of exploit is the criminal’s imagination. And you may experience multiple forms of exploits in a single attack. Then the criminal is likely to sell your information to others so they too can run their exploits against you, your friends, your friends’ friends, and so on as criminals leverage people’s misplaced trust.
TAGS: SCARS, Information About Scams, Anti-Scam, Scams, Scammers, Fraudsters, Cybercrime, Crybercriminals, Romance Scams, Scam Victims, Online Fraud, Online Crime Is Real Crime, Scam Avoidance, Social Engineering Scams, Social Engineered, Social Engineer, Persuasion,
PLEASE SHARE OUR ARTICLES WITH YOUR FRIENDS & FAMILY
HELP OTHERS STAY SAFE ONLINE – YOUR KNOWLEDGE CAN MAKE THE DIFFERENCE!
THE NEXT VICTIM MIGHT BE YOUR OWN FAMILY MEMBER OR BEST FRIEND!
By the SCARS™ Editorial Team
Society of Citizens Against Relationship Scams Inc.
A Worldwide Crime Victims Assistance & Crime Prevention Nonprofit Organization Headquartered In Miami Florida USA & Monterrey NL Mexico, with Partners In More Than 60 Countries
To Learn More, Volunteer, or Donate Visit: www.AgainstScams.org
Contact Us: Contact@AgainstScams.org



![Social-Engineering-Infographic[1]](https://romancescamsnow.com/wp-content/uploads/2021/02/social-engineering-infographic1.png)

Is,Hanah Gazar, part of these romance scams