The Calisto Group Is A Russian State-sponsored Cyberespionage Group Believed To Be Operating Under The Direction Of The Federal Security Service (FSB)
The Calisto Group is also known as Seaborgium, Star Blizzard, ColdRiver, and TA446,
Calisto Group Activities:
- Targeted attacks: The Calisto Group primarily targets military personnel, government officials, think tanks, journalists, and defense-industrial entities in Eastern Europe, the South Caucasus, the Ukraine, and the UK.
- Espionage: The primary goal of the Calisto Group is to steal sensitive information and data for the Russian government.
- Spear-phishing: They commonly use spear-phishing emails as their attack vector, tricking victims into clicking malicious links or opening infected attachments.
- Custom tools: The Calisto Group is known to develop and use sophisticated custom tools for their operations.
- Global reach: Their activities are not limited to specific regions, as they have been observed targeting entities worldwide, including the US and Europe.
Calisto Group’s Tactics and Techniques
The Calisto Group utilizes various tactics and techniques to achieve their goals of cyberespionage and information theft. Here are some of their known methods:
Spear Phishing Emails:
- This is the group’s primary attack vector, involving emails tailored to specific victims with personalized content and attachments designed to entice clicks or downloads.
- These emails often impersonate legitimate individuals or organizations, making them appear trustworthy.
- They may contain links to malicious websites or infected attachments that install malware on the victim’s device.
Social Engineering:
- This involves psychological manipulation techniques to deceive victims into divulging sensitive information or taking actions that benefit the attackers.
- They may use emotional appeals, threats, or fabricated stories to gain trust and exploit vulnerabilities.
- This can include tactics like offering enticing jobs, claiming to have compromising information, or posing as technical support representatives.
Custom Tools:
- The Calisto Group is known for developing and deploying sophisticated custom tools for their operations, including:
- Exploit kits: Code designed to exploit vulnerabilities in software and gain access to systems.
- Malware: Malicious software used to steal data, monitor activity, or control infected devices.
- Command and control (C2) servers: Used to communicate with compromised systems and issue commands.
- Data exfiltration tools: Techniques used to steal and transfer sensitive information from victim systems.
Advanced Techniques:
- The group employs various advanced techniques to remain undetected and evade security measures, such as:
- Zero-day exploits: Exploiting vulnerabilities in software before vendors release patches.
- Sandboxing evasion: Techniques to bypass security software that monitors suspicious activity.
- Lateral movement: Moving within a network after gaining initial access to one system.
- Data encryption: Encrypting stolen information to make it difficult to analyze.
Targeting:
- The Calisto Group strategically chooses its targets, focusing on individuals and organizations with access to sensitive information valuable to the Russian government.
- Their targets typically include:
- Government officials and military personnel: To gather intelligence on military plans, diplomatic relations, and national security strategies.
- Think tanks and research institutions: To access information on critical technologies, economic analysis, and political developments.
- Journalists and media outlets: To monitor public opinion and control narratives.
- Defense-industrial entities: To steal information on weapons development, military capabilities, and strategic partnerships.
Calisto Group Impact:
- Information theft: The Calisto Group has successfully stolen sensitive information from various organizations, potentially impacting national security and diplomatic relations.
- Disruption and instability: Their attacks can disrupt operations, cause financial losses, and erode trust in institutions.
- Escalating tensions: Their activities contribute to the ongoing geopolitical tensions between Russia and the West.
Calisto Group Responses and Investigations:
- Governments and security agencies: Several governments and security agencies, including the UK National Cyber Security Centre (NCSC), Microsoft Threat Intelligence Center, and Google’s Threat Analysis Group, have attributed attacks to the Calisto Group and issued warnings about their activities.
- Sanctions: The UK and the US have imposed sanctions on individuals associated with the Calisto Group.
- Ongoing investigations: Investigations are ongoing to understand the Calisto Group’s capabilities further and track their activities.
Protecting Against the Calisto Group:
- Awareness: Organizations and individuals should be aware of the Calisto Group’s tactics and techniques to avoid falling victim to their attacks.
- Cybersecurity measures: Implementing strong cybersecurity measures, such as using multi-factor authentication and keeping software updated, can help mitigate the risk of successful attacks.
- Reporting: Reporting suspicious activity to authorities and security researchers can help identify and track the Calisto Group’s activities.
Summary
The Calisto Group is a sophisticated and active Russian state-sponsored cyberespionage group posing a significant threat to national security and international stability. By remaining vigilant, implementing strong cybersecurity measures, and collaborating with authorities, we can work together to protect ourselves from their malicious activities.
By understanding the Calisto Group’s tactics and techniques, organizations and individuals can improve their defenses and better prepare for potential attacks. Implementing strong cybersecurity measures, being skeptical of unsolicited communications, and staying informed about emerging threats can significantly reduce the risk of falling victim to this sophisticated cybercrime & cyberespionage group.
