Scam Basics – Business Email Compromise Fraud
Business Email Compromise
Business email compromise (BEC)—also known as email account compromise (EAC)—is one of the most financially damaging online crimes. It exploits the fact that so many of us rely on email to conduct business—both personal and professional.
In a BEC scam, criminals send an email message that appears to come from a known source making a legitimate request, like in these examples:
- A vendor your company regularly deals with sends an invoice with an updated mailing address.
- A company CEO asks her assistant to purchase dozens of gift cards to send out as employee rewards. She asks for the serial numbers so she can email them out right away.
- A homebuyer receives a message from his title company with instructions on how to wire his down payment.
- Versions of these scenarios happened to real victims. All the messages were fake. And in each case, thousands—or even hundreds of thousands—of dollars were sent to criminals instead.
Business Email Compromise (BEC) Fraud
#BECareful – Don’t Let Scammers Trick You Into Making Payments To Their Accounts
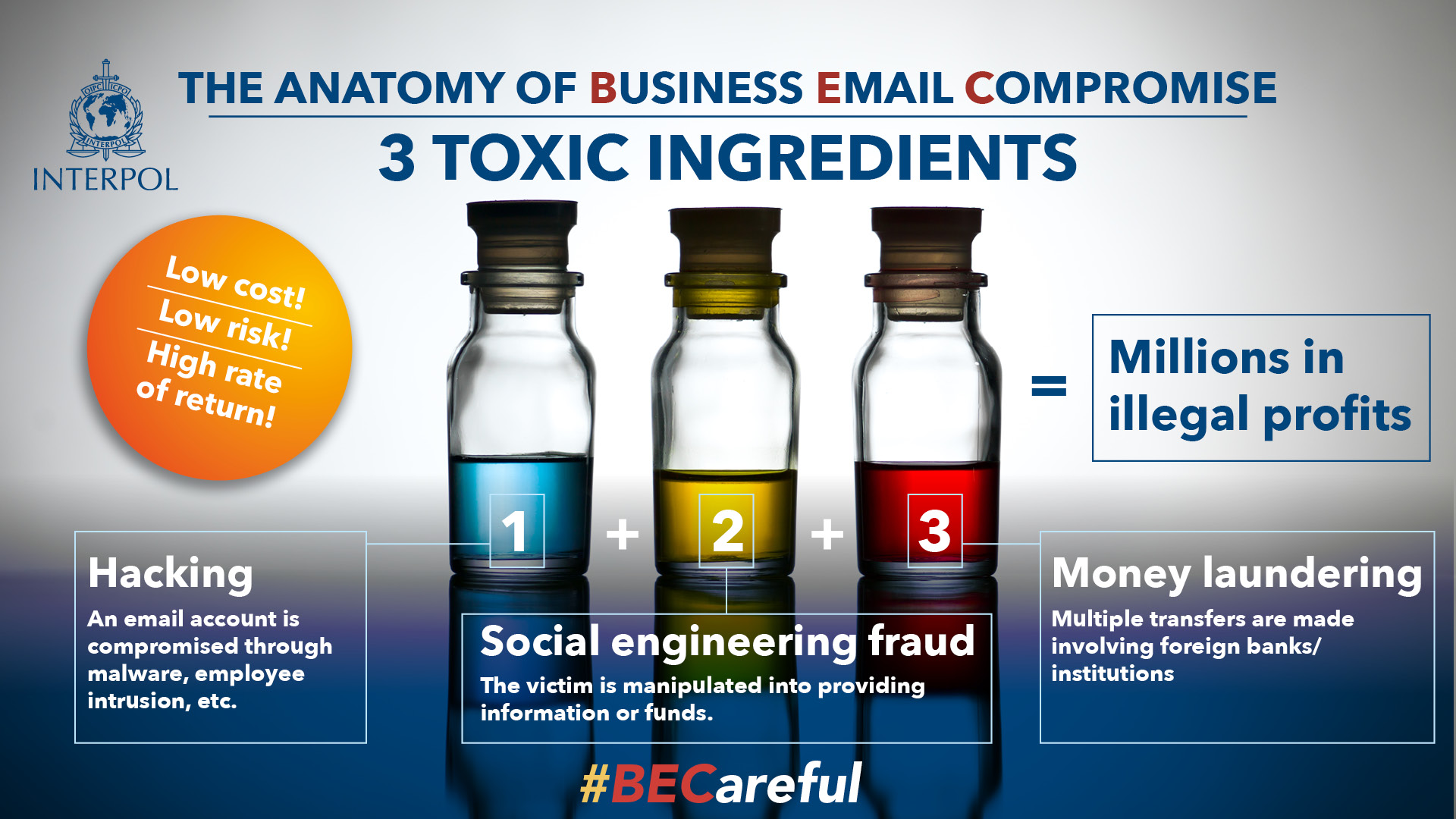
Criminals hack into email systems or use social engineering tactics to gain information about corporate payment systems, then deceive company employees into transferring money into their bank account.
