The Evolution of Cybercrime
Introduction – BazaCall or BazarCall – Same Thing
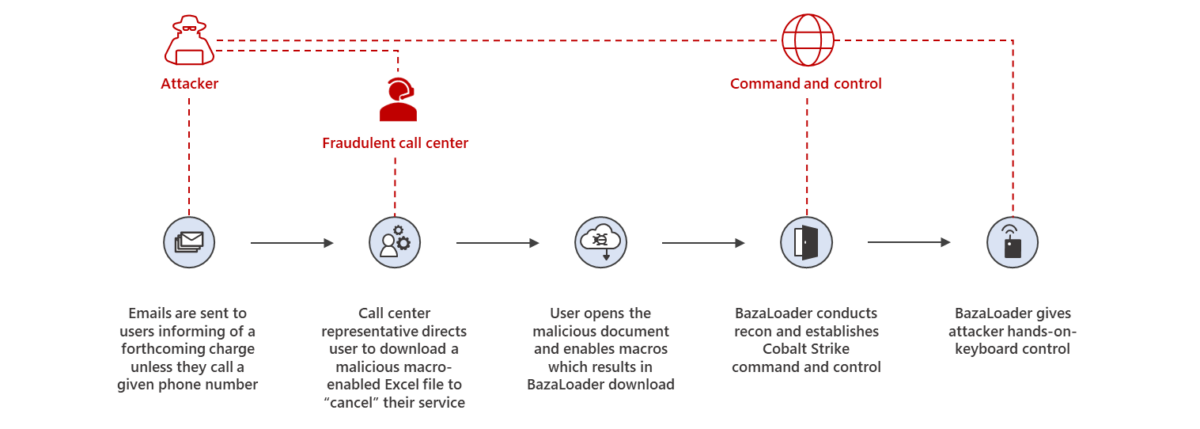
For the past year, security researchers have been waging an online battle against a new ‘BazarCall’ malware that uses call centers to distribute some of the most damaging Windows malware.
The new malware was discovered being distributed by call centers in late January 2022 and is named BazarCall, or BazaCall, as the threat actors initially used it to install the BazarLoader malware.
While other malware is now being distributed, researchers continue to identify the distribution campaign as BazarCall.
BazarCall Social Engineering Tactics
BazarCall campaigns weave phone-based scams and email-based or message-based scams together!
They leave out the malicious links or attachments in email messages that can be detected by automation and that would alert aware users in favor of phone numbers that recipients are misled into calling.
It’s a technique reminiscent of vishing and tech support scams where potential victims are being cold-called by the attacker, except in BazarCall’s case, targeted users must dial the number. And when they do, the users are connected with actual humans on the other end of the line, who then provide step-by-step instructions for installing malware into their devices.
BazarCall campaigns first came into the limelight in late 2020 and since then cybersecurity professionals have seen a constant increase in attacks pertaining to this campaign. It was initially found to be delivering BazaarLoader (backdoor software) which was used as an entry point to deliver ransomware.
What is particularly interesting is the evolution of the social engineering tactics of BazarCall. With the growth in cyberattacks, people are increasingly aware of the common tactics used by cybercriminals. As awareness has improved, BazarCall has ceaselessly adapted and evolved its social engineering tactics accordingly.
