How Do Scammers & Thieves Get You Personal & Financial Information?
A SCARS Insight
Scammers & Identity Thieves Are Not Stupid!
Scammers and Identity Thieve Steal the Information from Millions of Victims Every Year!
ACCORDING TO SOME REPORTS THERE IS A
1 OUT OF 2 CHANCE OF YOU BECOMING AN IDENTITY THEFT VICTIM
Identity theft occurs when someone fraudulently uses your personal information to obtain credit, take out a loan, open accounts, get identification or otherwise use your information in an unauthorized way. Estimates from the Federal Trade Commission suggest that identity theft is on the rise. In fact, identity theft is the fastest growing crime in the country—a crime that affects Coloradans and their credit histories.
Identity theft often tops the list of consumer fraud reports that are filed with the U.S. FTC and other enforcement agencies. While the FTC does not have criminal jurisdiction, it supports the criminal investigation and prosecution of identity theft by serving as a clearinghouse for identity theft reports, part of the FTC’s Consumer Sentinel report database.
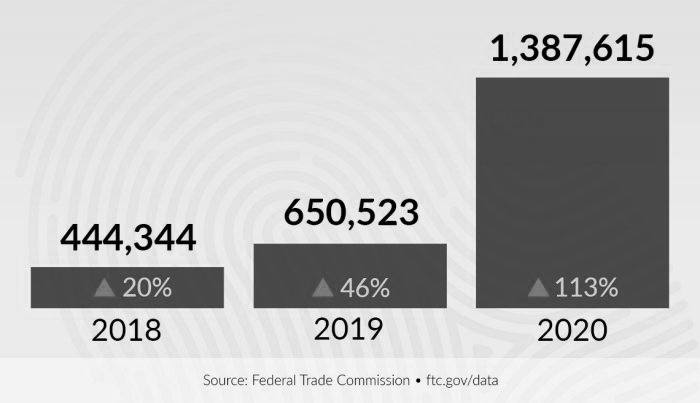
THE NUMBER OF IDENTITY THEFT CASES MORE THAN DOUBLED IN 2020 FROM 2019
How They Get Your Information
Here are some of the ways identity thieves steal your personal and financial information:
- Computer hackers “breaking into” business or personal computers to steal private files and personal financial information, commonly known as a data breach.
- Stealing your purse or wallet to obtain social security cards, credit cards, driver’s licenses, etc.
- Stealing mail being delivered to your home or left out for pick-up.
- Diverting your mail to another mailbox using a false “change-of-address” request.
- “Dumpster diving”— thieves dig through dumpsters or garbage cans behind homes or businesses looking for discarded checks or bank statements, credit card or other account bills, medical records, pre-approved credit applications, etc.
- “Shoulder surfing”— thieves watch over your shoulder as you enter your PIN into an ATM.
- “Pretext calls”— thieves call to “verify” account information or to “confirm” an enrollment or subscription by having you repeat bank or credit card account numbers.
- Using false or misleading Internet sites to collect personal and financial information.
- Purchasing personal information from unscrupulous employees at companies with which you do business.
- Burglarizing homes and businesses looking for purses, wallets, computers and digital devices, files containing personal and financial information.
- Phony e-mail or “pop-up” messages known as clickbait, phishing, and spam that appear to be from your credit card company, Internet Service Provider or other entity you do business with. These phony messages claim some problem with your account and direct you to another website where you will be asked to supply a credit card and other personal information or download malicious software or malware.
- ATM skimming involves the placement of a mechanical card reader over or into the actual card reader on an ATM machine. These fake card readers will capture your account number and possibly even your PIN code, which are then used to produce counterfeit credit or debit cards.
What Do They Want That Information For?
- Collect government benefits in your name by using your SSN or ID# to apply for a job or to obtain a tax return refund.
- Drain your bank account with electronic transfers, counterfeit checks, or your debit card.
- Open a bank or credit account in your name and write bad checks, make charges that never get paid off, which gets reflected on your credit report.
- Use your name if they get arrested or for conducting illegal activity such as drug purchases that could result in warrants being issued in your name or go on your permanent record.
- Obtain a driver’s license or a job with your personal information.
- Buy a car or property and use your information and credit history to get a loan for it.
- Obtain utility services in your name, such as phone or Internet.
