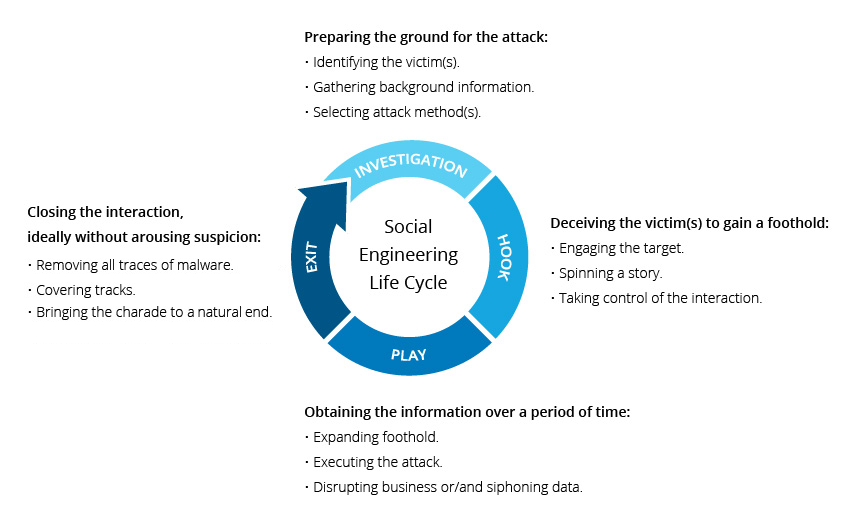
What is Social Engineering?
Social engineering is the practice of manipulating people into performing actions or divulging confidential information. It is a type of con or confidence trick for the purpose of information gathering, fraud, or system access. Social engineering attacks can be carried out online, in person, and over the phone.
Social engineering attacks are often very successful because they exploit human psychology.
Social Engineering is not limited to cybersecurity or cybercrimes and can be used in a variety of contexts, including:
- Business: Social engineering can be used to gain access to confidential business information, such as customer data or trade secrets. For example, an attacker might call a company employee and pretend to be a customer or vendor in order to get them to reveal their password.
- Politics: Social engineering can be used to manipulate people into voting for a particular candidate or supporting a particular cause. For example, an attacker might create a fake news article that makes false claims about a candidate in order to sway voters against them.
- Personal relationships: Social engineering can be used to manipulate people into doing things that they would not normally do, such as giving money or revealing personal information. For example, an attacker might create a fake online profile and pretend to be someone they’re not in order to trick someone into falling in love with them.
Social engineering is a complex and ever-evolving field, and new techniques are being developed all the time. It is important to be aware of the latest social engineering scams and to take steps to protect yourself.
But the most important thing to understand about social engineering is that it has always been here. Nature itself uses social engineering to survive. Plants and animals use it in millions of ways to find a mate, catch a meal, reproduce, hold territory, and so much more. It is also used in physical crimes, not just cyber!
Social Engineering in the Cyber Domain
Attackers may prey on people’s fear, greed, curiosity, or desire to be helpful. For example, an attacker might send a phishing email that appears to be from a legitimate bank, asking the recipient to click on a malicious link and enter their login credentials. Or, an attacker might call someone pretending to be from tech support and offer to help them fix a problem with their computer. Once the attacker has gained access to the victim’s computer, they can steal their personal information or install malware.
Social engineering attacks are often very successful because they exploit human psychology. Attackers may prey on people’s fear, greed, curiosity, or desire to be helpful. For example, an attacker might send a phishing email that appears to be from a legitimate bank, asking the recipient to click on a malicious link and enter their login credentials. Or, an attacker might call someone pretending to be from tech support and offer to help them fix a problem with their computer. Once the attacker has gained access to the victim’s computer, they can steal their personal information or install malware.
There are literally thousands of different types of social engineering attacks, but some of the most common include:
- Phishing: Phishing attacks involve sending fraudulent emails or text messages that appear to be from a legitimate source. The goal of phishing attacks is to trick the recipient into revealing sensitive information, such as passwords or credit card numbers.
- Baiting: Baiting attacks involve leaving behind a physical object, such as a USB drive or CD, that contains malware. When someone picks up the object and inserts it into their computer, the malware is installed and can steal data or damage the system.
- Quid pro quo: Quid pro quo attacks involve offering something of value in exchange for sensitive information. For example, an attacker might offer a free gift card or technical support in exchange for a password or credit card number.
- Pretexting: Pretexting attacks involve creating a false identity in order to gain someone’s trust. For example, an attacker might pretend to be a bank employee or a police officer in order to trick someone into revealing sensitive information.
- Tailgating: Tailgating attacks involve following someone into a secure area without authorization. For example, an attacker might follow someone into a building or onto a computer network.
- CEO fraud: CEO fraud attacks involve impersonating a high-level executive, such as a CEO or CFO, in order to trick someone into authorizing a financial transaction.
Catalog of Social Engineering
Attacks, Scans & Fraud, Manipulations, and More!
Relationship Scams
Are relationship scams/impersonation scams considered social engineering attacks?