Out With The Links And Attachments, In With The Customer Service Phone Numbers
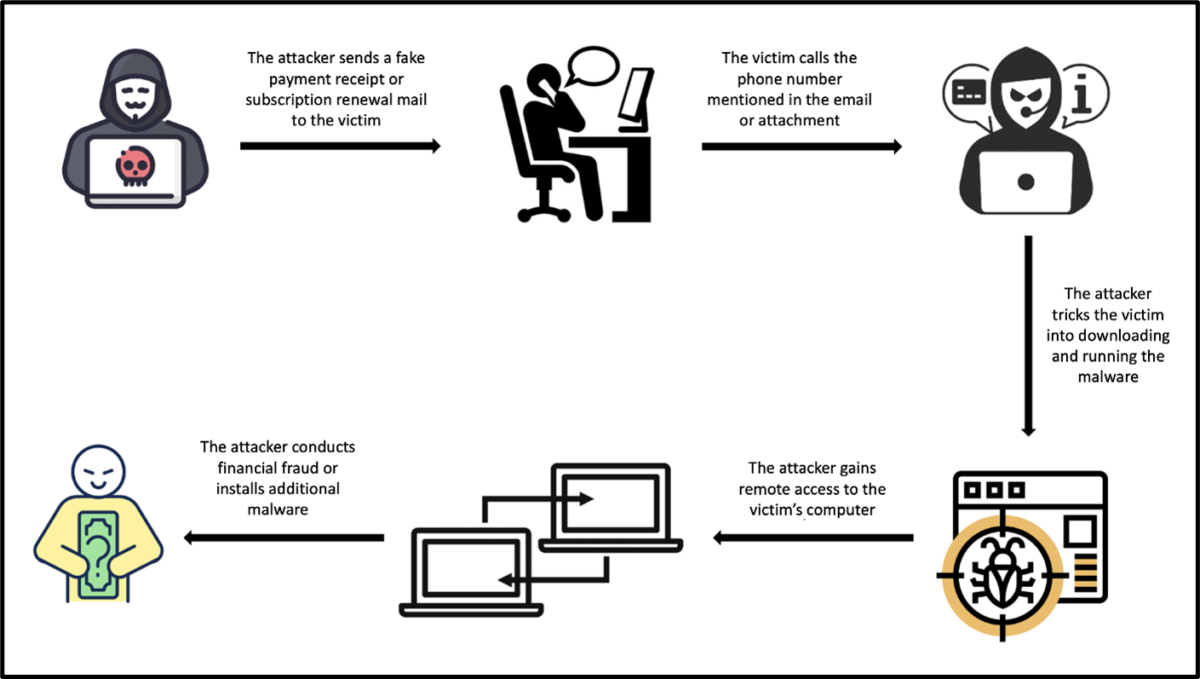
BazaCall campaigns begin with an email that uses various social engineering lures to trick target recipients into calling a phone number. For example, the email informs users about a supposed expiring trial subscription and that their credit card will soon be automatically charged for the subscription’s premium version. Each wave of emails in the campaign uses a different “theme” of subscription that is supposed to be expiring, such as a photo editing service or a cooking and recipes website membership. In a more recent campaign, the email does away with the subscription trial angle and instead poses as a confirmation receipt for a purchased software license.
Analyzing BazaCall (BazarCall) Attacks
Using emails obtained by cybersecurity professionals, researchers contacted various call centers to learn about different techniques and tactics utilized by attackers.
Based on the analysis, they were able to generalize the attack flow of the BazaCall campaigns and categorize the same into three phases (see above). The study also revealed the evolution of social engineering tactics which was particularly noticed in the call center scripts used by the scammers to trick victims into downloading and installing malware in their system, the scammers are now found to be utilizing many different types of conversation scripts.
