
SCARS Institute’s Encyclopedia of Scams™ Published Continuously for 25 Years

Evil Corp. – A Russian Organized Crime Group – Overview
Evil Corp (aka Indrik Spider) a Major Russian Cybercriminal Organization
Organized Crime – A SCARS Institute Insight
Authors:
• SCARS Institute Encyclopedia of Scams Editorial Team – Society of Citizens Against Relationship Scams Inc.
• Portions from the UK National Crime Agency
Article Abstract
Evil Corp, also known as Indrik Spider, is a notorious Russian cybercrime organization led by Maksim Yakubets. Originating as a family-centered operation in Moscow, the group became one of the most pervasive and sophisticated cybercrime adversaries, primarily engaging in financial crimes through malware and ransomware.
Over time, Evil Corp built close ties with Russian intelligence services, conducting cyber-attacks and espionage operations on behalf of the state. Despite facing sanctions and indictments from the US and UK in 2019, Evil Corp adapted by diversifying its tactics, including deploying new ransomware strains like WastedLocker and affiliating with LockBit. Government action in 2024 further exposed and disrupted the group’s ongoing activities.

Evil Corp (aka Indrik Spider) a Major Russian Cybercriminal Organization
Who is Evil Corp?
Evil Corp (also known as Indrik Spider) originated in Russia and is the most pervasive cybercrime group to ever have operated. Maksim Yakubets, who also goes by the online alias ‘Aqua’ and has a $5 million bounty for his arrest, was Evil Corp’s founder and led the group for the majority of its lifespan.
One of the first major financial cybercrime groups, Evil Corp. developed a series of malware and ransomware strains that have caused significant harm to numerous organizations and sectors, including healthcare, critical national infrastructure, and government.
Several law enforcement and government operations have taken place to disrupt the group since its formation, most notably in the form of sanctions and indictments in December 2019. As a result, the group has been forced to scrap its modus operandi and attempt new tactics to evade the additional scrutiny
and restrictions put on them.
Characterized by their longevity, adaptability, organizational hierarchy, and close links with the Russian state, Evil Corp. has proved a persistent threat for over a decade, and members continue to operate within the Russian Federation. However, since late-2019, their success and influence in the cybercrime ecosystem
have dwindled.
This is based on a UK National Crime Agency paper that provides a high-level overview of the group’s origins, operations, and evolution.
The Evil Corp Group
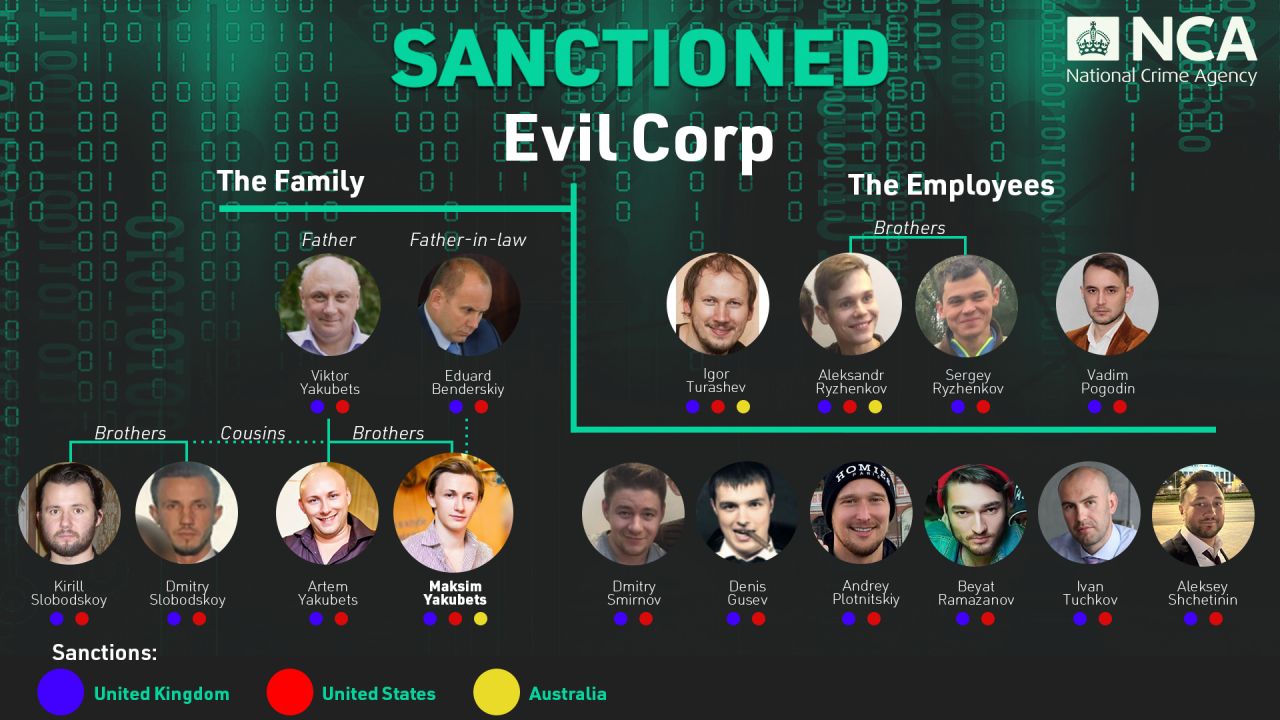
The majority of organized cybercrime groups operate predominately online, but Maksim Yakubets’ Evil Corp was a more personal affair: a family-centered operation based in Moscow, reminiscent of a traditional organized crime gang.
