According To Industry Sources, Cyber-Enabled Criminals Are Constantly Inventing New Attack Types
As scammers apply more institutional knowledge of the internet and online user’s behaviors they adapt their tactics. They are not giving up on the old techniques, but expanding to find more ways to scam victims – both individuals and corporations – from their money.
Here are the latest types of socially engineered scams running worldwide:
Social Engineering Against All Users
1: Browser Notification Hijack
Web sites have for several years asked visitors to approve “notifications” from the site. We do that on this website, but we use a reliable and secure partner to manage that (specifically OneSignal – an industry leader). Not all websites do use reliable partners – those that try to do it themselves can be vulnerable.
What was once a useful way to engage with readers and keep them up to date can be compromised and turned into a social engineering tool.
These are called push notifications, and they are valuable, but they can be weaponized on poorly managed websites. The problem is that many users blindly click ‘yes’ to allow these notifications. While many users have learned some level of caution with web browsers, the notifications appear more like system messages from the device itself, rather than the browser.
In our case, we offer that choice, but we also allow you to subscribe to our newsletter so you don’t have to use the push notifications- this is a safer alternative for most websites – unless they know what they are doing.
Once the cybercriminal has a user’s consent, they start inundating them with alert messages – and the messages are usually phishing schemes or scam notifications that contain malware.
Rule of thumb: if you receive more than a couple of alerts a day – you probably do not want their alerts anyway.
2: Deepfake Recordings
Social engineers are now using deepfakes – very realistic recordings that use artificial intelligence to simulate a specific person’s appearance or voice – to trick victims into divulging information or performing an action that benefits the scammer.
This means they can send better fake videos to victims of romance scams, etc. It also means they can fabricate fake adult intimate videos and photos for sextortion purposes with ease.
Audio deepfakes – in which the cybercriminal uses a “cloned” voice that is nearly indistinguishable from a real person’s voice to create a scam audio recording – are a real growing concern.
One of the earliest successful examples came in 2019, when a fake recording of a CEO’s voice was used to instruct an employee to immediately transfer money to an international account. The recording was left as a voicemail to the subordinate, who obeyed the fraudulent instructions and sent $243,000 to the attackers.
We are seeing criminals use deepfake recordings to company manipulate staff into sending money or offering up private information – only audio recordings so far, but Gerchow believes video deepfakes are just a matter of time. But these are also being used in other kinds of scams, such as romance scams.
Everyone needs to become much smarter and more knowledgeable fast.
3: Malicious QR Codes
QR code-related phishing fraud has become common in the last year.
QR codes – those machine-readable, black-and-white matrix codes arranged in a square – have become an increasingly popular way for companies to engage with consumers and deliver services in the midst of COVID-19. For example, many restaurants have ditched paper menus, and instead, allow patrons to scan a QR code with their smartphone. Similarly, many Girl Scouts posted QR codes for no-contact ordering and delivery of cookies this spring.
Here is the problem – you cannot see what web address the QR Code contains just by looking at it!
Many of the websites that QR codes send people to are operated by third-party vendors. When scanned, a malicious QR code can connect phones to a malicious destination – just like clicking on a bad link. Same concept; new wrapper.
QR Codes that appear on ads or other marketing material can offer everything from a menu, to access to a website, to a chance of winning an Xbox. Always look for a real web address and always be cautious. Only trust reliable sources.
4: Text fraud
Text messages have been a conduit for social engineering scams for a while, but texting tactics becoming very common and frequent.
A large portion of the population prefers communicating via text messages as opposed to the phone. People are now extremely used to communicating very confidential types of information via text and it comes with risks.
Because grocery and food delivery has grown in the last year, delivery-related scam texts are up. Other common lures include texts that promise information about COVID stimulus checks that link victims back to a website that looks like the IRS site and asks for sensitive personal information, such as a birth date and social security number.
If you get a questionable text, look at the sending number – have you seen it before? Do a quick search online and see what shows.
As with QR codes, victims simply have not developed the level of awareness and caution needed.
