Why Does Facebook & Social Media Largely Ignore Scammers? Section 230 Is The Answer!
Originally published in 2015
This Simple Answer Is Because They Can – A Get Away With It!
In the early days of the web, there was a problem, and in typical fashion, a new law – the Communications Decency Act including Section 230 was created to solve it. However, 25 years later, the solution was worse than the problem. The law’s section 230 almost forces all web platforms and publishers to ignore the abuses from criminals and they get away with it because it also gives them immunity from liability!
Under the Trump Administration, real progress was being made on revising the problem section 230, but that was forgotten under the Biden Admin., and in fact, Presidential Orders changing the focus were all rescinded when Biden took office. We do not expect any change to section 230 until after the new 2022 Congress takes office.
You will note that we are quite critical of the Obama/Biden administrations simply because the opportunities to resolve the terrible wrongs that take place on the internet were lost and section 230 remains unchanged.
United States Law Ruled The Internet
(or did until Obama gave the internet away in 2017)
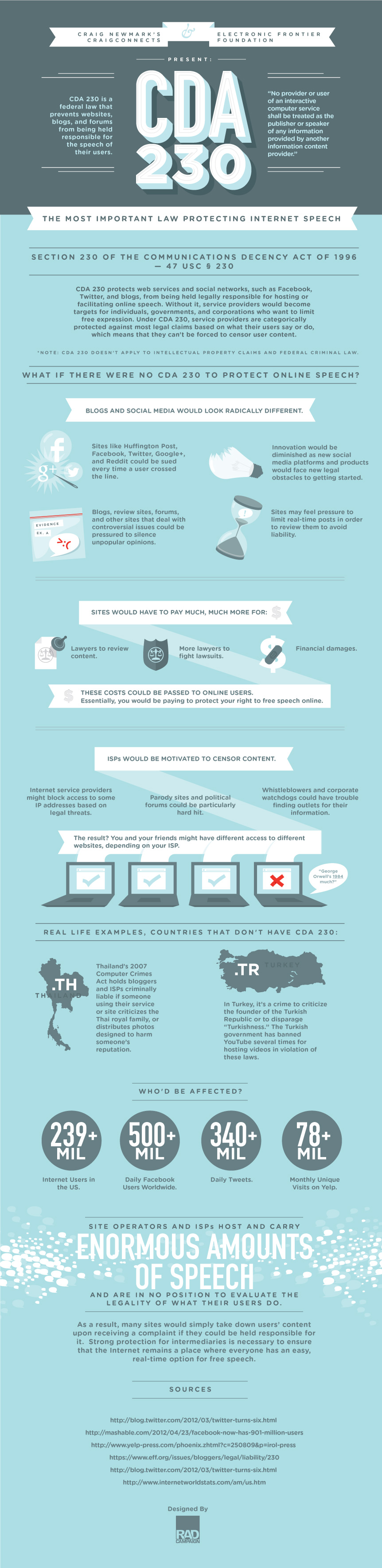
One of these laws is 47 U.S.C. Section 230, a Provision of the Communication Decency Act
All of us in the Internet industry in those days (which included our Managing Director who was a co-founder of TigerDirect.com – the largest internet retailer at that time) were looking for ways to allow our site visitors to comment and participate on our websites. We were all scared of what people were posting on our websites, chat services, and incipient social network services (such as ICQ and America Online). A solution was needed, but like with all solutions there are unforeseen consequences. Section 230 of the CDA became that solution and the curse.
The provisions of the Communications Decency Act (CDA) of 1996 were designed to allow the Internet to grow and prosper.
Tucked inside the Communications Decency Act (CDA) is one of the most valuable tools for protecting freedom of expression and innovation on the Internet: Section 230.
This comes somewhat as a surprise since the original purpose of the legislation was to restrict free speech on the Internet. The Internet community as a whole objected strongly to the Communications Decency Act, and with EFF’s (Electronic Freedom Foundation) help, the anti-free speech provisions were struck down by the Supreme Court. But thankfully, CDA Section 230 remains and in the years since has far outshone the rest of the law. But sometimes there are unforeseen consequences.
Section 230 says that “No provider or user of an interactive computer service shall be treated as the publisher or speaker of any information provided by another information content provider” (47 U.S.C. § 230). In other words, online intermediaries that host or republish speech are protected against a range of laws that might otherwise be used to hold them legally responsible for what others say and do. The protected intermediaries include not only regular Internet Service Providers (ISPs), but also a range of “interactive computer service providers,” including basically any online service that publishes third-party content. Though there are important exceptions for certain criminal, intellectual property-based claims, identity theft & impersonation, and defamation, the CDA section 230 creates a broad protection that has allowed innovation and free speech online to flourish.
