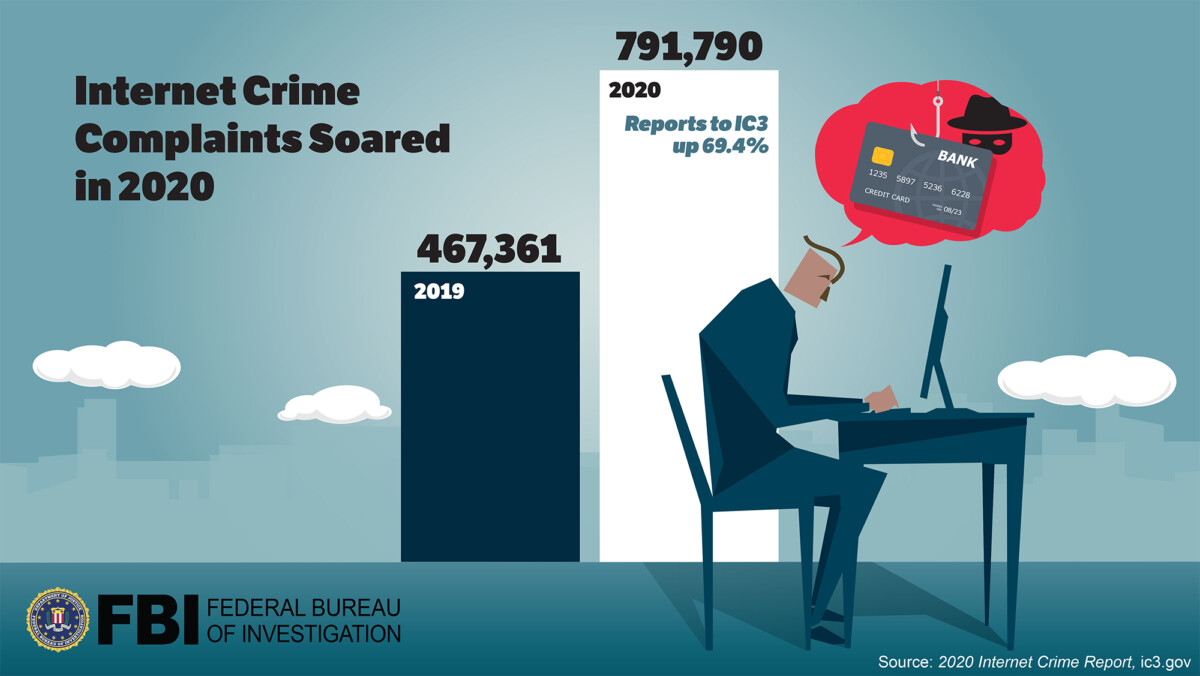
FBI Releases 2020 Internet Crime Report
In 2020, while the American public was focused on protecting our families from a global pandemic and helping others in need, cybercriminals took advantage of an opportunity to profit from our dependence on technology to go on an Internet crime spree.
These criminals used phishing, spoofing, extortion, and various types of Internet-enabled fraud to target the most vulnerable in our society – medical workers searching for personal protective equipment, families looking for information about stimulus checks to help pay bills, and many others.
FBI Releases the Internet Crime Complaint Center 2020 Internet Crime Report, Including COVID-19 Scam Statistics
The FBI’s Internet Crime Complaint Center has released its annual report. The 2020 Internet Crime Report includes information from 791,790 complaints of suspected internet crime—an increase of more than 300,000 complaints from 2019—and reported losses exceeding $4.2 billion. State-specific statistics have also been released and can be found within the 2020 Internet Crime Report and in the accompanying 2020 State Reports.
The top three crimes reported by victims in 2020 were phishing scams, non-payment/non-delivery scams, and extortion. Victims lost the most money to business email compromise scams, romance and confidence schemes, and investment fraud. Notably, 2020 saw the emergence of scams exploiting the COVID-19 pandemic. The IC3 received over 28,500 complaints related to COVID-19, with fraudsters targeting both businesses and individuals.