The Yakubets family were no strangers to financial crime: Viktor Yakubets, father of Maksim, had significant historical ties to money laundering activity. Maksim took this family business into the 21st century, branching into cybercrime and bringing his father, brother (Artem), and cousins (Kirill and Dmitry Slobodskoy) along with him.
By drawing on this family knowledge, Evil Corp became experts in laundering the proceeds of their cybercriminal activities.
Highly organized, a huge amount of resources was invested in professionalizing their business, whether that be by managing money mule networks, cryptocurrency trading, setting up front companies or employing lawyers. Although their technical capabilities were advanced, it was arguably their ability to realize the proceeds of their cybercrime that made them so successful.
At their peak, Evil Corp was a tight-knit group, operating out of physical office locations in Moscow (including Chianti Café and Scenario Café), and spending a lot of time socializing together, along with their wives and girlfriends. They even went on group holidays.
Maksim was the leader of the group, making all of the important decisions and keeping a firm grip on their activities. He was careful about exposing different group members to different areas of the business, even keeping details of his work secret from his wife.
However, he clearly placed a lot of trust in his long-term associate and second-in-command, Aleksandr Ryzhenkov. Yakubets started working with Ryzhenkov around 2013 whilst they were both still involved in The Business Club. The partnership endured, and they worked together on a number of Evil Corp’s most prolific ransomware strains.
Cyber Proxies: Evil Corp. and the Russian State
Whilst most cybercriminal activity is financially motivated, the Russian Intelligence Services have in some reported cases directed cybercriminals to conduct malicious cyber activity or used malware strains for espionage purposes. For example, in 2017, two Russian FSB officers were indicted by the US Department of Justice (DoJ) for directing criminal hackers to compromise 500 million Yahoo accounts. Another notable Russian cybercriminal, Vitaly Kovalev, who was sanctioned by the UK and US governments in 2023 for his senior role in the Trickbot cybercrime group, also had a relationship with the Russian Intelligence Services.
Evil Corp held a privileged position, and the relationship between the Russian state and this cybercriminal group went far beyond the typical state-criminal relationship of protection, payoffs, and racketeering. In fact, prior to 2019, Evil Corp was tasked by Russian Intelligence Services to conduct cyber-attacks and espionage operations against NATO allies.
Liaison with the intelligence services was led by Maksim Yakubets. As Evil Corp evolved, he became the group’s main contact with Russian officials, developing or seeking to develop relationships with FSB, SVR, and GRU officials. Multiple other members of the Evil Corp group have their own ties with the Russian state.
In particular, Yakubets’ father-in-law, Eduard Benderskiy, was a key enabler of Evil Corp’s state relationships.
