Every Day Scam Victims Lose Their Cryptocurrency Investment
However, what victims and the police often do not know is that cryptocurrency transactions are visible and traceable.
This means that the transactions can be traced as they pass through wallets most of the time, and that law enforcement can recover them with court orders.
This is not a simple process but it is not terribly complicated either.
Who Is This Article For?
This is an introductory article for both the victims of cryptocurrency theft (fraud/scams) and to help law enforcement better understand the issues and have an overview of the process, tools, and techniques.
It would be impossible for us to provide training in all the technical processes of tracing or in the criminal justice processes for seizure and return to victims. The purpose of this article is to introduce the topics and help everyone understand that recovery is possible, it is just knowledge and tools that have to be learned.
We also want to caution victims against paying for tracing because law enforcement will do this for free. Of course, law enforcement has to pay for the tools, but they will not charge victims. If someone wants to charge victims for this service, they may be violating local laws governing private investigations, and ultimately, law enforcement will have to recreate the trace anyway for evidentiary purposes. So, in most cases paying for crypto tracing is a waste of money, exploiting desperate crime victims, and possibly illegal.
First, let’s talk about the basics!
The Basics – Paid Vs. Free Tracing – For Victims
There are MANY companies that prey on crime victims and offer tracing services. NEVER USE THEM!
Law enforcement, prosecutors, and courts are the ONLY ones that can recover your crypto – PERIOD! It takes a court order to seize and return the cryptocurrency back to a victim! However, the big problem is that local law enforcement is mostly ignorant about this process. While it is possible to help local law enforcement in the United States address this gap, it is much more difficult internationally!
The good news, if there is any, is that the crypto is not going anywhere! What we mean is that the cryptocurrency that was stolen (through fraud or other means) from you is stolen property – it remains yours and this is recognized in most countries around the world – assuming that cryptocurrency transactions are legal – they are illegal in some countries.
This means that even if the original criminals cashed out and sold the cryptocurrency (engaged in a transaction) with someone, that transaction is still (hopefully) visible and can be traced. This allows law enforcement the time to learn the tools and techniques for recovery and come back to it later (with your urging, of course.) So even years later, if there is a traceable wallet that contains your cryptocurrency, it is still potentially recoverable because in most countries there is no time limit on stolen property!
The Basics – Bitcoin Is Not Anonymous
Cryptocurrencies have not yet fully entered the mainstream as widely accepted, everyday means of payment. They still carry a negative connotation by evoking images of ransomware, fraudsters, pig butchering scams, hackers, and internet drug deals.
You would think that criminals would choose an untraceable and completely private payment option, such as bank wire transfers – where they can set up fake bank accounts and then withdraw the money never to be seen again. But Bitcoin (and the others) is by design, one of the most transparent currencies out there. This transparency helps to carry out the transactions in a decentralized transparent manner.
Normally, when you transfer real money, a bank will update its records, lower your balance, and credit somebody else’s. This all happens behind closed doors, and only you will know the details of your account. This process requires a central bookkeeper whom you have to trust — in this case, the bank and banking system, as well as its record-keeping integrity.
For this same process to work without a central authority (a bank), the creator of cryptocurrency developed the blockchain. The blockchain is a ledger (a record system) distributed among many different nodes (computers) that are updated every time a new Bitcoin transaction is made. Anybody can run a node and observe the transactions being executed. Ledgers, therefore, permit Bitcoin to function with distributed, instead of centralized, accountability and every transaction is visible.
Some cryptocurrencies use obfuscated ledgers (such as Monero), but Bitcoin does not. This means that anybody can observe every Bitcoin transaction ever made (and graph it). The balance of every Bitcoin address (account) is then also discoverable. This leads to addresses with large balances garnering much attention online. The 1933p Bitcoin address is one of those addresses, with a peak value of 2 billion USD.
The Basics – Can Anyone Trace A Bitcoin Transaction?
Through blockchain explorers, one can easily track Bitcoin transactions, but it is becoming increasingly difficult to conduct cryptocurrency transactions anonymously.
It is certainly possible to trace a crypto transaction. Bitcoin explorers allow you to map activity on the blockchain. Thanks to this transparency, transactions are traceable and you can think of the blockchain as a kind of open database of all of these transactions.
