RSN™ Special Report: Europol Internet Organised Crime Threat Assessment (IOCTA) 2018
Europol Warns You Could Become A Cybercrime Victim
From ransomware through to cryptocurrency scams, Europol says it wants to stop criminals from making you a victim.
Europol has warned of 15 ways in which people can fall prey to cybercriminals as it launched a report on the dangers of the web.
The report, the fifth annual Internet Organised Crime Threat Assessment (IOCTA), is being presented at the Interpol cybercrime conference in Singapore.
Europol IOCTA 2018 Summary
For the fifth year in a row, Europol has produced the Internet Organised Crime Threat Assessment (IOCTA). The aim of this Assessment is to provide a comprehensive overview of the current, as well as anticipated future threats and trends of crimes conducted and/or facilitated online. While current events demonstrate how cybercrime continues to evolve, this year’s IOCTA shows us how law enforcement has to battle both innovative as well as persistent forms of cybercrime. Many areas of the report, therefore, build upon previous editions, which emphasizes the longevity of the many facets of cybercrime. It is also a testimony to an established cybercrime business model, where there is no need to change a successful modus operandi. The report also highlights the many challenges associated with the fight against cybercrime, both from a law enforcement and, where applicable, a private sector perspective.
Europol described the report as offering “a unique law enforcement view of the emerging threats and key developments in the field of cybercrime over the last year.”
It added that the assessment “describes anticipated future threats” and “only has one goal in mind – to stop cybercriminals from making you their next victim.”
Crime Priorities
Crime Priority: Cyber-Dependent Crime
Cyber-dependent crime can be defined as any crime that can only be committed using computers, computer networks or other forms of information communication technology (ICT). In essence, without the internet criminals could not commit these crimes. It includes such activity as the creation and spread of malware, hacking to steal sensitive personal or industry data and denial of service attacks to cause financial and/or reputational damage.
Key Findings
- Ransomware remains the key malware threat in both law enforcement and industry reporting.
- Cryptomining malware is expected to become a regular, low-risk revenue stream for cybercriminals.
- The use of exploit kits (EKs) as a means of infection continues to decline, with spam, social engineering and newer methods such as RDP brute-forcing coming to the fore.
- New legislation relating to data breaches will likely lead to greater reporting of breaches to law enforcement and increasing cases of cyber-extortion.
Crime Priority: Child Sexual Exploitation Online
Online child sexual exploitation (CSE) continues to be the worst aspect of cybercrime. Whereas child sexual abuse existed before the advent of the internet, the online dimension of this crime has enabled offenders to interact with each other online and obtain Child Sexual Exploitation Material (CSEM) in volumes that were unimaginable ten years ago. The growing number of increasingly younger children with access to Internet-enabled devices and social media enables offenders to reach out to children in ways that are simply impossible in an offline environment. This trend has considerable implications for the modi operandi in the online sexual exploitation of children.
Key Findings
- The amount of detected online Child Sexual Exploitation Material continues to grow, creating serious challenges for investigations and victim identification efforts.
- As technologies are becoming easier to access and use, the use of anonymization and encryption tools by offenders to avoid law enforcement detection is more and more common.
- Children increasingly have access to the internet and social media platforms at a younger age, resulting in a growing number of cases of online sexual coercion and extortion of minors.
- Live streaming of child sexual abuse remains a particularly complex crime to investigate. Streaming of self-generated material has significantly increased.
Crime Priority: Payment Fraud
Payment fraud which are considered well known as they have been reported on in previous editions as well as new developments in the area of payment fraud. New is a relative concept since criminals generally vary their existing modus operandi. Such variations, however, do introduce different threats. Therefore, well-known and new developments are included in a complementary manner, based both on what law enforcement agencies have witnessed in their investigations as well as what private sector parties have observed.
Key Findings
- The threat from skimming continues and shall do as long as payment cards with magnetic stripes continue to be used.
- The abuse of PoS terminals is taking on new forms: from manipulation of devices to the fraudulent acquisition of new terminals.
- Telecommunications fraud is a well-established crime but a new challenge for law enforcement.
Crime Priority: Online Criminal Markets
Illicit online markets, both on the surface web and on the dark web, provide criminal vendors the opportunity to purvey all manner of illicit commodities, with those of a more serious nature typically found deeper, in the dark web. Many of these illicit goods and services, such as cybercrime toolkits or fake documents, are enablers for further criminality.