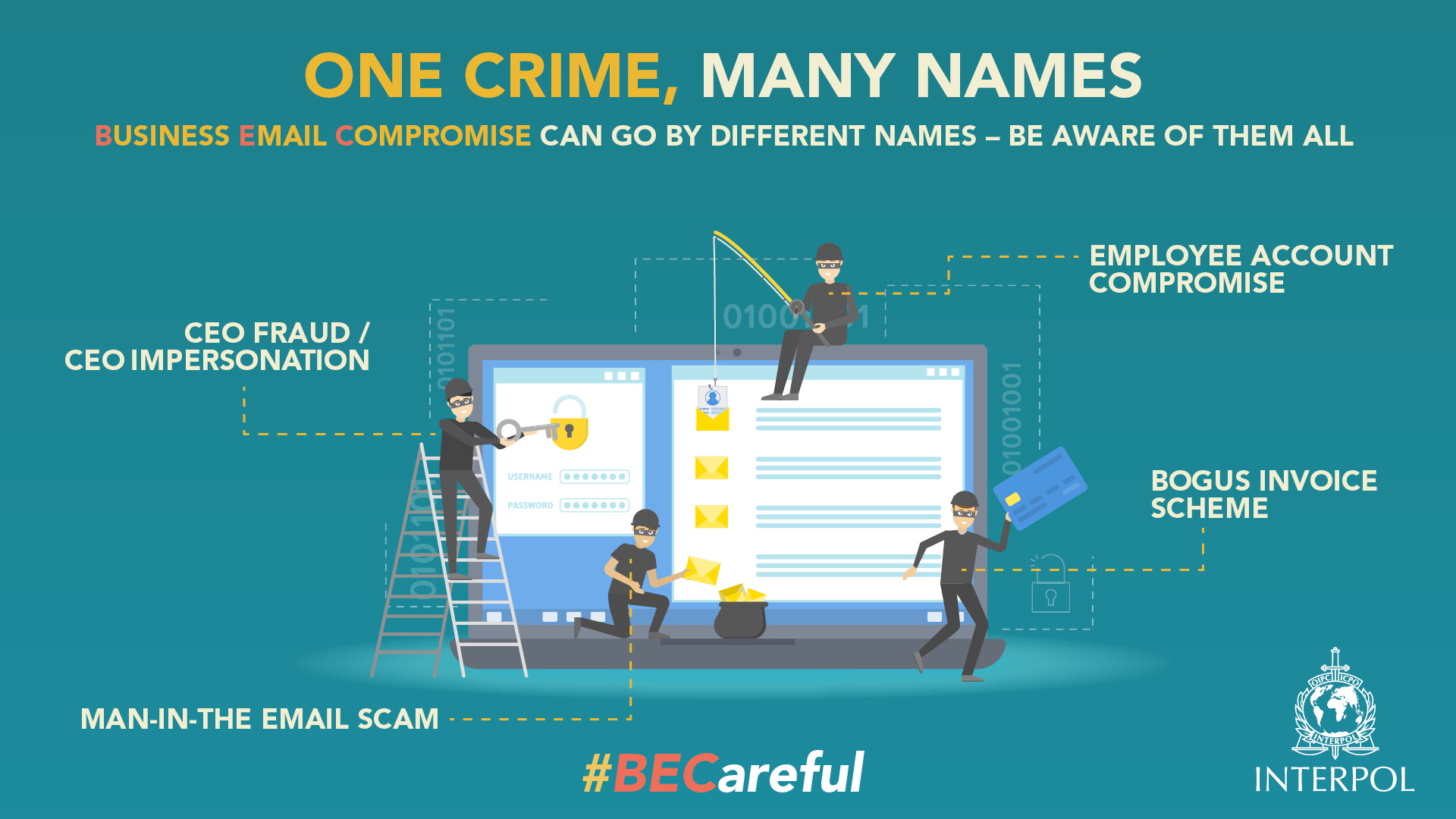
What Is A Business Email Compromise Scam
How Criminals Carry Out BEC Scams – A Scammer Might:
- Spoof an email account or website. Slight variations on legitimate addresses:
(john.kelly@examplecompany.com vs. john.kelley@examplecompany.com)
fool victims into thinking fake accounts are authentic. - Send spearphishing emails. These messages look like they’re from a trusted sender to trick victims into revealing confidential information. That information lets criminals access company accounts, calendars, and data that gives them the details they need to carry out the BEC schemes.