Other cryptocurrencies like Ether (ETH) and Solana (SOL) also have their own blockchain explorers (see below for a list with links) called Etherscan and SolScan. In all these explorers, you can find information about the transactions on the blockchain, such as how much crypto was sent and which addresses were involved in the transaction. Despite the transparency of the blockchain, many people think that you can still make Bitcoin transactions anonymously – what they fail to understand is that yes it is anonymous, in that no name is attached, but the transactions are fully-traceable.
However, more and more countries are implementing “Know Your Customer” (KYC) rules, which require you to reveal your identity on centralized trading platforms. By disclosing your identity, it becomes a lot easier for the government to discover what transactions you have carried out and to see what is in your Bitcoin wallet. By the way, the KYC regulations are in response to rampant fraud across the globe.
To be able to trade on a central exchange, personal data will have to be supplied to the exchange (but not always verified.) Bitcoin addresses can therefore be linked to personal data. Since the data of previous Bitcoin transactions is not deleted, it is always possible to view past transactions.
The Basics – What Makes Bitcoin Traceable?
Bitcoin transactions are traceable because Bitcoin’s blockchain is completely transparent and every transaction is publicly stored on a distributed ledger.
Thanks to the transparency of the blockchain, it is possible to easily track money flows. If a wallet address is known, then the transactions made can be traced back and traced in the future. All these transactions can be viewed in detail. In this way, it is possible to see which amount was sent, but also on which date and to which wallet.
Unfortunately, criminals are smart and are also trying to develop “obfuscator” tools to disguise cryptocurrency coming into these tools and where they go out. This can make it much harder to trace, but many modern law enforcement tools can address this.
The Basics – How Are Bitcoin Transactions Traced?
With increasing legislation and surveillance, governments can trace fraudulent BTC transactions more efficiently. Law enforcement jurisdictions are regularly announcing cryptocurrency recovery.
In recent years, billions in cryptocurrencies has been seized by various governments worldwide. Criminals saw the opportunities that blockchain technology has to offer and tried to buy cryptocurrencies such as Bitcoin as anonymously as possible, but it has failed to be the perfect solution they wanted.
When trading from wallets whose identity is not known, transactions can be traced quickly. However, skill and training are required to perform traces into and out of complex exchanges.
Here is an example trace done using the Blockchain Intelligence Groups tools (see below)
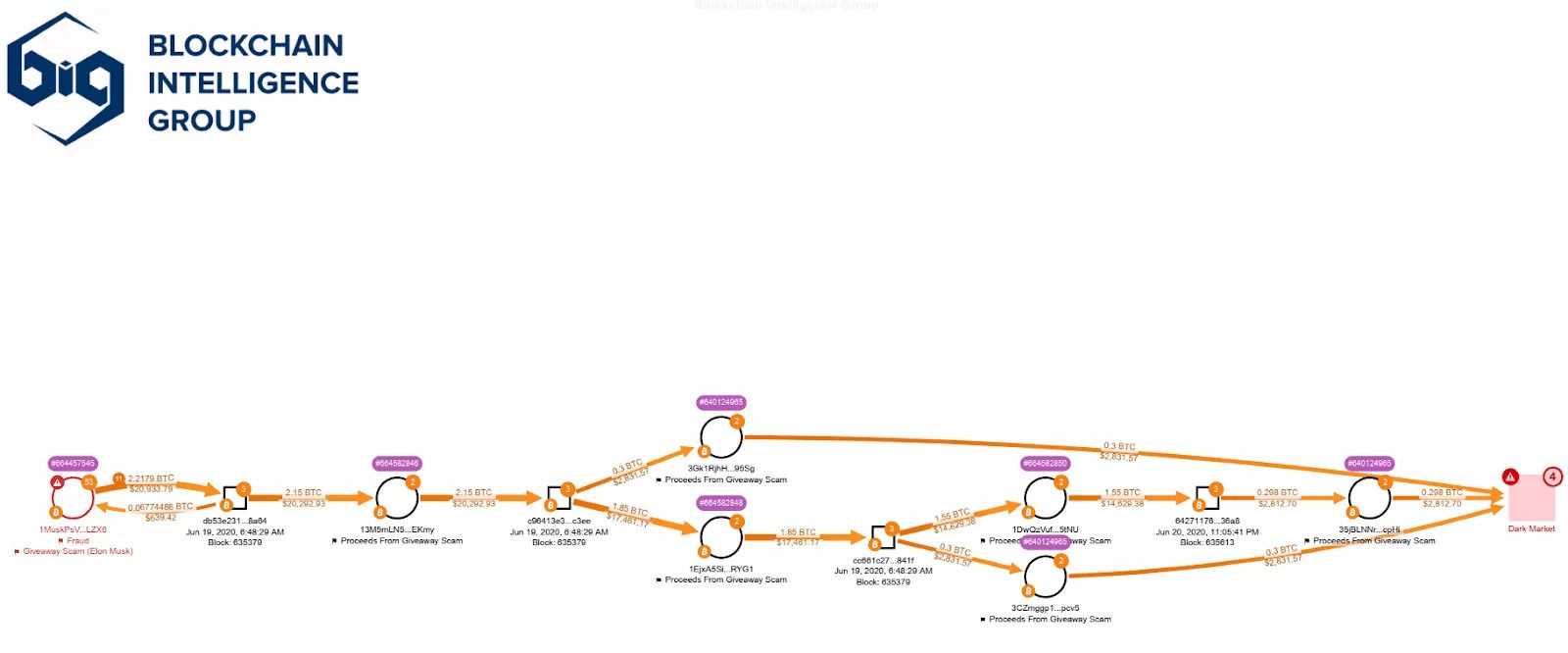
example bitcoin trace
The Basics – Search For A Bitcoin Wallet Address