Eduard Benderskiy is a former high-ranking official of the FSB’s secretive ‘Vympel’ unit and now owns various organizations carrying the ‘Vympel’ name. It has been reported by Bellingcat that through Vympel, Benderskiy has been involved in multiple overseas assassinations on behalf of the Russian state. Evidently, he is a highly connected individual still closely involved with the Kremlin’s activities.
Benderskiy leveraged his status and contacts to facilitate Evil Corp’s developing relationships with officials from the Russian Intelligence Services. After the US sanctions and indictments against Evil Corp members in December 2019, Benderskiy used his extensive influence to protect the group, both by providing senior members with security and by ensuring they were not pursued by internal Russian authorities.
Timeline of Evil Corp.’s Activity
2007-2011: The Early Days
-
- Maksim Yakubets, leader of the Evil Corp OCG, probably began his involvement in cybercrime activity around 2007.
- Since at least 2009, Yakubets worked with several notorious cybercriminals including Evgeniy Bogachev and Vitaliy Kovalev (involved in Dyre, Trickbot and Conti) to deploy malware.
2011-2014: The Business Club
-
- A number of Russian-speaking cybercriminals, including Maksim Yakubets and Vitaliy Kovalev, came together to form The Business Club cybercrime group. Yakubets would later team up with other members, Igor Turashev and Aleksandr Ryzhenkov, in Evil Corp.
- Aleksandr Ryzhenkov was part of an affiliate group of The Business Club which specialised in bank transfer fraud against the UK.
2014: Dridex and the Formation of Evil Corp as an OCG
-
- Maksim Yakubets worked with Aleksandr Ryzhenkov and other former members of The Business Club to create Dridex malware.
- Dridex was brought into operation in June 2014 and went on to become one of the most prolific and successful banking malware strains to date. The group set up the domain Ev17corp.biz to coordinate their operations, and Evil Corp was born.
- Much like current Ransomware as a Service (RaaS) models, Evil Corp segmented and rented out the Dridex botnet to affiliates who could use it for their own malicious cyber operations.
2017-2018: BitPaymer – The Group Begins Using Ransomware
-
- In mid-2017, Evil Corp used Dridex to start deploying ransomware. BitPaymer was used in a number of big game hunting attacks, targeting high value or high-profile organizations.
2019-2020: The Split – DoppelPaymer
-
- After an acrimonious split between Maksim Yakubets and another key Evil Corp member, Igor Turashev (beginning in mid-2019 but exacerbated by the December 2019 disruption), the group divided, and Turashev led the development of DoppelPaymer ransomware. DoppelPaymer was first observed in mid-2019 and continued infecting organizations throughout 2020.
- Since 2023, Igor Turashev is wanted by the German authorities for his involvement in DoppelPaymer ransomware.
- The remaining Evil Corp group, led by Yakubets and Ryzhenkov, began developing a new ransomware that would eventually become WastedLocker.
December 2019: US/UK Disruption
-
- Following operational support from the NCA, the US Treasury Office for Foreign Assets Control (OFAC) designated Evil Corp and a number of its members. The US Department of Justice also announced indictments and State Department rewards for information leading to the arrest of Maksim Yakubets and Igor Turashev.
- The disruptions in 2019 brought significant cost and risk to the group’s operations and bred mistrust and paranoia.
2020: Obfuscation and Evasion – WastedLocker
-
- Evil Corp. was forced to transform its modus operandi to further obfuscate its activities. This included no longer using Dridex and switching to the initial access tool SocGholish.
- The individuals became more secretive, abandoning online accounts and restricting their movements.
- Despite attempts to obfuscate their activities, Evil Corp was attributed to the WastedLocker ransomware strain, which they started deploying in mid-2020.
2020-2021: Hades, Phoenix Locker, PayloadBIN and Macaw
-
- Evil Corp continued to adapt and change their ransomware strains. They developed and deployed further ransomware strains Hades, Phoenix Locker, PayloadBIN, and Macaw, all of which shared a similar codebase.
- One of the notable attacks using Phoenix Locker resulted in a $40 million ransomware payment, the largest ever recorded at the time.