Key Findings
- The Darknet market ecosystem is extremely unstable. While law enforcement shut down three major marketplaces in 2017, at least nine more spontaneously closed or exit scammed.
- The almost inevitable closure of large, global Darknet marketplaces has led to an increase in the number of smaller vendor shops and secondary markets catering to specific language groups or nationalities.
The Convergence Of Cyber And Terrorism
The Islamic State’s (IS) loss of territory from 2016 to 2017 did not equate to a loss of authority among its followers or a manifest decrease in its ability to inspire attacks. Instead, the group continues to use the internet to promote its doctrine and inspire acts of terrorism. In many ways, military defeat has made the internet even more important for the IS; the difference being that it has since shifted from using it to support its state-building ambitions toward inspiring and attempting to direct terrorist attacks in the West.
Key Findings
- Islamic State continues to use the internet to spread propaganda and to inspire acts of terrorism.
- Law enforcement and industry action has pushed IS sympathizers into using encrypted messaging apps which offer private and closed chat groups, the dark web, or other platforms which are less able or willing to disrupt their activity.
- While IS sympathizers have demonstrated their willingness to buy cyber-attack tools and services from the digital underground, their own internal capability appears limited.
Cross-Cutting Crime Factors
Cross-cutting crime factors are those which impact, facilitate or otherwise contribute to multiple crime areas but are not necessarily inherently criminal themselves. This includes topics such as methods of communication, financing, encryption, IoT and social engineering.
Key Findings
- West African fraudsters have evolved to adopt emerging fraud techniques, including those with more sophisticated, technical aspects, such as business email compromise.
- Phishing continues to increase and remains the primary form of social engineering. Although only a small proportion of victims click on the bait, one successful attempt can be enough to compromise a whole organization.
- Many of the classic scams, such as technical support scams, advanced fee fraud, and romance scams still result in a considerable number of victims.
- An increase in HTTPS encryption protocol by phishing sites misleads victims into thinking a website is legitimate and secure.
- Cyber-attacks which historically targeted traditional financial instruments are now targeting businesses and users of cryptocurrencies.
- While Bitcoin’s share of the cryptocurrency market is shrinking, it still remains the predominant cryptocurrency encountered in cybercrime investigations.
- A combination of legislative and technological developments, such as 5G and the redaction of WHOIS, will significantly inhibit suspect attribution and location for law enforcement and security researchers.
Regular Cybercrimes
Ransomware
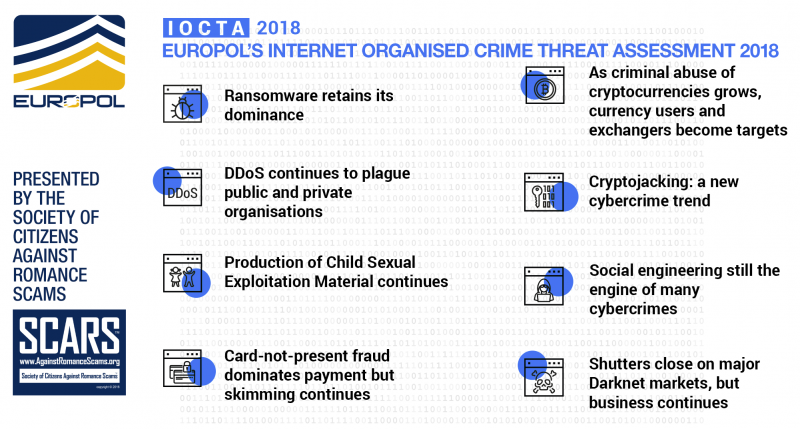
Ransomware Retains Its Dominance
Ransomware – malicious software that encrypts your computer and demands a ransom to make the files accessible – has become a standard attack tool for cybercriminals.
Europol is warning that criminals are moving from random ransomware attacks, such as the WannaCry attack which hit the NHS, to specifically targeting companies and individuals who might be able to pay larger ransoms.
How to protect yourself?
- Keep your computer updated
- Use a reputable anti-virus program
Even though the growth of ransomware is beginning to slow, ransomware is still overtaking banking Trojans in financially-motivated malware attacks, a trend anticipated to continue over the following years. In addition to attacks by financially motivated criminals, significant, public reporting increasingly attributes global cyber-attacks to the actions of nation states. Mobile malware has not been extensively reported in 2017, but this has been identified as an anticipated future threat for private and public entities alike.
