The Most Dangerous Malware EMOTET Disrupted Through Global Action
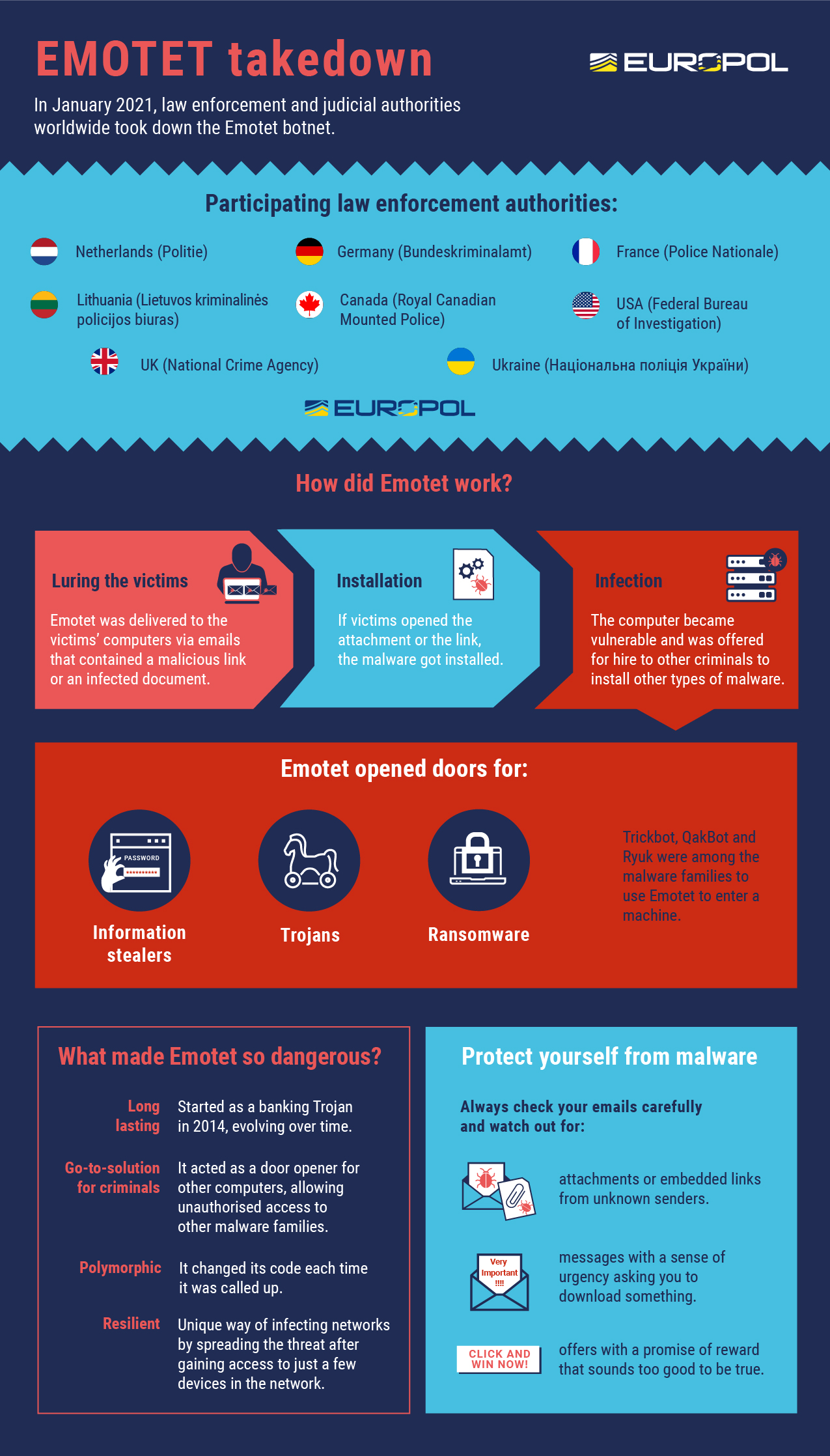
Law enforcement and judicial authorities worldwide have this week disrupted one of the most significant botnets of the past decade: EMOTET
Investigators have now taken control of its infrastructure in an international coordinated action!
EMOTET Has Been One Of The Most Professional And Long-Lasting Cybercrime Services Out There
First discovered as a banking Trojan Virus in 2014, the malware evolved into the go-to solution for cybercriminals over the years!
This operation is the result of a collaborative effort between authorities in the Netherlands, Germany, the United States, the United Kingdom, France, Lithuania, Canada, and Ukraine, with international activity coordinated by Europol and Eurojust. This operation was carried out in the framework of the European Multidisciplinary Platform Against Criminal Threats (EMPACT).
The EMOTET infrastructure essentially acted as a primary door opener for computer systems on a global scale.
Once this unauthorized access was established, these were sold to other top-level criminal groups to deploy further illicit activities such data theft and extortion through ransomware.
SPREAD VIA WORD DOCUMENTS
The EMOTET group managed to take email as an attack vector to the next level. Through a fully automated process, EMOTET malware was delivered to the victims’ computers via infected e-mail attachments. A variety of different lures were used to trick unsuspecting users into opening these malicious attachments. In the past, EMOTET email campaigns have also been presented as invoices, shipping notices, and information about COVID-19.