2022-2024: Diversification and Affiliation to LockBit - Whilst many original members are suspected to have gone on to other activity, some remaining Evil Corp members and affiliates have been involved in deploying other ransomware strains since 2022, including LockBit, continuing to employ SocGholish as an initial access tool.
- The NCA has determined that Aleksandr Ryzhenkov, Yakubets’ right-hand man, is a LockBit affiliate and has been involved in LockBit ransomware attacks against numerous organizations.
- LockBit ransomware was disrupted by an NCA-led international law enforcement takedown in February 2024 under Operation Cronos.
- Other members of the group continue to operate within the Russian Federation. For example, in December 2022, Igor Turashev and his company came third in a hackathon organized by the Wagner group.
Recent Action
Further Evil Corp. cybercriminals exposed following NCA investigation, one unmasked as LockBit affiliate, as UK, US, and Australia unveil sanctions.
16 members of Evil Corp, once believed to be the most significant cybercrime threat in the world have been sanctioned in the UK with their links to the Russian state and other ransomware groups, including LockBit, exposed. Sanctions have also been imposed by Australia and the US.
An extensive investigation by the NCA has helped map out the history and reach of Evil Corp’s criminality; from a family-centered financial crime group in Moscow that branched out into cybercrime, going on to extort at least $300 million from victims globally.
Today, the head of Evil Corp, Maksim Yakubets, and eight of those sanctioned by the US in 2019 have also been sanctioned in the UK by the Foreign, Commonwealth and Development Office, along with an additional seven individuals whose links and support for the group have not previously been exposed.
This includes Aleksandr Ryzhenkov, Yakubets’ right-hand man who has also been identified as a LockBit affiliate as part of Operation Cronos – the ongoing NCA-led international disruption of the group.
Conclusion
Evil Corp’s story is a prime example of the evolving threat posed by cybercriminals and ransomware operators. In their case, the activities of the Russian state played a particularly significant role, sometimes even co-opting this cybercrime group for its own malicious cyber activity. Born out of a coalescing of elite cybercriminals, Evil Corp.’s sophisticated business model made them one of the most pervasive and persistent cybercrime adversaries to date. After
being hampered by the December 2019 sanctions and indictments, the group has been forced to diversify its tactics as it attempted to continue causing harm whilst adapting to the changing cybercrime ecosystem. In 2024, further action taken against Evil Corp by the United Kingdom, United States, and Australian governments proves their attempts have not gone unnoticed and will not go unchallenged.
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment below!
Table of Contents
LEAVE A COMMENT?
Recent Comments
On Other Articles
- velma faile on Finally Tax Relief for American Scam Victims is on the Horizon – 2026: “I just did my taxes for 2025 my tax account said so far for romances scam we cd not take…” Feb 25, 19:50
- on Reporting Scams & Interacting With The Police – A Scam Victim’s Checklist [VIDEO]: “Yes, this is a scam. For your own sanity, just block them completely.” Feb 25, 15:37
- on Danielle Delaunay/Danielle Genevieve – Stolen Identity/Stolen Photos – Impersonation Victim UPDATED 2024: “She goes by the name of Sanrda John now” Feb 25, 10:26
- on Reporting Scams & Interacting With The Police – A Scam Victim’s Checklist [VIDEO]: “So far I have not been scam out of any money because I was aware not to give the money…” Feb 25, 07:46
- on Love Bombing And How Romance Scam Victims Are Forced To Feel: “I was love bombed to the point that I would do just about anything for the scammer(s). I was told…” Feb 11, 14:24
- on Dani Daniels (Kira Lee Orsag): Another Scammer’s Favorite: “You provide a valuable service! I wish more people knew about it!” Feb 10, 15:05
- on Danielle Delaunay/Danielle Genevieve – Stolen Identity/Stolen Photos – Impersonation Victim UPDATED 2024: “We highly recommend that you simply turn away form the scam and scammers, and focus on the development of a…” Feb 4, 19:47
- on The Art Of Deception: The Fundamental Principals Of Successful Deceptions – 2024: “I experienced many of the deceptive tactics that romance scammers use. I was told various stories of hardship and why…” Feb 4, 15:27
- on Danielle Delaunay/Danielle Genevieve – Stolen Identity/Stolen Photos – Impersonation Victim UPDATED 2024: “Yes, I’m in that exact situation also. “Danielle” has seriously scammed me for 3 years now. “She” (he) doesn’t know…” Feb 4, 14:58
- on An Essay on Justice and Money Recovery – 2026: “you are so right I accidentally clicked on online justice I signed an agreement for 12k upfront but cd only…” Feb 3, 08:16
ARTICLE META
Important Information for New Scam Victims
- Please visit www.ScamVictimsSupport.org – a SCARS Website for New Scam Victims & Sextortion Victims
- Enroll in FREE SCARS Scam Survivor’s School now at www.SCARSeducation.org
- Please visit www.ScamPsychology.org – to more fully understand the psychological concepts involved in scams and scam victim recovery
If you are looking for local trauma counselors please visit counseling.AgainstScams.org or join SCARS for our counseling/therapy benefit: membership.AgainstScams.org
If you need to speak with someone now, you can dial 988 or find phone numbers for crisis hotlines all around the world here: www.opencounseling.com/suicide-hotlines
A Note About Labeling!