Attack Phase 1 – The bait
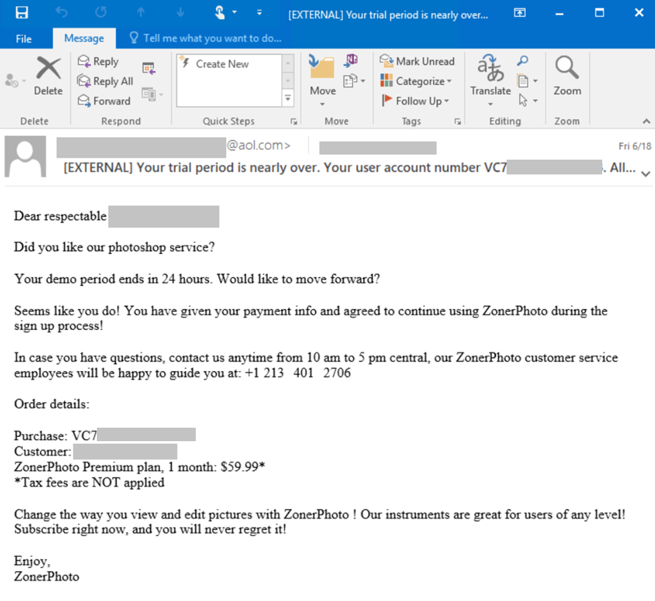
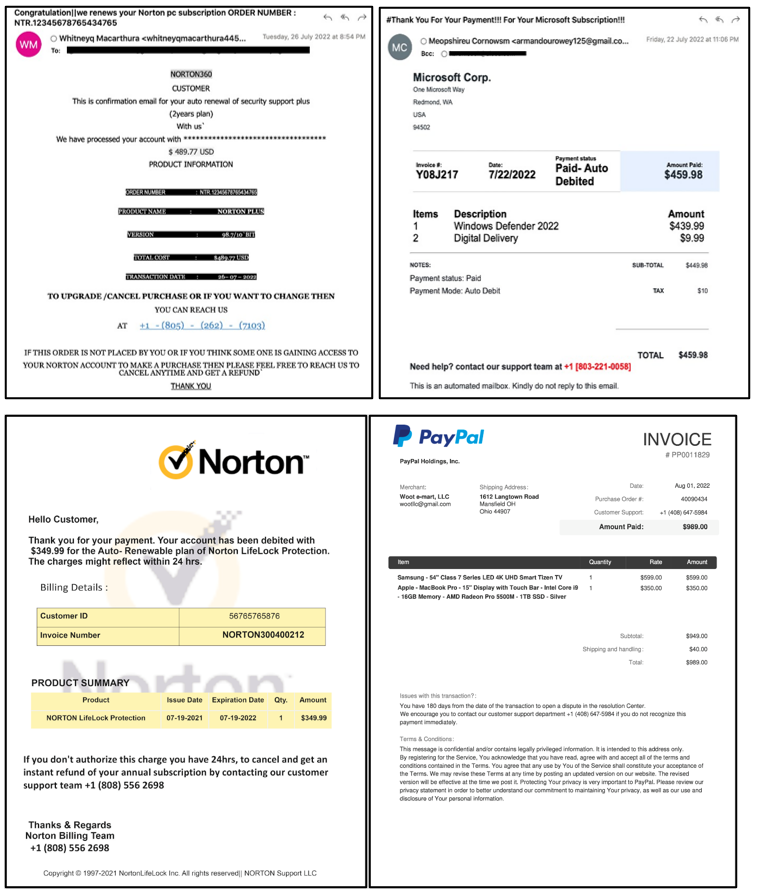
The delivery vector is a fake notification email that informs the recipient about a charge on their account for the purchase/renewal of a product/subscription.
It contains all the generic information like Product Name, Date, Model, etc. along with a unique invoice number used by the scammer to identify the victim. In addition, the email states that the victim can call the phone number for any queries or cancellation requests. In different variants, the information was found to be present in the email body or as a PDF attachment.
The campaign was seen impersonating many brands like Geek Squad, Norton, McAfee, PayPal, Microsoft, and many others.
BazaCall Emails
BazaCall email is sent from a different sender, typically using free email services and likely-compromised email addresses.
The lures within the email use fake business names that are similar to the names of real businesses. A recipient who then searches the business name online to check the email’s legitimacy may be led to believe that such a company exists and that the message they received has merit.
Some sample subject lines are listed below.
They each have a unique “account number” created by the attackers to identify the recipients:
- Soon you’ll be moved to the Premium membership, as the demo period is ending. Personal ID: KT[unique ID number]
- Automated premium membership renewal notice GW[unique ID number] ?
- Your demo stage is nearly ended. Your user account number VC[unique ID number]. All set to continue?
- Notification of an abandoned road accident site! Must to get hold of a manager! [body of email contains unique ID number]
- Thanks for deciding to become a member of BooyaFitness. Fitness program was never simpler before [body of email contains unique ID number]
- Your subscription will be changed to the gold membership, as the trial is ending. Order: KT[unique ID number]
- Your free period is almost ended. Your member’s account number VC[unique ID number]. Ready to move forward?