In addition to statistics, the IC3’s 2020 Internet Crime Report contains information about the most prevalent internet scams affecting the public and offers guidance for prevention and protection. It also highlights the FBI’s work combating internet crime, including recent case examples. Finally, the 2020 Internet Crime Report explains the IC3, its mission, and functions.
The IC3 gives the public a reliable and convenient mechanism to report suspected internet crime to the FBI. The FBI analyzes and shares information from submitted complaints for investigative and intelligence purposes, for law enforcement, and for public awareness.
With the release of the 2020 Internet Crime Report, the FBI wants to remind the public to immediately report suspected criminal internet activity to the IC3 at ic3.gov. By reporting internet crime, victims are not only alerting law enforcement to the activity, but aiding in the overall fight against cybercrime.
Top 33 Cyber-related Crimes Per The FBI IC3 Report
As you can see in the following table, FBI reporting is massively below realistic actual numbers. Furthermore, that alters the priorities and leads to mistakes in FBI prioritization of cyber-related crimes.
2020 IC3 Report CRIME TYPES By Victim Count |
|
| # | CRIME TYPE AND NUMBER OF COMPLAINTS RECEIVED BY THE FBI IC3.GOV |
| 1 | Phishing/Vishing/Smishing/Pharming 241,342 |
| 2 | Non-Payment/Non-Delivery 108,869 |
| 3 | Extortion 76,741 |
| 4 | Personal Data Breach 45,330 |
| 5 | Identity Theft 43,330 |
| 6 | Spoofing 28,218 |
| 7 | Misrepresentation 24,276 |
| 8 | Confidence Fraud/Romance 23,751 |
| 9 | Harassment/Threats of Violence 20,604 |
| 10 | BEC/EAC 19,369 |
| 11 | Credit Card Fraud 17,614 |
| 12 | Employment 16,879 |
| 13 | Tech Support 15,421 |
| 14 | Real Estate/Rental 13,638 |
| 15 | Advanced Fee 13,020 |
| 16 | Government Impersonation 12,827 |
| 17 | Other 10,372 |
| 18 | Lottery/Sweepstakes/Inheritance 8,501 |
| 19 | Investment 8,788 |
| 20 | IPR/Copyright and Counterfeit 4,213 |
| 21 | Crimes Against Children 3,202 |
| 22 | Corporate Data Breach 2,794 |
| 23 | Ransomware 2,474 |
| 24 | Denial of Service/TDoS 2,018 |
| 25 | Malware/Scareware/Virus 1,423 |
| 26 | Health Care Related 1,383 |
| 27 | Civil Matter 968 |
| 28 | Re-shipping 883 |
| 29 | Charity 659 |
| 30 | Gambling 391 |
| 31 | Terrorism 65 |
| 32 | Hacktivist 52 |
| 33 | Overpayment 10,988 |
2020 IC3 Report Highlights:
COVID-19 Fraud:
The IC3 received over 28,500 complaints from victims related to emerging financial crime around government stimulus programs, unemployment insurance, Paycheck Protection Program (PPP) loans, and Small Business Economic Injury Disaster Loans, among others. The most prevalent scheme, however, involved government impersonation; as in, criminals reaching out to victims pretending to be from the government in order to gather personal information or illicit money. Other prolific scams involved criminals asking individuals to pay out of pocket or sign in with their Office 365 credentials to place their name on a waiting list for fake COVID-19 vaccinations. The Report encouraged individuals to protect themselves by not providing their personal information to unknown sources and to rely only on trusted sources such as an individual’s doctor or the CDC for medical information. Additional IC3 recommendations included using “extreme caution” in online communication and verifying external email senders, attachments, and links.