Two Russian Nationals Working with Russia’s Federal Security Service Charged in the United States with Global Computer Intrusion Campaign
Indictment Alleges the So-Called “Callisto Group” Hacked Computers in the United States and Allied Countries, and Stole Information Used in Foreign Malign Influence Operations Designed to Influence the U.K.’s 2019 Elections
A federal grand jury in San Francisco returned an indictment on Tuesday charging two individuals with a campaign to hack into computer networks in the United States, the United Kingdom, other North Atlantic Treaty Organization member countries, and Ukraine, all on behalf of the Russian government.
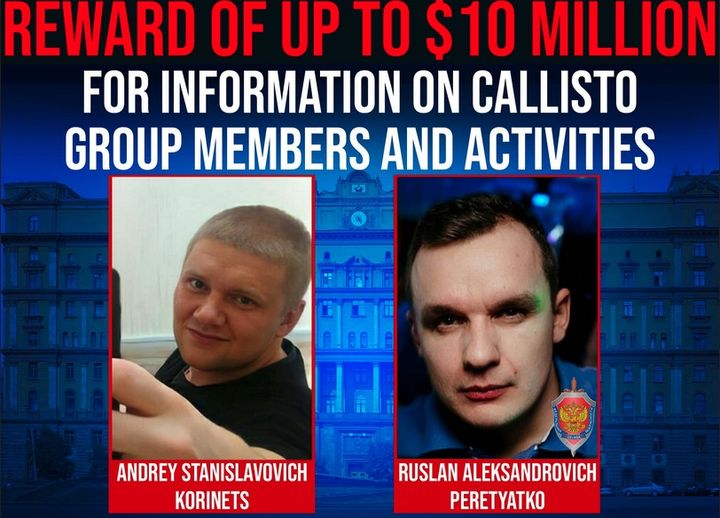
According to court documents, Ruslan Aleksandrovich Peretyatko (Перетятько Руслан Александрович), an officer in Russia’s Federal Security Service (FSB) Center 18, Andrey Stanislavovich Korinets (Коринец Андрей Станиславович) and other unindicted conspirators employed a sophisticated spear phishing campaign to gain unauthorized, persistent access (i.e., “hack”) into victims’ computers and email accounts.
“The Russian government continues to target the critical networks of the United States and our partners, as highlighted by the indictment unsealed today,” said Assistant Attorney General Matthew G. Olsen of the Justice Department’s National Security Division. “Through this malign influence activity directed at the democratic processes of the United Kingdom, Russia again demonstrates its commitment to using weaponized campaigns of cyber espionage against such networks in unacceptable ways. The Department of Justice will respond to such behavior with an even more determined commitment to disrupt those activities and to hold accountable the individuals responsible.”
“Today’s indictment is part of a coordinated international response to send a message to the conspirators that the whole of the United States government stands together and with our partners internationally to identify and disrupt cyber espionage actors, particularly those seeking to obtain government information and attempting to create chaos in democratic processes,” said U.S. Attorney Ismail J. Ramsey for the Northern District of California. “We are grateful to all of our partners for their assistance in addressing these threats posed by the FSB’s action in the Northern District of California, across the United States, and around the world.”
“The FBI will not stand idly by as Russia continues to perpetuate this type of targeted malicious activity,” said Assistant Director Bryan Vorndran of the FBI’s Cyber Division. “Russian interference through malign foreign influence campaigns is deplorable, and we will not tolerate it in the United States or directed against our foreign partners. The FBI is dedicated to combating this pervasive threat and will tirelessly seek to prevent and disrupt these criminal acts carried out by Russia.”
The indictment, which was unsealed today, alleges the conspiracy targeted current and former employees of the U.S. Intelligence Community, Department of Defense, Department of State, defense contractors, and Department of Energy facilities between at least October 2016 and October 2022. In addition, the indictment alleges the conspirators – known publicly by the name “Callisto Group” – targeted military and government officials, think tank researchers and staff, and journalists in the United Kingdom and elsewhere, and that information from certain of these targeted accounts was leaked to the press in Russia and the United Kingdom in advance of U.K. elections in 2019.
As a common example, the conspirators used “spoofed” email accounts designed to look like personal and work-related email accounts of the group’s targets. The conspirators allegedly also sent sophisticated-looking emails that appeared to be from email providers suggesting users had violated terms of service. These messages were designed to trick victims into providing their email account credentials to false login prompts. Once the conspirators fraudulently obtained the victim’s credentials, they were able to use those credentials to access the victims’ email accounts at will.
In addition to the indictment, the Department of the Treasury’s Office of Foreign Assets Control (OFAC) announced that it has sanctioned both Peretyatko and Korinets for their roles in malicious cyber-enabled activity. Moreover, the United Kingdom has issued sanctions of its own, and the U.S. Department of State announced rewards of up to $10 million for information leading to the identification or location of Peretyatko and Korinets, as well as their conspirators.
In addition to the name “Callisto Group,” FSB Center 18 is known by cybersecurity investigators as “Dancing Salome” by Kaspersky Labs, “STAR BLIZZARD” by Microsoft Threat Intelligence Center and “COLDRIVER” by Google’s Threat Analysis Group.