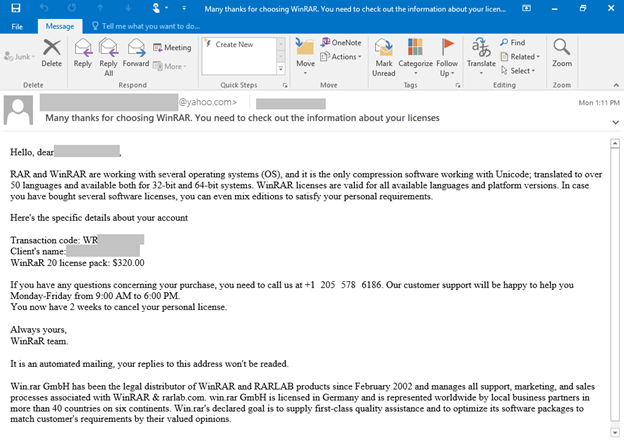
- Thank you for getting WinRAR pro plan. Your order # is WR[unique ID number].
- Many thanks for choosing WinRAR. You need to check out the information about your licenses [body of email contains unique ID number]
While the subject lines in most of the observed campaigns contain similar keywords and occasional emojis, each one is unique because it includes an alphanumeric sequence specific to the recipient. This sequence is always presented as a user ID or transaction code, but it actually serves as a way for the attacker to identify the recipient and track the latter’s responses to the campaign. The unique ID numbers largely follow the same pattern, which the regular expression [A-Z]{1,3}(?:\d{9,15}) can surface, for example, L0123456789 and KT01234567891.
In one recent BazaCall campaign, the unique ID was present in the body of the email, but not in the subject line:
Phase 2 – The Attack
Once the recipient calls the scam call center the trickiest phase of the attack begins: manipulating the victim into downloading and running malware on their system.
BazaCall employs many different tactics to achieve this. We will now go into greater detail on the conversation script categories.
THE (DIS)HONEST GUY
This tactic begins with the scammer asking the victim for basic details like invoice number, phone number, email address etc. Following this, the scammer takes a pause and pretends to check his system to find any invoice relative to the details shared by the victim and then conveys that no invoice could be found.
The scammer suggests that the email received by the victim is a spam email and should be ignored.
The scammer then asks the victim if their system is slow or if they are facing any other issues with it, then the scammer suggests that the victim’s system might be affected by malware which would have caused them to receive the spam email. He then offers to schedule a call back where an executive can scan and check the victim’s system and resolve any issues.
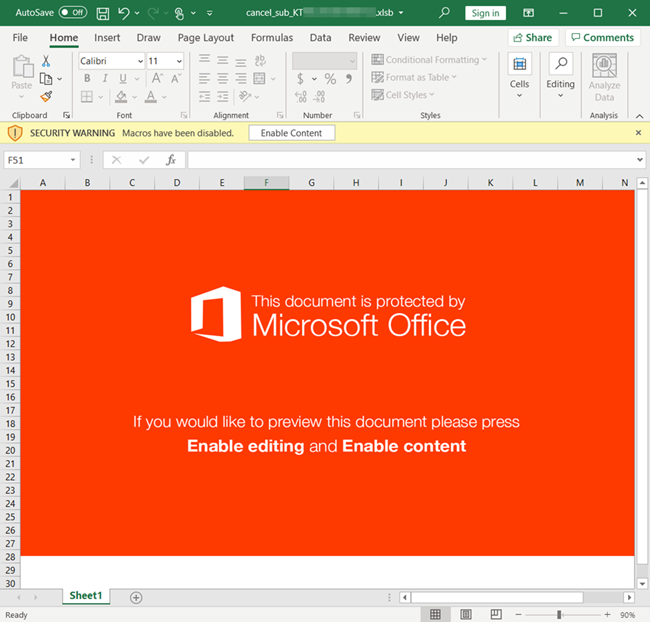
The next call begins with the scammer asking the name of the operating system which the victim is using. Following the answer, the scammer asks the victim to open a specific URL which is a malicious website masqueraded to look like a customer support website.