Illegal acquisition of data following data breaches is a prominent threat. Criminals often use the obtained data to facilitate further criminal activity. In 2017, the biggest data breach concerned Equifax, affecting more than 100 million credit users worldwide. With the EU GDPR coming into effect in May 2018, the reporting of data breaches is now a legal requirement across the EU, bringing with it hefty fines and new threats and challenges.
Mobile malware
Europol warns that malware for mobile phones is likely to grow as people shift from online to mobile banking.
How to protect yourself?
- Check apps are legitimate before installing them
- Use a reputable mobile anti-virus program
PC Malware
Europol warns that cyber attacks have become increasingly stealthy and harder to detect.
Attacks using so-called “fileless” malware are increasingly common. This malware doesn’t write itself onto the victim computer’s hard drive, but only exists in parts of the computer memory, such as the RAM
How to protect yourself?
- Keep your computer software updated.
- Be wary of using macros in office programs.
Online Extortion
The EU’s new General Data Protection Regulation (GDPR) introduces severe financial sanctions, up to 4% of global turnover, for companies that fail to protect users’ privacy.
GDPR requires that data breaches are reported within 72 hours, and Europol warns that criminals may try to extort organizations because of this.
“While this is not new, it is possible that hacked companies will prefer to pay a smaller ransom to a hacker for non-disclosure than the steep fine that might be imposed by the authorities.”
How to protect yourself?
- Never pay extortion attempts without contacting the authorities first
Data Theft For Data’s Sake
Europol warns that the motive behind a lot of network intrusions is the illegal acquisition of data.
This data could be used for a variety of purposes, from developing leads for phishing or payment fraud, through to commercial or industrial espionage.
How to protect yourself?
- Keep your computer updated
- Use a reputable anti-virus program
DDoS – Distributed Denial of Service – Website Attacks
DDoS Continues To Plague Public And Private Organizations
Distributed Denial of Service (DDoS) attacks are very unsophisticated and involve sending so many requests to a network resource that it is overloaded and can’t respond to any of them.
There are tools widely available allowing unskilled individuals to launch these attacks, and there are limited ways to protect against them because of the way the internet is engineered.
Fortunately, DDoS attacks can’t steal data or cause any damage beyond making a website or internet resource unavailable.
Criminals continue to use Distributed-Denial-of-Service (DDoS) attacks as a tool against private business and the public sector. Such attacks are used not only for financial gains but for an ideological, political or purely malicious reason. This type of attack is not only one of the most frequent (only second to malware in 2017); it is also becoming more accessible, low-cost and low-risk.
The “Darknet”
Shutters Close On Major Darknet Markets, But Business Continues
Europol says that offenders are continuously seeking new ways to avoid detection from law enforcement, including by using anonymization and encryption tools – and in some cases even the Bitcoin blockchain.
Almost all of this material is available on the open internet, but the very extreme material can be found on hidden services that can only be accessed on the “Darknet” according to Europol.
How will they catch these criminals?
The widespread use of encryption on the web today has repeatedly been described as an issue for law enforcement, security, and intelligence agencies.
According to a report by Parliament’s Security and Intelligence Committee, in 2016 GCHQ was engaged in a major ongoing project called FOXTROT, which was designed “to increase GCHQ’s ability to operate in an environment of ubiquitous encryption”.
The Darknet will continue to facilitate online criminal markets, where criminals sell illicit products in order to engage in other criminal activity or avoid surface net traceability. In 2017, law enforcement agencies shut down three of the largest Darknet markets: AlphaBay, Hansa and RAMP. These takedowns prompted the migration of users towards existing or newly-established markets, or to other platforms entirely, such as encrypted communications apps.
Although cybercrime continues to be a major threat to the EU, last year again saw some remarkable law enforcement success. Cooperation between law enforcement agencies, private industry, the financial sector, and academia is a key element of this success.
Social Control
Social Engineering
Social Engineering Still The Engine Of Many Cybercrimes
Social engineering describes a form of attack in which someone exploits human traits, such as kindness or compassion, as part of a cyber attack. The famous Nigerian prince scams are a form of social engineering fraud.
Europol warns that West African fraudsters are likely to have a more significant role within the EU in the future, as Africa continues to have the fastest growing internet usage globally.
How to protect yourself?
- Always remember that if it seems to good to be true, it probably is.