The defendants are each charged with one count of conspiracy to commit an offense against the United States, namely, computer fraud, which carries a maximum sentence of five years in prison for PERETYATKO, and up to 10 years for KORINETS. The maximum potential sentences in this case are prescribed by Congress and are provided here for informational purposes only, as any sentencings of the defendants will be determined by the assigned judge.
The investigation was conducted jointly by the U.S. Attorney’s Office for the Northern District of California, the National Security Cyber Section of the Justice Department’s National Security Division and the FBI San Francisco Field Office. The FBI’s Cyber Division, Cyber Assistant Legal Attachés, and Legal Attachés in countries around the world provided essential support. Numerous victims cooperated and provided valuable assistance in the investigation.
An indictment is merely an allegation. All defendants are presumed innocent until proven guilty beyond a reasonable doubt in a court of law.
More About Organized Crime Groups:
- REKK Fraud Organization – Retail Fraud – 2023 (romancescamsnow.com)
- Scattered Spider Cybercriminals – SIM Swap Cyberattacks 2023 (romancescamsnow.com)
- Octo Tempest Cybercrime Gang – Organized Criminal Enterprise Profile (romancescamsnow.com)
- Nigerian Killer Bee Cybercrime Syndicate – Organized Criminal Enterprise Profile (romancescamsnow.com)
- 14K Triad Cybercrime Gang – Organized Criminal Enterprise Profile (romancescamsnow.com)
- Cavalcante Cybercrime Gang – Organized Criminal Enterprise Profile (romancescamsnow.com)
- Cobalt Cybercrime Gang – Organized Criminal Enterprise Profile (romancescamsnow.com)
- Black Axe – Organized Criminal Enterprise Profile (romancescamsnow.com)
- Red Dragon – Organized Criminal Enterprise Profile (romancescamsnow.com)
SCARS Resources:
- Getting Started Right: ScamVictimsSupport.org
- Sextortion Scam Victims: Sextortion Victims Support – The Essentials (scamvictimssupport.org)
- For New Victims of Relationship Scams newvictim.AgainstScams.org
- Subscribe to SCARS Newsletter newsletter.againstscams.org
- Sign up for SCARS professional support & recovery groups, visit support.AgainstScams.org
- Join our Scam Survivors United Chat & Discussion Group facebook.com/groups/scam.survivors.united
- Find competent trauma counselors or therapists, visit counseling.AgainstScams.org
- Become a SCARS Member and get free counseling benefits, visit membership.AgainstScams.org
- Report each and every crime, learn how to at reporting.AgainstScams.org
- Learn more about Scams & Scammers at RomanceScamsNOW.com and ScamsNOW.com
- Scammer photos ScammerPhotos.com
- SCARS Videos youtube.AgainstScams.org
- Self-Help Books for Scam Victims are at shop.AgainstScams.org
- Donate to SCARS and help us help others at donate.AgainstScams.org
- Worldwide Crisis Hotlines: https://blog.opencounseling.com/suicide-hotlines/
Other Cyber Resources
- Block Scam Domains: Quad9.net
- Global Cyber Alliance ACT Cybersecurity Tool Website: Actionable Cybersecurity Tools (ACT) (globalcyberalliance.org) https://act.globalcyberalliance.org/index.php/Actionable_Cybersecurity_Tools_(ACT)_-_Simplified_Cybersecurity_Protection
- Wizer Cybersecurity Training – Free Security Awareness Training, Phishing Simulation and Gamification (wizer-training.com)
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment below!
Do You Need Support?
Get It Now!
SCARS provides the leading Support & Recovery program for relationship scam victims – completely FREE!
Our managed peer support groups allow victims to talk to other survivors and recover in the most experienced environment possible, for as long as they need. Recovery takes as long as it takes – we put no limits on our support!
SCARS is the most trusted support & education provider in the world. Our team is certified in trauma-informed care, grief counseling, and so much more!
To apply to join our groups visit support.AgainstScams.org
We also offer separate support groups for family & friends too.
Become a
SCARS STAR™ Member
SCARS offers memberships in our STAR program, which includes many benefits for a very low annual membership fee!
SCARS STAR Membership benefits include:
- FREE Counseling or Therapy Benefit from our partner BetterHelp.com
- Exclusive members-only content & publications
- Discounts on SCARS Self-Help Books Save
- And more!
To learn more about the SCARS STAR Membership visit membership.AgainstScams.org
To become a SCARS STAR Member right now visit join.AgainstScams.org
To Learn More Also Look At Our Article Catalogs
Scam & Crime Types
More SCARS
- ScamsNOW Magazine – ScamsNOW.com
- ContraEstafas.org
- ScammerPhotos.com
- AnyScam.com – reporting
- AgainstScams.org – SCARS Corporate Website
- SCARS YouTube Video Channel













Leave A Comment