Yes, it is possible to search for a Bitcoin wallet address through a Bitcoin explorer, most of the time. However, finding a crypto address does not mean that you also know the identity behind it. The good news that, at least, in the United States, the identity of the wallet owner is not needed to recover it. The District Attorney’s office in Santa Clara California has perfected a process for recovery even if the defendant is unknown.
When you don’t have any identifying information that goes with the Bitcoin wallet, can be harder to search. Through a blockchain explorer, it is easy to find transactions and addresses, and that is really all that is needed (in many cases) to effect a recovery.
Because someone’s wallet address does not have to be anonymous but can be hard to find, a Bitcoin wallet address is called a pseudonym, an alias, which is different from someone’s actual name. The data is not linked to an identity, but it is still possible to trace someone’s identity or their pseudonym.
The Basics – Challenges In Tracking A Bitcoin Address
It can be difficult to track Bitcoin transactions when people use various wallets and Bitcoin mixers. These factors disrupt the search process and take up a lot of time.
Despite the fact that it is challenging for users of a Bitcoin wallet to conduct transactions completely anonymously, there are several ways to get close to anonymity. For example, it is possible to use a cryptocurrency mixer.
In this case, it is a Bitcoin mixer, which ensures that it is more difficult to make Bitcoin traceable. This is done by mixing BTC transactions from different people together in a pool, then sending the transactions to the intended addresses.
In addition, wallets can also be very difficult to monitor. If someone does not want their activities on the Bitcoin network to be traceable, it is possible to create a sort of smoke screen. By creating many crypto wallets and carrying out various transactions between these wallets, it can be more difficult for anyone to trace transactions and wallets.
Both challenges are difficult on their own, but combining them can make tracking Bitcoin addresses a lot more difficult. Tracking transactions and wallets will take an enormous amount of time and energy.
6.Can you have an anonymous Bitcoin wallet?
Anonymous Bitcoin wallets exist, but be careful while handling them. You can reveal your identity, which defeats the purpose of the wallet.
It is certainly possible to have an anonymous Bitcoin wallet. However, a wallet alone is not enough to ensure this anonymity. When someone makes several transactions, an identity can be linked to a wallet where this information is known. Due to the tightened KYC rules for exchanges, it seems to be increasingly challenging to conduct transactions in a completely anonymous way.
Nevertheless, there are Bitcoin wallets that allow you to operate completely anonymously. The Electrum wallet is an example of this, which can also be integrated with a hardware wallet. Before making the choice to use an anonymous wallet, it is useful to first consider how Bitcoin will get on this wallet. When BTC is sent from an exchange with KYC, the anonymity is already gone.