We often use the term ‘scam victim’ in our articles, but this is a convenience to help those searching for information in search engines like Google. It is just a convenience and has no deeper meaning. If you have come through such an experience, YOU are a Survivor! It was not your fault. You are not alone! Axios!
A Question of Trust
At the SCARS Institute, we invite you to do your own research on the topics we speak about and publish, Our team investigates the subject being discussed, especially when it comes to understanding the scam victims-survivors experience. You can do Google searches but in many cases, you will have to wade through scientific papers and studies. However, remember that biases and perspectives matter and influence the outcome. Regardless, we encourage you to explore these topics as thoroughly as you can for your own awareness.
Statement About Victim Blaming
SCARS Institute articles examine different aspects of the scam victim experience, as well as those who may have been secondary victims. This work focuses on understanding victimization through the science of victimology, including common psychological and behavioral responses. The purpose is to help victims and survivors understand why these crimes occurred, reduce shame and self-blame, strengthen recovery programs and victim opportunities, and lower the risk of future victimization.
At times, these discussions may sound uncomfortable, overwhelming, or may be mistaken for blame. They are not. Scam victims are never blamed. Our goal is to explain the mechanisms of deception and the human responses that scammers exploit, and the processes that occur after the scam ends, so victims can better understand what happened to them and why it felt convincing at the time, and what the path looks like going forward.
Articles that address the psychology, neurology, physiology, and other characteristics of scams and the victim experience recognize that all people share cognitive and emotional traits that can be manipulated under the right conditions. These characteristics are not flaws. They are normal human functions that criminals deliberately exploit. Victims typically have little awareness of these mechanisms while a scam is unfolding and a very limited ability to control them. Awareness often comes only after the harm has occurred.
By explaining these processes, these articles help victims make sense of their experiences, understand common post-scam reactions, and identify ways to protect themselves moving forward. This knowledge supports recovery by replacing confusion and self-blame with clarity, context, and self-compassion.
Additional educational material on these topics is available at ScamPsychology.org – ScamsNOW.com and other SCARS Institute websites.
Psychology Disclaimer:
All articles about psychology and the human brain on this website are for information & education only
The information provided in this article is intended for educational and self-help purposes only and should not be construed as a substitute for professional therapy or counseling.
While any self-help techniques outlined herein may be beneficial for scam victims seeking to recover from their experience and move towards recovery, it is important to consult with a qualified mental health professional before initiating any course of action. Each individual’s experience and needs are unique, and what works for one person may not be suitable for another.
Additionally, any approach may not be appropriate for individuals with certain pre-existing mental health conditions or trauma histories. It is advisable to seek guidance from a licensed therapist or counselor who can provide personalized support, guidance, and treatment tailored to your specific needs.
If you are experiencing significant distress or emotional difficulties related to a scam or other traumatic event, please consult your doctor or mental health provider for appropriate care and support.
Also read our SCARS Institute Statement about Professional Care for Scam Victims – click here to go to our ScamsNOW.com website.
















Thank you for your comment. You may receive an email to follow up. We never share your data with marketers.