- Use malware. Malicious software can infiltrate company networks and gain access to legitimate email threads about billing and invoices. That information is used to time requests or sends messages so accountants or financial officers don’t question payment requests. Malware also lets criminals gain undetected access to a victim’s data, including passwords and financial account information.
How to Protect Yourself
- Be careful with what information you share online or on social media. By openly sharing things like pet names, schools you attended, links to family members, and your birthday, you can give a scammer all the information they need to guess your password or answer your security questions.
- Don’t click on anything in an unsolicited email or text message asking you to update or verify account information. Look up the company’s phone number on your own (don’t use the one a potential scammer is providing), and call the company to ask if the request is legitimate.
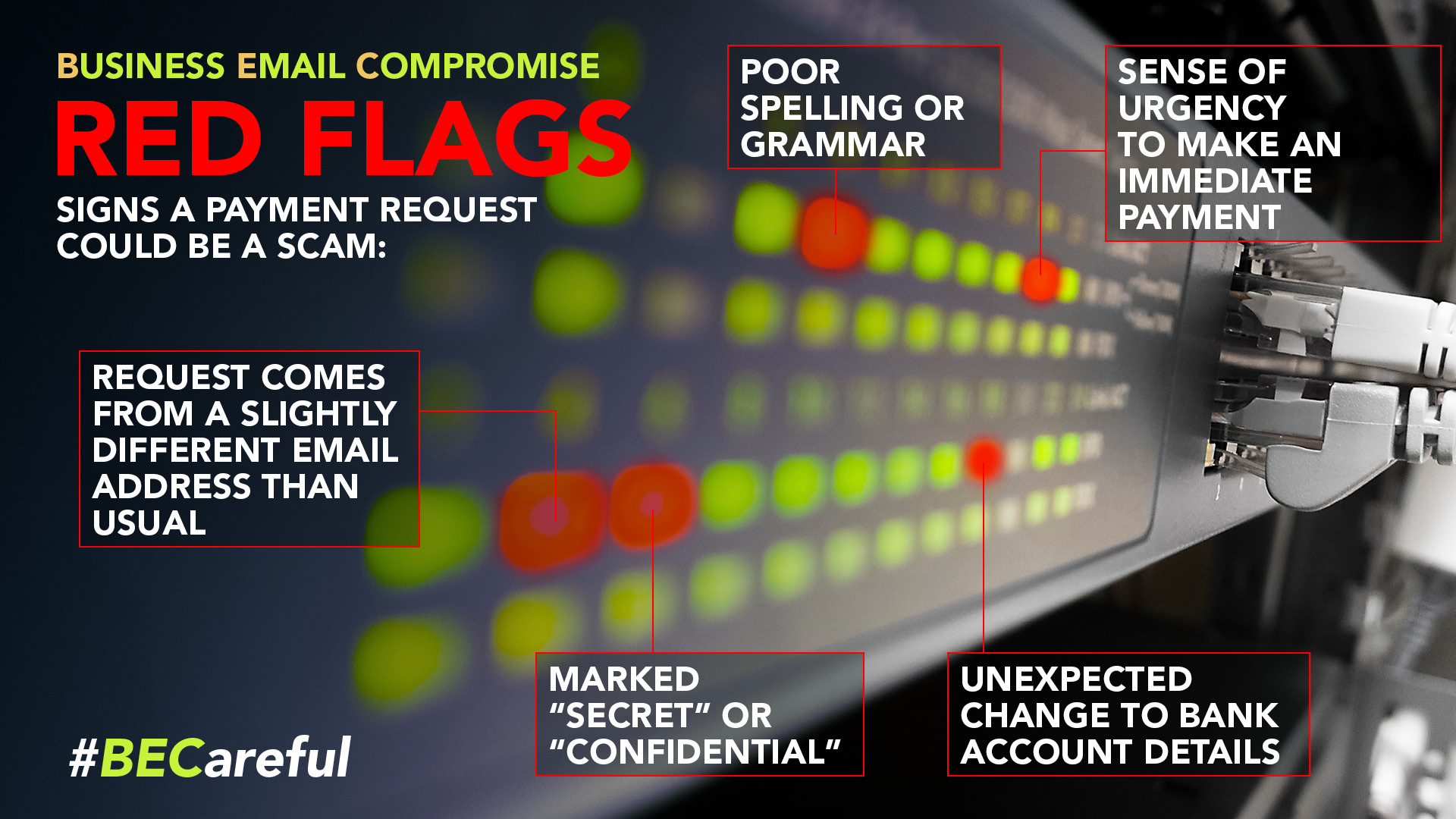
- Carefully examine the email address, URL, and spelling used in any correspondence. Scammers use slight differences to trick your eye and gain your trust.