The scammer then asks the victim to enter a code on the website to download a file that he claims to be anti-virus software. As an additional tactic to make the call sound more authentic, the scammer asks the victim to keep a note of the code for verification purposes. Finally, the scammer asks the victim to execute the downloaded file to run the scan on their system.
THE (FAKE) INCIDENT RESPONDER
This tactic was found to be used in PayPal-themed BazaCall campaigns. It begins with the scammer asking the victim for the details like invoice number, debited amount etc. The scammer then asks if the victim uses PayPal, on answering “Yes,” the scammer then asks for the email ID which is linked to their PayPal account.
The scammer then pretends to check the information related to the victim’s PayPal account and states that the account has been accessed from 8 (or any random high number) of devices. The scammer asks if all these devices belong to the victim and just like anyone would, the victim gets alarmed. The scammer then asks the victim about their current location, following the answer the scammer informs the victim that their account was accessed from a suspicious location, the scammer would then name any random location which is far from the victim’s current location.
Now, the scammer asks the victim to search “What’s my IP” on Google and suggests that if the result has a title as “your public IP address,” that means the connection is public and hence insecure. The scammer then suggests that to secure the connection, the victim must open a particular website. The final step is where the scammer asks the victim to download and execute a file.
THE OVER COMPENSATOR
Just like the other categories, this tactic also begins with the scammer asking for basic details and pretending to check their system for the same. The scammer then confirms that the amount (the fee) has been deducted from the victim’s account for the security (or any other) product/service.
He then asks the victim if they would want to cancel the subscription and if the victim says “Yes,” the scammer explains the importance of security software to the victim and would ask if the victim still wants to proceed with the cancellation.
This is used as a tactic to make the call sound authentic by convincing the victim that the caller is motivated to sell the subscription for the security product and is not motivated to proceed with the cancellation. The scammer then states that the victim needs to be connected to a support agent to complete the cancellation and receive a refund. As an additional tactic to gain trust, the scammer repeatedly asks the victim not to share any sensitive information with him as the call is being recorded and the company policy does not allow him to ask for any sensitive information from the customer. The final step is where the scammer asks the victim to download and execute another file.
THE TERRIBLE/SENSIBLE ONE
This tactic is used in the “security subscription renewal” themed campaigns. This also begins with the scammer asking for some basic details and pretending to find information related to it. The scammer then explains to the victim that the charge has been placed on their account because the security product that came pre-installed with their laptop has expired and has hence been automatically renewed to continue the security protection for the device.
The scammer then asks the victim if they would like to continue with their security subscription or cancel it.
As the victim requests to cancel the subscription, the scammer asks if the victim has any other security solution present on their system. This is also a trust-gaining tactic where the scammer pretends to be interested in the security of the victim’s system. The scammer then states that the victim needs to be connected to the cancellation server to complete the cancellation process and receive a refund. Here too, the final step is like the other cases, where the scammer asks the victim to download and execute yet another file.
The Relevance of the Invoice ID
All the variants of the campaign began with the scammer asking for the Invoice ID from the victim. That is because each Invoice ID is uniquely generated for every email.
When the victim provides the Invoice ID to the scammer, the scammer searches for the same in their database and if found, the scammer can use details related to the Invoice ID in order to pretend to already have the victim’s details like name, email address, the amount debited, etc. This gives an impression of authenticity to the victim and helps to convince him into downloading and running the malware.
The following are some examples of the fake support websites found by security professionals which are being used in BazaCall campaigns to deliver malware.
Phase 3 – The kill
Once the malware is executed, then begins the third phase of the attack where the malware is used to conduct financial fraud or push additional malware to the system.
Based on the analysis by cybersecurity researchers the majority of BazaCall campaigns utilize a file name like “support.Client.exe” and the following is an example of such a file spotted by our researchers:
| Name | Support.Client.exe |
| Size | 85.70 KB |
| File-Type | Win32 EXE |
| SHA 256 | ead2b47848758a91466c91bed2378de1253d35db3505b5f725c289468d24645b |
| SHA 1 | bc664ec8dff62f5793af24f6ca013e29498062f2 |
| MD5 | 1e88b21d4c7d51f312337b477167ed25 |
Once it has been executed, the file connects to a malicious domain and downloads a ClickOnce Security and Deployment Application file (or others depending on what brand is being impersonated) with “.application” extension. ClickOnce is a deployment technology that allows it to create self-updating Windows-based applications that can be installed and run with minimal user interaction. Once this process has started the war is lost.