The significance of social engineering for cyber-dependent and cyber-enabled crime continues to grow. Phishing remains the most frequent form of social engineering, with vishing and smishing less common. Criminals use social engineering to achieve a range of goals: to obtain personal data, hijack accounts, steal identities, initiate illegitimate payments, or convince the victim to proceed with any other action against their self-interest, such as transferring money or sharing personal data.
Live Streaming
Live streaming of child sexual abuse is a very difficult crime to investigate. Europol states: “It often leaves few forensic traces and the live streamed material does not need to be downloaded or locally stored.”
It has been on the rise for some years as video streaming technology has improved.
This form of abuse “will most likely move to other parts of the world, where legislation and law enforcement are not always able to keep up with the rapid developments in this area,” warns Europol.
How to tackle it?
- Internet businesses currently use the Child Abuse Image Database, which contains 30 million cryptographic hashes (digital fingerprints that can be used to identify files) to automatically detect when someone attempts to upload a known indecent image to their platforms.
- However, this form of filtering is unable to capture new indecent images that haven’t been reported before – nor can it address child abuse material which is being streamed.
Sajid Javid, the U.K. home secretary, has pledged £250,000 towards the development of technologies which can detect live-streamed abuse.
Cryptocurrency Based
Cryptocriminality
Cryptojacking: A New Cybercrime Trend
There is a range of cryptocurrency crimes taking place, according to Europol, and cyber attacks which historically targeted financial instruments are now targeting cryptocurrency users and businesses.
Cryptomining has been exploited by financially motivated cybercriminals, who for instance hack legitimate websites to cryptojack users visiting those sites – hijacking their CPU power to mine more of the currency.
How to protect yourself?
- Use a legitimate browser plug-in to avoid running javascript on unfamiliar web pages.
Cryptojacking is an emerging cybercrime trend, referring to the exploitation of internet users’ bandwidth and processing power to mine cryptocurrencies. While it is not illegal in some cases, it nonetheless creates additional revenue streams and therefore motivation for attackers to hack legitimate websites to exploit their visitor systems. Actual cryptomining malware works to the same effect but can cripple a victims system by monopolizing their processing power.
Privacy-Oriented Cryptocurrencies
As Criminal Abuse Of Cryptocurrencies Grows, Currency Users And Exchangers Become Targets
Europol states that it expects “a more pronounced shift towards more privacy-oriented currencies” and said “an increase in extortion demands and ransomware in these currencies will exemplify this shift”.
How to protect yourself?
- Report all extortion attempts to the authorities
- Keep your software updated to avoid ransomware
Previous reports indicated that criminals increasingly abuse cryptocurrencies for funding criminal activities. While Bitcoin has lost its majority of the overall cryptocurrency market share, it still remains the primary cryptocurrency encountered by law enforcement. In a trend mirroring attacks on banks and their customers, cryptocurrency users and facilitators have become a victim of cybercrimes themselves. Currency exchangers, mining services and other wallet holders are facing hacking attempts as well as extortion of personal data and theft. Money launderers have evolved to use cryptocurrencies in their operations and are increasingly facilitated by new developments such as decentralized exchanges which allow exchanges without any Know Your Customer requirements. It is likely that high-privacy cryptocurrencies will make the current mixing services and tumblers obsolete.
Online Child Abuse
Volume Of Child Abuse Material
Production Of CSEM Continues
The volume of child sexual abuse is growing to levels “that were unimaginable ten years ago” according to Europol, “partly because of the growing number of young children with access to Internet-enabled devices and social media”.
How to react?
- Seeing images and videos of child sexual abuse can be upsetting, but the right thing to do is report it to the Internet Watch Foundation here.
- Your report could lead to the rescue of a young victim from further abuse.
The amount of detected online Child Sexual Exploitation Material (CSEM), including Self-Generated Explicit Material (SGEM), continues to increase. Although most CSEM is still shared through P2P platforms, the more extreme material is increasingly found on the Darknet. Meanwhile, Live Distant Child Abuse (LDCA), facilitated by growing internet connectivity worldwide, continues to be a particularly complex form of online CSE to investigate due to the technologies and jurisdictions involved.
As increasing numbers of young children have access to the internet and social media platforms, the risk of online sexual coercion and extortion continues to rise. The popularity of social media applications with embedded streaming possibilities has resulted in a strong increase in the amount of SGEM live streamed on these platforms.
Self-Generated Material
A large amount of child sexual exploitation material is self-generated. These images are often initially produced and shared voluntarily by young people, but end up in the hands of online child sex offenders. Offenders have also obtained images through sexual extortion.