- Be careful what you download. Never open an email attachment from someone you don’t know, and be wary of email attachments forwarded to you.
- Set up two-factor (or multi-factor) authentication on any account that allows it, and never disable it.
- Verify payment and purchase requests in person if possible or by calling the person to make sure it is legitimate. You should verify any change in an account number or payment procedures with the person making the request.
- Be especially wary if the requestor is pressing you to act quickly.
More BEC Protection Basics
Protect your corporate systems from hacking attempts
- DO use anti-virus, firewall, and other tools and scan computers and devices regularly to prevent malware infections.
- DO keep your personal and business computers up to date: pay attention to security alerts, update security patches, conduct periodic systems checks.
- DO make sure that your email accounts are well protected and don’t share the passwords.
- DON’T click on attachments or links you aren’t expecting, even if they have innocent sounding names (invoice, for example). They often contain malware giving access to monitor your email/computer activities.
- DO enable spam filters and block all access to suspicious or blacklisted websites.
Be vigilant of suspicious or unexpected ‘urgent’ payment requests or changes
- DO look carefully at the sender’s email address. Criminals often create an account with a very similar email address to your business partners so keep your eyes peeled!
- DO spread the word so any colleagues dealing with bank accounts are aware of the scam.
- If you receive an email concerning a change of payment method or bank account,
- DO contact the payment recipient through another channel (such as by phone) to verify this claim.
- DON’T reply directly to the email.
- DO verify the authenticity of websites before providing any personal or sensitive information.
Avoid becoming a target from the beginning
- DON’T post sensitive or personal information on social media. This can be used by fraudsters to target you.
- DO shred all confidential documents and dispose of them properly.
- DO use different passwords for every account, change them regularly and enable two-factor authentication on all your accounts whenever possible.