Key Fraud Indications In 2020:
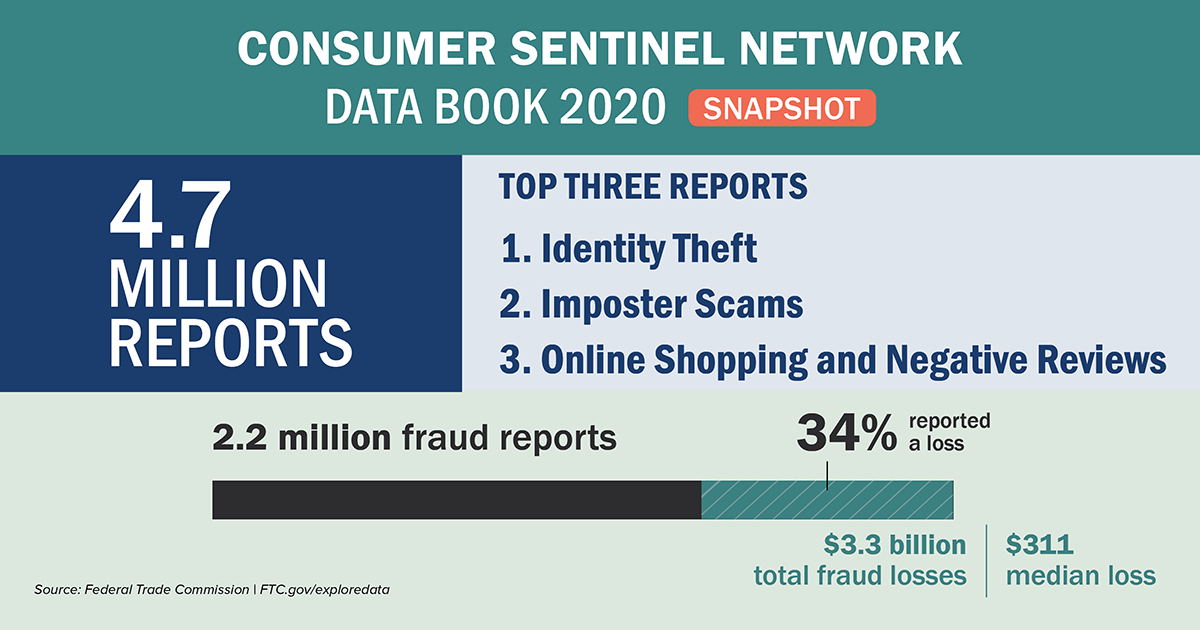
- There were 2.18 million reports of fraud, and impostor scams (meaning identity theft) were the most common type of fraud. Howevere, it is estimated that less that 5% of all victims every report these crimes.
- These involve criminals posing as others to steal money or personal information from victims.
- Frauds grew from 1.72 million reports in 2019, and year-over-year losses climbed to more than $3.3 billion in 2020 from $1.8 billion a year earlier. Consider that this may be less that 3% of the actual.
- Not everyone who reports fraud actually lost money: Only 18 percent of those age 80 and older said the fraud deprived them of assets. The elderly were largest average loss of any group at over $1,300.
- Average fraud losses were $635 for victims age 70 to 79; $436 for those 60 to 69; $325 for those 50 to 59; $278 for those 40 to 49; $250 for those 30 to 39; $324 for those 20 to 29; and $180 for those 19 and younger. Those below the age of 30 almost never report these crimes.
Who Is Most At Risk For Identity Theft?
Most identity thefts are crimes of opportunity. Identity thieves often target those who don’t regularly check for identity theft warning signs and are unlikely to report irregular activity on their credit reports.
CHILDREN AND SENIORS
Everyone with a Social Security number is at risk for identity theft, but two demographics are targeted aggressively and often: the very young and the very old.
- Children are targeted because identity thieves can use a child’s Social Security numbers to establish a fraudulent “clean slate.” Identity theft experts recommend parents monitor their children’s credit reports to check for identity theft as often as their own.
- Seniors are targeted most often over the telephone and through internet phishing scams. Some studies suggest that people become more trusting as they age, which explains why it’s more difficult for older adults to detect fraudsters.
THE MILITARY
While deployed, active-duty members of the armed services are particularly vulnerable to identity theft because they may not notice mistakes on their credit reports or receive calls from debt collectors regarding a fraudulent charge. According to FTC reports, military consumers are most affected by credit card and bank fraud.
- 2018 total military consumer credit card fraud reports: 10,590
- 2018 total military consumer bank fraud reports: 5,723
- Military consumers’ reports of employment or tax-related fraud increased by 85% between 2017 and 2018.
- Military members are also increasingly affected by loan or lease fraud.
2018 Military Consumer Loan Or Lease Fraud Reports
| Fraud type | Total reports | % Difference from previous year |
|---|---|---|
| Business/personal loan | 1,168 | +19% |
| Auto loan/lease | 832 | +40% |
| Real estate loan | 385 | +36% |
| Apartment or house rented | 380 | +79% |
| Non-federal student loan | 257 | +18% |
| Federal student loan | 192 | +22% |



SOCIAL MEDIA USERS
It’s relatively easy for cybercriminals to discover a person’s name, date of birth, phone number, hometown and other sensitive information through social media and networking sites. With this information, an identity thief can target victims for phishing and imposter scams.
REPEAT VICTIMS
People who have previously been affected by identity theft are at a greater risk for future identity theft and fraud. According to the Center for Victim Research, 7-10% of the U.S. population are victims of identity fraud each year, and 21% of those experience multiple incidents of identity fraud.
For more information about how victims of identity theft can protect themselves from future fraud, read about the identity theft recovery process.
THE DECEASED
Identity thieves can target the recently departed with information gleaned from public obituaries and access the deceased Social Security number through the Social Security Administration’s Master Death File. Stealing a dead person’s identity is commonly referred to as “ghosting.” Ghosting often goes unnoticed by surviving family members for months or years.