Business Email Compromise (BEC):
BEC schemes topped the list of costliest scams reported by victims in 2020 with adjusted losses exceeding $1.8 billion and making up nearly half of all losses reported. This type of attack targets businesses and frequently involves criminals using social engineering or computer intrusion techniques to compromise legitimate business email accounts to conduct unauthorized transfers of funds. In 2020, the IC3 observed an increase in the number of BEC complaints relating to the use of identity theft and funds being converted to cryptocurrency. 2020 complaints involve criminals posing as tech support or engaging in romantic fraud to lure a victim into providing their ID, which the criminal then used to establish a bank account to receive the stolen BEC funds and then transfer those funds to a cryptocurrency account. The IC3 Recovery Asset Team (“RAT”), which works as a liaison between victims, financial institutions, and FBI field offices to assist in reducing financial losses resulting from BEC scams, recommends that BEC victims: (i) contact the originating financial institution as soon as fraud is recognized to request a recall or reversal and a Hold Harmless Letter or Letter of Indemnity; (ii) file a detailed complaint of the incident with the IC3; (iii) monitor incident trends on IC3’s website; and (iv) never make payment changes without verifying the intended recipient.
Tech Support Fraud:
Tempered only slightly by pandemic lockdowns, the IC3 identified that tech support fraud continues to be a growing problem in 2020. The IC3 received 15,421 tech support fraud complaints from victims in 60 countries in 2020, with losses exceeding $146 million—up 171% from 2019. Notably, the majority of victims reported to be over the age of 60 and experienced over 84% of the losses. This type of attack involves criminals attempting to defraud consumers by posing as support or service representatives offering to resolve technical, security, or customer issues to elicit fraudulent payments or access to consumers’ computers. 2020 complaints involve criminals posing as customer support for financial institutions, utility companies, or virtual currency exchanges. Readers are encouraged to visit the IC3 website for additional information on tech support fraud.
Ransomware:
The IC3 highlighted ransomware as another growing area in 2020 after receiving 2,474 complaints with adjusted losses of $29.1 million, which is nearly triple the amount of ransomware-related losses identified in 2019. This type of attack frequently involves criminals deploying malicious software, or malware, that encrypts and blocks access to data on a computer system until payment of the ransom is made. Among the most common means of infection in 2020, as identified by the IC3, involved targeted email phishing campaigns and exploitation of remote desktop protocol or software vulnerabilities.
“The FBI does not encourage paying a ransom to criminal actors” the Report stated, as payment does not guarantee that a victim’s files will be recovered. Payment may instead “embolden adversaries to target additional organizations, encourage other criminal actors to engage in the distribution of ransomware, and /or fund illicit activities.”
Even so, the Report emphasizes that the decision to pay the ransom should not discourage a business or individual from reporting the incident to the local FBI field office or IC3.
Romance Scams:
Romance scams is given no special consideration in the report, nor is sextortion. The above are the only crimes the FBI though worthy of special discussion in the report.
FBI’s 2020 Report
Remember, that the FBI only reports what was reported to them. Most victims do not report these crimes – the current estimate is that only 3-5% of victims report these. And people who are victims of multiple scams almost never do.
THESE NUMBERS ARE BETWEEN 1-3% OF ACTUAL CRIMES!
Take any number you see and multiply it by 20 for a more realistic number!
TAGS: SCARS, Information About Scams, Anti-Scam, Scams, Scammers, Fraudsters, Cybercrime, Crybercriminals, Romance Scams, Scam Victims, Online Fraud, Online Crime Is Real Crime, Scam Avoidance, FBI, Federal Bureau of Investigation, United States Government, IC3.gov, Internet Complaint Center, 2020 Report
PLEASE SHARE OUR ARTICLES WITH YOUR FRIENDS & FAMILY
HELP OTHERS STAY SAFE ONLINE – YOUR KNOWLEDGE CAN MAKE THE DIFFERENCE!
THE NEXT VICTIM MIGHT BE YOUR OWN FAMILY MEMBER OR BEST FRIEND!
By the SCARS™ Editorial Team
Society of Citizens Against Relationship Scams Inc.
A Worldwide Crime Victims Assistance & Crime Prevention Nonprofit Organization Headquartered In Miami Florida USA & Monterrey NL Mexico, with Partners In More Than 60 Countries
To Learn More, Volunteer, or Donate Visit: www.AgainstScams.org
Contact Us: Contact@AgainstScams.org




Please Leave A Comment - Tell Us What You Think About This!