This legal and policy framework has allowed for YouTube and Vimeo users to upload their own videos, Amazon and Yelp to offer countless user reviews, craigslist to host classified ads, and Facebook and Twitter to offer social networking to more than a billion Internet users.
Given the sheer size of user-generated websites (for example, Facebook alone has more than 1 billion users, and YouTube users upload more than 100 hours of video every minute), it would be infeasible for online intermediaries to prevent objectionable content from cropping up on their site.
Rather than face potential liability for their users’ actions, most would likely not host any user content at all or would need to protect themselves by being actively engaged in censoring what we say, what we see, and what we do online. In short, CDA 230 is perhaps the most influential law to protect the kind of innovation that has allowed the Internet to thrive since 1996.
However, it has a dark side too! (Enter the scammers, the haters, the defamers, fake news, and the terrorists!) Because these people use this loophole to exploit what and who they want.
The good news is that there are laws against that behavior too.
- Haters and defamers can be sued and stripped of their money and assets.
- Terrorists and criminals can be discovered and in many cases arrested in the more developed countries.
But scammers have flourished even though arrested continue to rise year after year.
Why? Because the flip side of the law (specifically section 230) is that websites and social media companies act like the three monkeys: See No Evil, Hear No Evil, Speak No Evil. So if they don’t look, they are not liable.
They have had their lawyers establish Community Standards, Terms, Conditions, and Policies that protect them at all costs, and sometimes even the consumer. However, it means that anything wrong has to be reported. Just one problem in this “live happily ever after” world of legal fiction – the ability of consumers to report and be heard by these websites and social media networks is that the platforms can selectively decide what they hear thanks to section 230.
Facebook especially is massively deficient in the training of their Standards Checking Personnel to the point that they don’t recognize scammers when they see them, and Facebook doesn’t even use basic technology to check the IP addresses of profile creators and editors to match where they say they live. It is for these reasons that the Society has created the SCARS Plan to help Facebook and others understand their weakness and what could even be called culpable negligence, and simple remedies to resolve a significant number of these problems rapidly.
Now that you know why Social Media and websites behave this way, what will you do to help change their minds? We would love to hear your opinions!
Where Do We Go Front Here?
Basically, the CDA needs an overhaul. SCARS has developed a change that addresses the real needs while retaining the value of the CDA. You can see it here!
However, until there is a willing Congress and a concerned public we will see no change!
Remember, that you have a dog in this fight! So act like it matters, because it does!
Section 230 Infographic
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment below!
Do You Need Support?
Get It Now!
SCARS provides the leading Support & Recovery program for relationship scam victims – completely FREE!
Our managed peer support groups allow victims to talk to other survivors and recover in the most experienced environment possible, for as long as they need. Recovery takes as long as it takes – we put no limits on our support!
SCARS is the most trusted support & education provider in the world. Our team is certified in trauma-informed care, grief counseling, and so much more!
To apply to join our groups visit support.AgainstScams.org
We also offer separate support groups for family & friends too.
Become a
SCARS STAR™ Member
SCARS offers memberships in our STAR program, which includes many benefits for a very low annual membership fee!
SCARS STAR Membership benefits include:
- FREE Counseling or Therapy Benefit from our partner BetterHelp.com
- Exclusive members-only content & publications
- Discounts on SCARS Self-Help Books Save
- And more!
To learn more about the SCARS STAR Membership visit membership.AgainstScams.org
To become a SCARS STAR Member right now visit join.AgainstScams.org
To Learn More Also Look At Our Article Catalogs
Scam & Crime Types
More SCARS
- ScamsNOW Magazine – ScamsNOW.com
- ContraEstafas.org
- ScammerPhotos.com
- AnyScam.com – reporting
- AgainstScams.org – SCARS Corporate Website
- SCARS YouTube Video Channel













Yes all guys with the last name Becerra are scammers
People should be aware of the names of scammers,should be posted all over Facebook,television,radio so they will be discourage to scam women in all over Canada,the U S.Most of this Scammers are from Nigeria,India,Malaysia,UK and every part of the World its a virus that is affecting the World.Why??????
THEY ARE IF PEOPLE REPORT THEM – SCAMMERS REPORTED ON OUR WEBSITE ARE DISTRIBUTED THROUGH THE SCARS ANTI-SCAM DATA REPORTING NETWORK