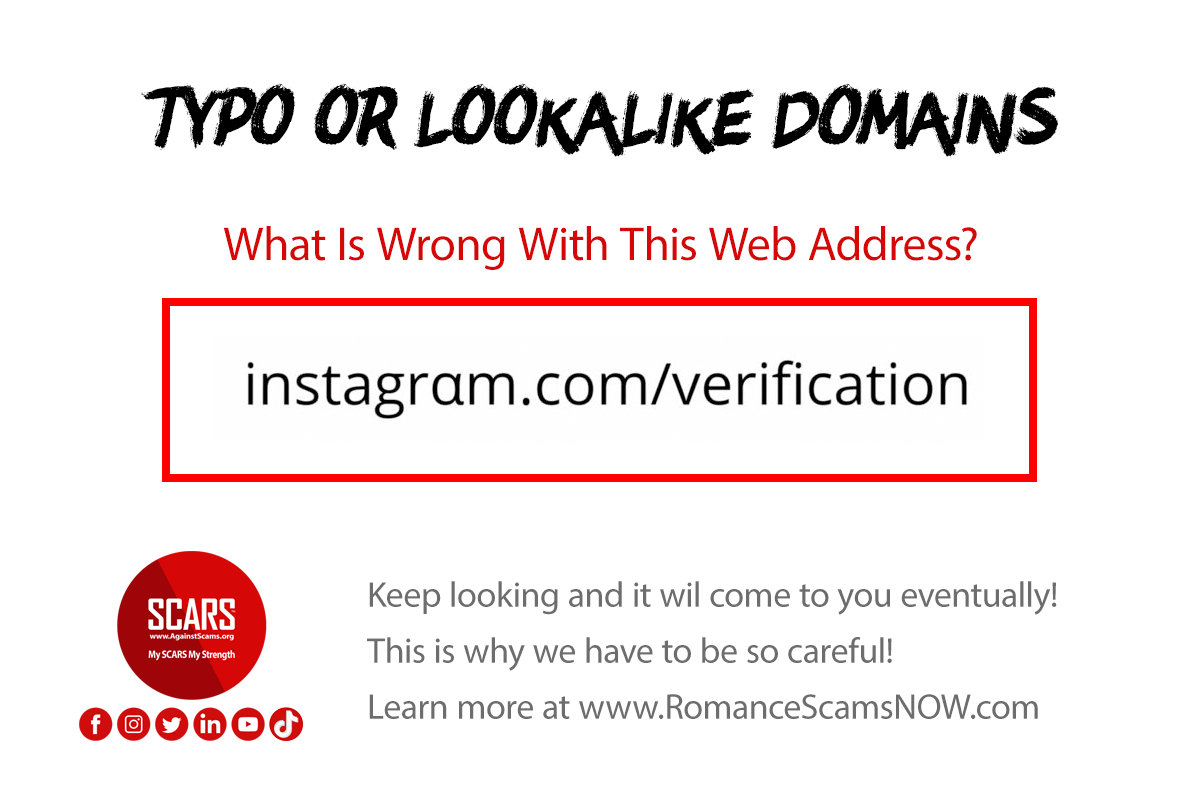
5: Typo-squatting or Lookalike Domains
This is actually not new but has become more sinister in the last year.
A Typo Domain uses common misspellings of a domain name that many people would naturally make. Mostly these have been used to gain ad exposures from people carelessly typing a web address. But increasingly they are used to fool victims in email addresses, or in directing unsuspecting victims to fake or malicious websites.
For example: think Gooogle instead of Google, or by adding a different top-level domain (.uk instead of .co.uk). Unlike the often sloppy versions from earlier days, today these sites may feature sophisticated designs, carefully detailed mimicry of legitimate sites, and sophisticated functionality.
Lookalike domains – are often served up in a business email compromise (BEC) attack. Fraudsters impersonate legitimate domains in order to fool victims into thinking they are in a safe location or that an email is legitimate.
We saw an example of this from a scammer in Australia that used the name of a government anti-scam agency called “ScamWatch” in a domain name to fool scam victims into believing they were dealing with the government investigators. They were asked to pay an investigation fee. SCARS has it shut down in 2019, but criminals persist in creating fake businesses.
A perfect example – can you see what is wrong in this web address?
Social engineering victims are usually tricked into either feeling psychological safety by their choice or into seeking psychological safety in a way that will play into a criminal’s hands.
Criminals set up these sites not only to deliver malware but also to capture credit card information or other sensitive data through fake login fields or other fake forms.
Social Engineering Against Businesses
1: Supply Chain Partner Impersonation
Attacks that exploit parts of an organization’s supply chain are now a big problem. This is basically a variation of BEC scams, but scammers now have more than enough money to understand real business processes.
It’s not easy to defend what you can’t see, and you are only as strong as the weakest link. For example, there have been many targeted emails coming in that look like they are from your trusted partners but are in fact bad actors posing as employees you may know within your network.
Always verify, verify, verify. Create a new email from the address in your contact list, or through your connection on LinkedIn. Do not just reply to a message you receive.
These attacks have become even more detailed and sophisticated over time. They will look and sound good.
We see these long, sophisticated attempts to build trust or relationships with a company’s outbound-facing teams whose entire job is to help.
By establishing these trusted relationships, the criminals’ ultimate goal is to make standard social engineering tactics more effective, eliciting help in bypassing security controls, or sending malware or gaining information that will compromise the target company’s systems.
The SolarWinds attack is an example of a supply chain attack – in that case, a specific version called a vendor email compromise attack (VEC) was used. As SolarWinds officials noted, an email account was compromised and used to programmatically access accounts of targeted SolarWinds personnel in business and technical roles.
2: Collaboration Scams
With this social engineering tactic, cybercriminals target professionals in collaborative fields, including designers, developers, and even security researchers. The lure is an invitation that asks them to collaborate on work via an app or website.
Recent pandemic lockdowns and expanded work-from-home increased people’s comfort with remote collaboration, so this tactic fit the times well.
The cybercriminal sends over a Visual Studio Project containing malicious code. The user runs the program, and their device is infected pretty quickly. This attack essentially exploits the desire or need to assist or help others with passion projects.
Obviously, you should never accept or open an email or other attachments from people that you do not know! And never run anything that can be executed on your computer.
These attacks are often well-crafted, showing great attention to detail – but especially for people that live on the web – they should know better!
Criminals posed as active researchers and built social proof documents – with apparent third parties validating their research – using a blog including articles from industry sources as ‘guest posts,’ Twitter accounts, YouTube videos, LinkedIn, Discord, and more, A suspicious victim may be put at ease by this seemingly wide social footprint. But like all things online, don’t trust anyone!
If someone wants to participate in research then do it through a known channel such as RsearchGate.
To Learn More Also Look At Our Article Catalogs
Scam & Crime Types
More SCARS
- ScamsNOW Magazine – ScamsNOW.com
- ContraEstafas.org
- ScammerPhotos.com
- AnyScam.com – reporting
- AgainstScams.org – SCARS Corporate Website
- SCARS YouTube Video Channel











Leave A Comment