PDFs: The Most Underestimated Cyber Threat
When it comes to personal or business cybersecurity, the focus often falls on sophisticated malware and intricate hacking techniques. However, one usually overlooked vector for cyberattacks is the ubiquitous PDF (Portable Document Format) file.
PDFs are widely used for sharing documents, presentations, and other forms of content, but they can also be exploited by attackers to deliver malicious payloads and compromise unsuspecting users.
Can PDFs have viruses?
Yes, they can. Because PDFs are one of the most universally used file types, hackers and bad actors can find ways to use these normally harmless files — just like dot-com files, JPGs, Gmail, and Bitcoin — to create security threats via malicious code.
In A Hurry And Want To Check A File Now?
Scanning a PDF for viruses in a hurry: Many tools work equally well for Mac or PC users. One of the most popular is VirusTotal, which might be the best solution when you’re in a hurry because it doesn’t even require a download or software installation.
Go here to scan a saved PDF: VirusTotal File Scan
The Appeal of PDFs for Cyberattacks
There are several reasons why PDFs are attractive to cybercriminals:
-
Ubiquity: PDFs are widely used and supported across various operating systems and software applications, making them a convenient and accessible target for attackers.
-
Ease of Exploitation: Vulnerabilities in PDF readers and the format itself can be exploited to execute malicious code or embed hidden data within the document.
-
Undetectability: PDFs can be carefully crafted to bypass security measures and remain undetected by antivirus software and other security tools.
-
Social Engineering: Attackers can leverage social engineering tactics, such as phishing emails with attached PDFs, to trick users into opening infected documents.
PDF Attack Techniques
Attackers employ various techniques to exploit PDFs for cyberattacks, here are the most common ones:
-
Embedding Malicious Code: Attackers can embed malicious code, such as JavaScript or Flash, within PDFs to take control of a user’s system when the document is opened.
-
Exploiting Vulnerabilities: Attackers can exploit vulnerabilities in PDF readers or the format itself to execute arbitrary code on a user’s system.
-
Data Embedding: Attackers can embed hidden data, such as stolen credentials or sensitive information, within PDFs, making it difficult to detect and remove.
-
Phishing Attacks: Attackers can use PDFs as attachments in phishing emails to trick users into opening infected documents, allowing malware to be installed or sensitive information to be stolen.
An explanation of the different ways hackers can exploit PDFs to deliver malicious payloads and compromise users:
Malicious Attachments:
Hackers can attach files like executables or scripts to PDFs. When you open the PDF, these attachments can run automatically, installing malware on your computer.
Embedded Links:
PDFs can contain links that, when clicked, take you to malicious websites. These websites can contain malware, phishing pages, or exploit kits that target vulnerabilities in your system.
Exploiting PDF Vulnerabilities:
Hackers can take advantage of weaknesses in PDF software itself. If you open a PDF using an outdated PDF reader, the hacker can execute code that harms your system.
Hidden Content and Layers:
PDFs can have layers and hidden content. Hackers can hide malicious content behind seemingly harmless information. When opened, this hidden content can be revealed and perform malicious actions.
Malicious JavaScript:
PDFs can contain JavaScript code that runs when you open the PDF. Hackers can use JavaScript to download malware, steal your information, or redirect you to malicious websites.
Phishing Attacks:
Hackers can create PDFs that look like legitimate documents, such as invoices, contracts, or forms. These fake documents may contain links to phishing sites or ask for your personal information.
Malicious Macros:
Some PDF readers support macros, similar to those in Microsoft Office documents. Hackers can embed malicious macros in PDFs that, when enabled, can execute code leading to malware infection.
Document Exploitation:
Hackers can embed exploits within PDF files that target software vulnerabilities. These vulnerabilities could allow the hacker to take control of your system.
Watering Hole Attacks:
In a watering hole attack, hackers compromise a website you frequently visit. They then inject malicious code into a PDF hosted on the compromised site. When you download and open the PDF, your system could be compromised.
Document Encryption and Passwords:
Some hackers send password-protected PDFs via email, claiming the password is provided in the message. In your haste, you might enter the password, allowing the hacker to access your system or sensitive information.
NOTE: Just because a PDF may have a password does not mean it is safe!
Take These Precautions Against PDF-Based Attacks
Determining the safety of a PDF file before opening it is crucial to protect yourself from potential cyberattacks. Here are some effective strategies to verify the safety of a PDF:
- Browser PDF reader extension: make sure it is a reputable extension from a trusted maker.
- Browser Anti-Malware extension installed: Such as MalwareBytes or Bitdefender.
- Adobe brand is the official PDF reader: install the Adobe PDF reader for safety.
-
Check the Sender’s Origin: If you receive a PDF via email, carefully examine the sender’s email address. If it appears unfamiliar, suspicious, or from an unknown source, exercise caution and avoid opening the attachment. NOTE: this is no guaranty, it could have come from someone you know and their computer was compromised.