The malware then follows to drop multiple files on the victim’s system that are required for the proper execution of the malware. The dropped files are often found to be for ScreenConnect software which is a legitimate remote-control software by ConnectWise. Cybercriminals, however, have been utilizing ScreenConnect for many years as a part of the attack chain when they drop spyware, ransomware, etc. BazaCall campaigns have also been consistent with the use of ScreenConnect for more than a year.
Once the malware completes downloading the dependencies, it executes and the scammer gains remote access to the victim’s system. The attacker can also show a fake lock screen and make the system inaccessible to the victim, where the attacker is able to perform tasks without the victim being aware of them.
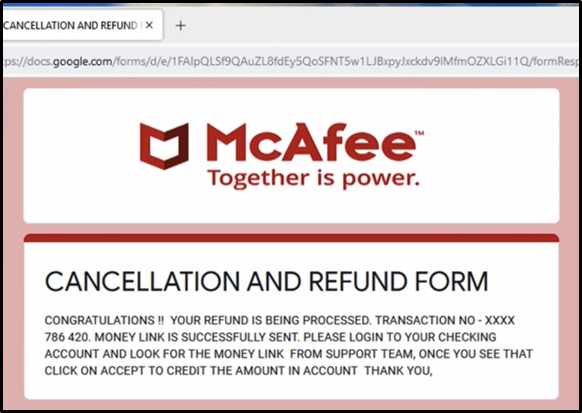
In one such case noticed by cybersecurity professionals, the scammer opens a Fake Cancellation Form behind the lock screen and then asks the victim to fill out the form that requires generic details like name, address, email, etc. On submitting the form, the victim receives a success message saying the refund is being processed and they should log into their bank account and accept the refund.
The scammer then asks the victim to login into their bank account to complete the refund process where the scammer would manipulate the victim into sending money to the scammer by making it look as if the victim is receiving the amount. This is achieved by locking the victim’s screen and then unlocking the screen when the transaction requires an OTP (One Time Password/MFA Code) or a secondary password. The victim is also presented with a fake refund successful page (above) to convince him into believing that they have received the refund. The scammer may also send an SMS to the victim with a fake money-received message as an additional tactic to prevent the victim from suspecting any fraud.
The above example only presents one of the many directions the attack can lead to, the attacker might also use remote access to install additional malware in the victim’s system to gain persistent access to the victim’s system which can be then used to spy on the activities, steal data, steal credentials or install ransomware on the system.
Summary
This is a profoundly serious form of scam/cybercrime attack!
Every online user needs to modify their behaviors to prevent phishing and other related scams and attack. However, romance scam victims are 1000 times more likely to be impulsive and not stop when alarm bells go off! Even one of our own Board Members after ten years scam-free yet fell for a recent phishing scam.
Online safe is partly about knowledge, but knowledge and intelligence are not enough. You have to change your behavior and eliminate impulsiveness. If you cannot do that you will remain vulnerable and be scammed over and over.
We thank Microsoft & Trelix for the use of their images and some content.
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment below!
To Learn More Also Look At Our Article Catalogs
Scam & Crime Types
More SCARS
- ScamsNOW Magazine – ScamsNOW.com
- ContraEstafas.org
- ScammerPhotos.com
- AnyScam.com – reporting
- AgainstScams.org – SCARS Corporate Website
- SCARS YouTube Video Channel









![An Example of How Scammers Use Emergency Scams - 2014 [UPDATED 2024] - on SCARS RomanceScamsNOW.com](https://romancescamsnow.com/wp-content/uploads/2014/06/emergency-scams.png)

Please Leave A Comment - Tell Us What You Think About This!