All these emails contained malicious Word documents, either attached to the email itself or downloadable by clicking on a link within the email itself. Once a user opened one of these documents, they could be prompted to “enable macros” so that the malicious code hidden in the Word file could run and install EMOTET malware on a victim’s computer.
ATTACKS FOR HIRE
EMOTET was much more than just malware. What made EMOTET so dangerous is that the malware was offered for hire to other cybercriminals to install other types of malware, such as banking Trojans or ransomware, onto a victim’s computer.
This type of attack is called a ‘loader’ operation, and EMOTET is said to be one of the biggest players in the cybercrime world as other malware operators like TrickBot and Ryuk have benefited from it.
Its unique way of infecting networks by spreading the threat laterally after gaining access to just a few devices in the network made it one of the most resilient malware in the wild.
Disruption of EMOTET’s Infrastructure
The infrastructure that was used by EMOTET involved several hundreds of servers located across the world, all of these having different functionalities in order to manage the computers of the infected victims, to spread to new ones, to serve other criminal groups, and to ultimately make the network more resilient against takedown attempts.
To severely disrupt the EMOTET infrastructure, law enforcement teamed up together to create an effective operational strategy. It resulted in this week’s action whereby law enforcement and judicial authorities gained control of the infrastructure and took it down from the inside. The infected machines of victims have been redirected towards this law enforcement-controlled infrastructure. This is a unique and new approach to effectively disrupt the activities of the facilitators of cybercrime.
How To Protect Oneself Against Loaders
Many botnets like EMOTET are polymorphic in nature. This means that the malware changes its code each time it is called up. Since many antivirus programs scan the computer for known malware codes, a code change may cause difficulties for its detection, allowing the infection to go initially undetected.
A combination of both updated cybersecurity tools (antivirus and operating systems) and cybersecurity awareness is essential to avoid falling victim to sophisticated botnets like EMOTET. Users should carefully check their email and avoid opening messages and especially attachments from unknown senders. If a message seems too good to be true, it likely is and emails that implore a sense of urgency should be avoided at all costs.
As part of the criminal investigation conducted by the Dutch National Police into EMOTET, a database containing e-mail addresses, usernames and passwords stolen by EMOTET was discovered. You can check if your e-mail address has been compromised. As part of the global remediation strategy, in order to initiate the notification of those affected and the cleaning up of the systems, information was distributed worldwide via the network of so-called Computer Emergency Response Teams (CERTs).
The Future
While this and other malware & cyber threats have not gone away forever, actions like this make us safer, but we must always be on our guard – every minute of the day! Cybercriminals never give up and they are after your data, your identity, and your money!
We recommend that you always have a malware security solution installed on your devices – SCARS suggests Malware Bytes
We also recommend that everyone learn the basics of cybersecurity. We suggest that you visit our SCARS Partner www.Wizer-Training.com for their free Cybersecurity training, plus use our free cybersecurity training here:
- Free Cybersecurity Awareness Training [Presentation / Slideshow] – SCARS™ Training
- Cybersecurity for Small Businesses – SCARS™ Guide
- Scams And Your Small Business – SCARS™ Guide
- Las Estafas y Su Pequeño Negocio – Información de SCARS|LATINOAMERICA™
Make Sure You Check
You can check if your e-mail address has been compromised here
The following Law Enforcement authorities took part in this operation:
- Europe: Europol
- Netherlands: National Police (Politie), National Public Prosecution Office (Landelijk Parket)
- Germany: Federal Criminal Police (Bundeskriminalamt), General Public Prosecutor’s Office Frankfurt/Main (Generalstaatsanwaltschaft)
- France: National Police (Police Nationale), Judicial Court of Paris (Tribunal Judiciaire de Paris)
- Lithuania: Lithuanian Criminal Police Bureau (Lietuvos kriminalinės policijos biuras), Prosecutor’s General’s Office of Lithuania
- Canada: Royal Canadian Mounted Police
- United States: Federal Bureau of Investigation, U.S. Department of Justice, US Attorney’s Office for the Middle District of North Carolina
- United Kingdom: National Crime Agency, Crown Prosecution Service
- Ukraine: National Police of Ukraine (Національна поліція України), of the Prosecutor General’s Office (Офіс Генерального прокурора)
TAGS: SCARS, Cybercrime, Crybercriminals, Cybercrime Victims, Online Crime Is Real Crime, Malware Avoidance, Ransomware, EMOTET, EMPACT, Europol, Botnet, Malware, Computer Virus, Email Compromise
PLEASE SHARE OUR ARTICLES WITH YOUR FRIENDS & FAMILY
HELP OTHERS STAY SAFE ONLINE – YOUR KNOWLEDGE CAN MAKE THE DIFFERENCE!
THE NEXT VICTIM MIGHT BE YOUR OWN FAMILY MEMBER OR BEST FRIEND!
By the SCARS™ Editorial Team
Society of Citizens Against Relationship Scams Inc.
A Worldwide Crime Victims Assistance & Crime Prevention Nonprofit Organization Headquartered In Miami Florida USA & Monterrey NL Mexico, with Partners In More Than 60 Countries
To Learn More, Volunteer, or Donate Visit: www.AgainstScams.org
Contact Us: Contact@AgainstScams.org




Leave A Comment