-
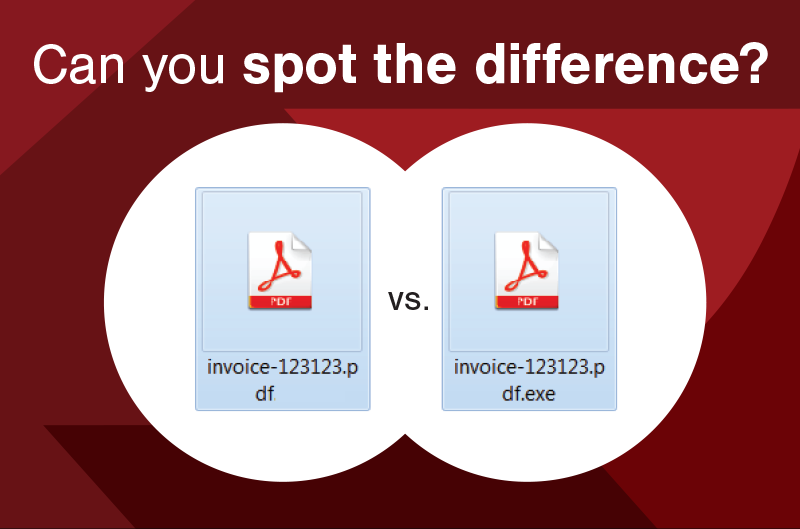
Verify the File Extension: Ensure that the file extension is indeed .pdf and not .exe or another executable format. Malicious actors often disguise malware as PDFs by changing the extension.
-
Scan the PDF with Antivirus/Anti-Malware Software: Utilize a reputable antivirus software to scan the PDF before opening it. This can help detect and remove embedded malware or potential threats. SCARS uses MalwareBytes
-
Enable Protected View: Most PDF readers offer a “Protected View” mode that restricts the execution of potentially harmful code within the PDF. Enable this mode to add an extra layer of protection.
-
Hover over Links: Before clicking on any links within the PDF, hover your cursor over them to reveal the actual destination URL. If the URL appears suspicious or unfamiliar, avoid clicking on it.
-
Check for Embedded Macros: Some PDF readers support macros, which can be used to automate tasks or execute code. If the PDF contains macros, proceed with caution and only enable them if you trust the source.
-
Avoid Opening PDFs from Untrusted Sources: Refrain from opening PDFs attached to unsolicited emails or downloaded from untrusted websites. These sources are more likely to contain malicious PDFs.
-
Update PDF Reader Software: Keep your PDF reader software up to date to ensure it has the latest security patches and vulnerability fixes.
-
Educate Yourself: Stay informed about the latest PDF-based attack techniques and educate yourself on how to identify and avoid them.
By following these precautions, you can significantly reduce the risk of opening a malicious PDF and compromising your device or sensitive information. Remember, vigilance and awareness are key to staying safe in the digital world.
Summary
PDFs, while essential for document sharing and collaboration, can also pose a significant cybersecurity threat. By understanding the risks associated with PDFs and taking appropriate precautions, users can protect themselves from malicious actors and safeguard their valuable information. Remember, vigilance and awareness are key to staying safe in the ever-evolving cybersecurity landscape.
SCARS Resources:
- Getting Started Right: ScamVictimsSupport.org
- For New Victims of Relationship Scams newvictim.AgainstScams.org
- Subscribe to SCARS Newsletter newsletter.againstscams.org
- Sign up for SCARS professional support & recovery groups, visit support.AgainstScams.org
- Join our Scam Survivors United Chat & Discussion Group facebook.com/groups/scam.survivors.united
- Find competent trauma counselors or therapists, visit counseling.AgainstScams.org
- Become a SCARS Member and get free counseling benefits, visit membership.AgainstScams.org
- Report each and every crime, learn how to at reporting.AgainstScams.org
- Learn more about Scams & Scammers at RomanceScamsNOW.com and ScamsNOW.com
- Scammer photos ScammerPhotos.com
- SCARS Videos youtube.AgainstScams.org
- Self-Help Books for Scam Victims are at shop.AgainstScams.org
- Donate to SCARS and help us help others at donate.AgainstScams.org
- Worldwide Crisis Hotlines: https://blog.opencounseling.com/suicide-hotlines/
Other Cyber Resources
- Block Scam Domains: Quad9.net
- Global Cyber Alliance ACT Cybersecurity Tool Website: Actionable Cybersecurity Tools (ACT) (globalcyberalliance.org) https://act.globalcyberalliance.org/index.php/Actionable_Cybersecurity_Tools_(ACT)_-_Simplified_Cybersecurity_Protection
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment below!
Do You Need Support?
Get It Now!
SCARS provides the leading Support & Recovery program for relationship scam victims – completely FREE!
Our managed peer support groups allow victims to talk to other survivors and recover in the most experienced environment possible, for as long as they need. Recovery takes as long as it takes – we put no limits on our support!
SCARS is the most trusted support & education provider in the world. Our team is certified in trauma-informed care, grief counseling, and so much more!
To apply to join our groups visit support.AgainstScams.org
We also offer separate support groups for family & friends too.
Become a
SCARS STAR™ Member
SCARS offers memberships in our STAR program, which includes many benefits for a very low annual membership fee!
SCARS STAR Membership benefits include:
- FREE Counseling or Therapy Benefit from our partner BetterHelp.com
- Exclusive members-only content & publications
- Discounts on SCARS Self-Help Books Save
- And more!
To learn more about the SCARS STAR Membership visit membership.AgainstScams.org
To become a SCARS STAR Member right now visit join.AgainstScams.org
To Learn More Also Look At Our Article Catalogs
Scam & Crime Types
More SCARS
- ScamsNOW Magazine – ScamsNOW.com
- ContraEstafas.org
- ScammerPhotos.com
- AnyScam.com – reporting
- AgainstScams.org – SCARS Corporate Website
- SCARS YouTube Video Channel











![An Example of How Scammers Use Emergency Scams - 2014 [UPDATED 2024] - on SCARS RomanceScamsNOW.com](https://romancescamsnow.com/wp-content/uploads/2014/06/emergency-scams.png)

Please Leave A Comment - Tell Us What You Think About This!