- DO use strong passwords which include numbers, symbols, capital, and lower-case letters.
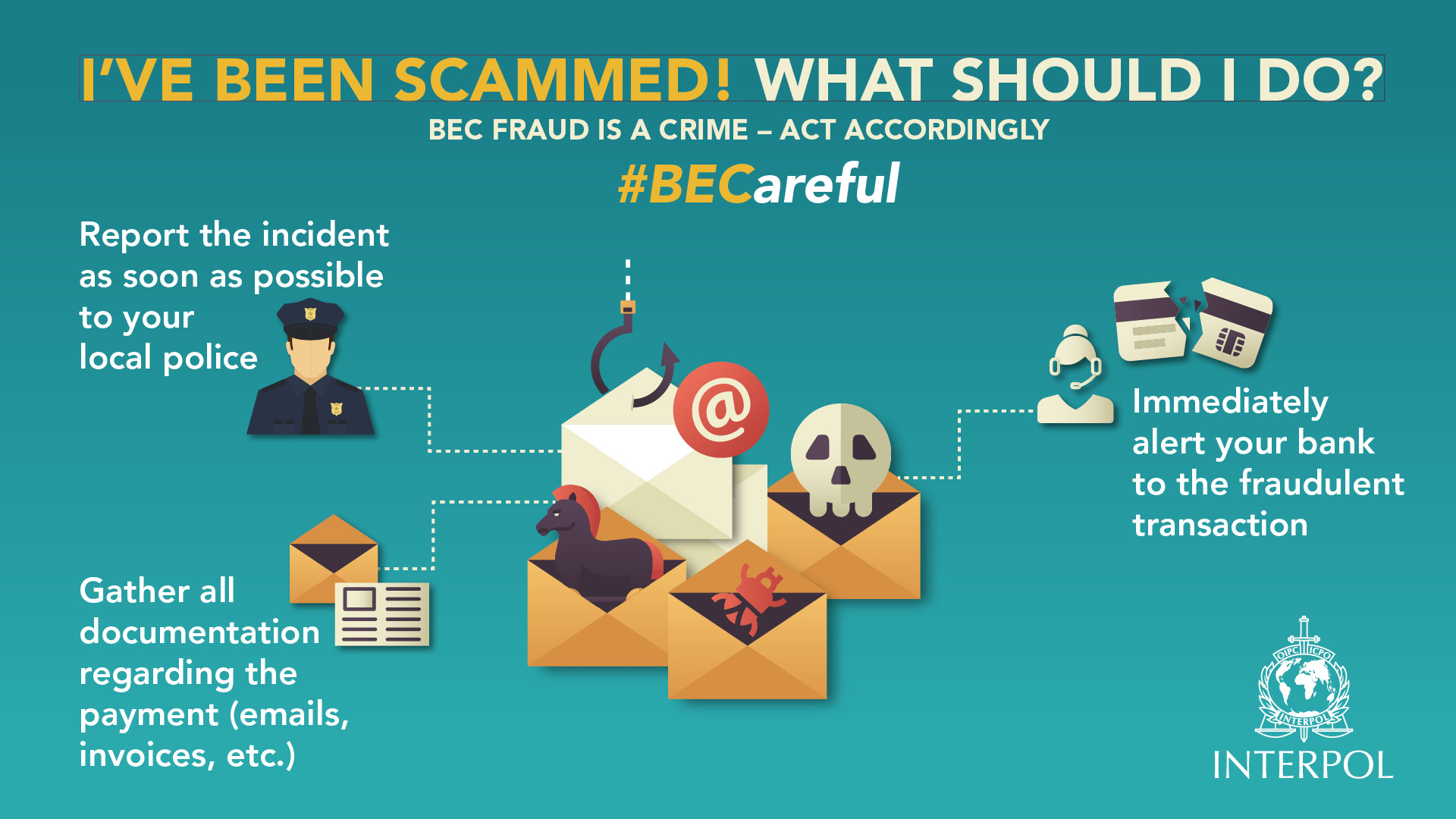
If you paid the money – now what?
- Gather all documentation regarding the transaction and emails/invoices received and DO report the incident as soon as possible to your local police.
- DO immediately alert your bank to the fraudulent transaction. The bank should immediately try to recall the funds.
- DO consider consulting a civil lawyer in the country where the money was deposited into the beneficiary bank account. This might be of help to address the bank in trying to recover the money and/or launch a civil complaint regarding the account holder.
How to Report (USA)
If you or your company falls victim to a BEC scam, it’s important to act VERY quickly:
- Contact your financial institution immediately and request that they contact the financial institution where the transfer was sent.
- Next, contact your local FBI field office to report the crime.
- Also file a complaint with the FBI’s Internet Crime Complaint Center (IC3).
If your business is not in the United States, contact your National Police Force or their Cybercrimes Police Unit (most countries now have them.)
TAGS: SCARS, Information About Scams, Anti-Scam, Scams, Scammers, Fraudsters, Cybercrime, Crybercriminals, Scam Victims, Online Fraud, Online Crime Is Real Crime, Scam Avoidance, BEC Scams, Business Email Compromise, Financial Fraud, Business Fraud
PLEASE SHARE OUR ARTICLES WITH YOUR FRIENDS & FAMILY
HELP OTHERS STAY SAFE ONLINE – YOUR KNOWLEDGE CAN MAKE THE DIFFERENCE!
THE NEXT VICTIM MIGHT BE YOUR OWN FAMILY MEMBER OR BEST FRIEND!
By the SCARS™ Editorial Team
Society of Citizens Against Relationship Scams Inc.
A Worldwide Crime Victims Assistance & Crime Prevention Nonprofit Organization Headquartered In Miami Florida USA & Monterrey NL Mexico, with Partners In More Than 60 Countries
To Learn More, Volunteer, or Donate Visit: www.AgainstScams.org
Contact Us: Contact@AgainstScams.org



![business-email-compromise-timeline-022717[1]](https://romancescamsnow.com/wp-content/uploads/2021/02/business-email-compromise-timeline-0227171.jpg)






Leave A Comment