How to protect yourself and others?
- Educate children about the risks of sharing nude images online and encourage them to report any harassment or extortion attempts to a responsible adult.
Money Fraud
Credit / Debit Card Skimming
Card-Not-Present Fraud Dominates Payment But Skimming Continues
Credit card skimming is still successful as magnetic stripes on cards continue to be used. The presence of cameras alongside chip and pin skimmers can also allow criminals to capture the PIN alongside their attempts to clone the chip.
How to protect yourself?
- Check instant payments on your banking app to be aware of fraud attempts
- Make sure you cover your PIN when at an ATM
Skimming remains a common issue in most of the EU Member States. As in previous years, this continues to decrease as a result of geoblocking measures. Skimmed card data is often sold via the Darknet and cashed out in areas where Europay, MasterCard, and Visa (EMV) implementation is either slow or non-existent.
Toll fraud has received a considerable amount of attention this year, with criminal groups using counterfeit fuel and credit/debit cards to avoid paying toll fees. Many Member States also reported an increase in the creation of fake companies to access and abuse Points of Sale (PoS), as well as profit from the compromised information. Meanwhile, CNP fraud continues to be a key threat for EU Member States, with the transport and retail sectors highlighted as key targets within the EU.
Phone Scams
Telecommunications Fraud
Fraudsters on the phone is an old but growing trend in fraud involving non-cash payments. Fraudsters can pretend to be from financial institutions or banks when attempting to collect details from you.
How to protect yourself?
- Never hand out financial information, including card details, over the phone
- Always double-check that someone claiming to be a representative from your bank is a real person, and call them back on a publicly listed number
Summary
Europol’s executive director Catherine De Bolle said: “Cybercrime cases are increasingly complex and sophisticated.
- “Law enforcement requires additional training, investigative and forensic resources in order to adequately deal with these challenges.
- “The policing opportunities arising from emerging technologies, such as big data analytics and machine learning, need to be seized.
- “Europol will continue its efforts to enhance cooperation with international law enforcement and government agencies, tech companies, academia, and other relevant stakeholders. Only if we do this, can cybercrime be combated effectively.”
- The European commissioner for the security union, Sir Julian King, concluded: “As the report shows, Europe is still faced with a range of security threats from terrorism and cyber.
- “We will continue to take decisive action, with the support of Europol, to tackle these threats, through our proposals on terrorist content online, electronic evidence and on election security, and through our cybersecurity strategy.”
Full IOCTA 2018 Report
Click Here For The Full IOCTA 2018 Report PDF File »
END
WESTERN UNION REPAYMENT PROGRAM NEWS
FOR THE LATEST INFORMATION ABOUT THE WESTERN UNION REPAYMENT / REMISSION PROGRAM CLICK HERE – IT IS STILL OPEN FOR A PETITIONS FOR REPAYMENT
– – –
Tell us about your experiences with Romance Scammers in our Scams Discussion Forum on Facebook »
FAQ: How Do You Properly Report Scammers?
It is essential that law enforcement knows about scams & scammers, even though there is nothing (in most cases) that they can do.
Always report scams involving money lost or where you received money to:
- Local Police – ask them to take an “informational” police report – say you need it for your insurance
- Your National Police or FBI (www.IC3.gov)
- The Scars Worldwide Reporting Network HERE or on www.Anyscam.com
This helps your government understand the problem, and allows law enforcement to add scammers on watch lists worldwide.
Visit our NEW Main SCARS™ News & Information Facebook page for much more information about scams and online crime: www.facebook.com/SCARS.News.And.Information
To learn more about SCARS visit www.AgainstScams.org
Please be sure to report all scammers HERE or on www.Anyscam.com
All original content is Copyright © 1991 – 2018 SCARS All Rights Reserved Worldwide & Webwide – RSN/Romance Scams Now & SCARS/Society of Citizens Against Romance Scams are all trademarks of Society of Citizens Against Romance Scams Inc.
Reporting Scammers, Arrest Scammers, AVOID SCAMS, ROMANCE SCAMS, NIGERIAN SCAMMERS, ROMANCE SCAMS NOW, GHANA SCAMMERS, FAKE PROFILES, FACEBOOK SCAMMERS, BOYCOTT AFRICAN COFFEE




Please Leave A Comment - Tell Us What You Think About This!