The Basics – Remember
It is not a problem to share public keys, but make sure the private key cannot be found by anyone (except for police use.) Transactions can be sent to the public key, which is completely secure.
The private key is the password to enter the wallet. It is important that this unique code is kept in an offline place where no one can access it. Sharing personal data, such as the private keys and the wallet password, with others can cause the wallet in question to be emptied (contents stolen.) Therefore, only share the public key if necessary and keep the other codes in a safe place (except with he police, they may need your private key for recovery purposes.)
Tracing Transactions through the Blockchain
It begins by using a Blockchain Explorer
We are not going to try and deliver a complete tutorial on the tracing process. The different tool providers will provide law enforcement with plenty of free training, plus different law enforcement groups do this as well.
The process is evolving and there are new techniques from time to time, so please check with the tool (explorers) providers for the latest techniques, processes, and training.
Some of these tools are relatively easy, some are very complex. Partly it depends on the complexities of the cryptocurrency passing through exchanges which sometimes try to hide the final wallet where the crypto lands and is held.
Training For Law Enforcement:
- Chainalysis Academy https://academy.chainalysis.com/
- Fintechfocus.io – private consultancy training law enforcement
Tools For Law Enforcement:
- Cryptocurrency intelligence and blockchain analytics – CipherTrace https://ciphertrace.com/
- TRM Labs Forensics https://www.trmlabs.com/products/forensics – subscription-based tool
- Chainalysis https://demo.chainalysis.com/get-demo/ & https://www.chainalysis.com/chainalysis-reactor/
- Blockchain Analysis, Compliance | Blockchain Intelligence Group https://blockchaingroup.io/
Public Bitcoin Blockchain Explorers:
- https://blockchair.com/ – they offer a free search and tracing tool online
- Blockchain.com https://www.blockchain.com/
Other Cryptocurrency Blockchain Explorers:
Other Guides:
There are many only guides using various tools, here are some of those:
- Ivan on Tech explains Bitcoin Tracing: https://youtu.be/T_3dMKCFXf0
- https://www.maltego.com/blog/tracing-transactions-through-the-bitcoin-blockchain-with-maltego/
More Information On This Topic
SCARS Webinar: Money Recovery or Not!
SCARS Q&A With Prosecutor Erin West
SCARS Interview With Prosecutor Erin West
SCARS Webinar: Romance Scams #1 – Pig Butchering Fraud & Military Impersonation Fraud
A Third-Party Explanation Of Bitcoin Tracing
Third-Party Video on Bitcoin Investigation and Wallet Seizure
This is a highly technical explanation!
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment below!
Do You Need Support?
Get It Now!
SCARS provides the leading Support & Recovery program for relationship scam victims – completely FREE!
Our managed peer support groups allow victims to talk to other survivors and recover in the most experienced environment possible, for as long as they need. Recovery takes as long as it takes – we put no limits on our support!
SCARS is the most trusted support & education provider in the world. Our team is certified in trauma-informed care, grief counseling, and so much more!
To apply to join our groups visit support.AgainstScams.org
We also offer separate support groups for family & friends too.
Become a
SCARS STAR™ Member
SCARS offers memberships in our STAR program, which includes many benefits for a very low annual membership fee!
SCARS STAR Membership benefits include:
- FREE Counseling or Therapy Benefit from our partner BetterHelp.com
- Exclusive members-only content & publications
- Discounts on SCARS Self-Help Books Save
- And more!
To learn more about the SCARS STAR Membership visit membership.AgainstScams.org
To become a SCARS STAR Member right now visit join.AgainstScams.org
To Learn More Also Look At Our Article Catalogs
Scam & Crime Types
More SCARS
- ScamsNOW Magazine – ScamsNOW.com
- ContraEstafas.org
- ScammerPhotos.com
- AnyScam.com – reporting
- AgainstScams.org – SCARS Corporate Website
- SCARS YouTube Video Channel













This article reminds me just how much I hate the whole crypto subject. I wish my local law enforcement would take a more aggressive role in my case. I don’t think they have the expertise to really get me results. I sent them the training & tools for law enforcement links found in this article.