Relationship scams and impersonation scams are considered social engineering attacks. Social engineering attacks are any type of attack that relies on human manipulation rather than technical expertise to gain access to sensitive information or systems. Relationship scams and impersonation scams specifically target victims’ emotions and vulnerabilities in order to gain their trust and exploit them.
Relationship scammers often create fake online profiles and pretend to be someone they are not, such as a member of the military, a successful business person, or a doctor. They may also use stolen photos of real people to create their fake profiles. Once they have gained the victim’s trust, they may ask the victim for money, gifts, or even to travel to meet them in person.
Impersonation scammers, on the other hand, typically pretend to be someone the victim already knows and trusts, such as a family member, friend, or coworker, but they can also be where the scammer has stolen the face or identity of a stranger. They may contact the victim via email, phone, or text message and ask to develop a relationship and then later ask for help with an urgent matter, such as paying a bill or sending money for a medical emergency, etc.
The List of Social Engineering Traps, Attacks, and Scams
List of many of the most common types of social engineering attacks or scam types in use to defraud individuals and businesses:
- Phishing: Phishing attacks involve sending fraudulent emails or text messages that appear to be from a legitimate source, such as a bank or government agency. The goal of phishing attacks is to trick the recipient into revealing sensitive information, such as passwords or credit card numbers.
- Baiting: Baiting attacks involve leaving behind a physical object, such as a USB drive or CD, that contains malware. When someone picks up the object and inserts it into their computer, the malware is installed and can steal data or damage the system.
- Quid pro quo: Quid pro quo attacks involve offering something of value in exchange for sensitive information. For example, an attacker might offer a free gift card or technical support in exchange for a password or credit card number.
- Pretexting: Pretexting attacks involve creating a false identity in order to gain someone’s trust. For example, an attacker might pretend to be a bank employee or a police officer in order to trick someone into revealing sensitive information.
- Tailgating: Tailgating attacks involve following someone into a secure area without authorization. For example, an attacker might follow someone into a building or onto a computer network.
- CEO fraud: CEO fraud attacks involve impersonating a high-level executive, such as a CEO or CFO, in order to trick someone into authorizing a financial transaction.
- Relationship scams: Relationship scammers often create fake online profiles and pretend to be someone they are not, such as a member of the military, a successful businessperson, or a doctor. They may also use stolen photos of real people to create their fake profiles. Once they have gained the victim’s trust, they may ask the victim for money, gifts, or even to travel to meet them in person.
- Impersonation scams: Impersonation scammers typically pretend to be someone the victim already knows and trusts, such as a family member, friend, or coworker. They may contact the victim via email, phone, or text message and ask for help with an urgent matter, such as paying a bill or sending money for a medical emergency.
- Tech support scams: Tech support scammers typically call people claiming to be from a well-known tech company, such as Microsoft or Apple. They may claim that the person’s computer is infected with a virus or that they need to update their software. The scammer will then try to trick the person into giving them remote access to their computer or paying for unnecessary tech support services.
- Charity scams: Charity scammers may call, email, or send letters to people asking for donations to charities that either do not exist or are not legitimate. They may also use fake websites or social media accounts to solicit donations.
- Investment scams: Investment scammers promise people high returns on their investments, but the investments are actually scams. The scammer may take the person’s money and disappear, or they may invest the person’s money in risky or fraudulent investments.
- Watering hole attacks: Watering hole attacks involve targeting websites or online services that are frequented by a specific group of people, such as employees of a particular company or members of a particular professional organization. Once the attacker has gained access to the website or online service, they can inject malicious code that will infect the devices of visitors to the site.
- Spear phishing: Spear phishing attacks are more targeted than traditional phishing attacks. Spear phishing attacks involve sending fraudulent emails to specific individuals, such as high-level executives or employees with access to sensitive information. The emails are often tailored to the individual’s interests or job responsibilities, making them more likely to be convincing.
- Whaling: Whaling attacks are a type of spear phishing attack that targets high-level executives, such as CEOs and CFOs. The goal of whaling attacks is to trick the executive into authorizing a financial transaction or revealing sensitive information.
- Vishing: Vishing attacks are social engineering attacks that are carried out over the phone. Vishing scammers typically impersonate a legitimate organization, such as a bank or government agency. They may claim that the victim’s account has been compromised or that they need to update their personal information. The scammer will then try to trick the victim into revealing sensitive information, such as passwords or credit card numbers.
- Smishing: Smishing attacks are social engineering attacks that are carried out via text message. Smishing scammers typically impersonate a legitimate organization, such as a bank or delivery service. They may send a text message claiming that the victim’s account has been compromised or that they have a package that needs to be delivered. The scammer will then try to trick the victim into clicking on a malicious link or revealing sensitive information.
- Piggybacking: Piggybacking attacks involve following someone into a secure area without authorization. For example, an attacker might follow someone into a building or onto a computer network.
- Social engineering malware: Social engineering malware is malware that is designed to trick users into installing it or revealing sensitive information. Social engineering malware may be disguised as a legitimate application or file, or it may be delivered via a phishing attack or other social engineering technique.
- Honey trapping: Honey trapping involves using romantic or sexual advances to gain someone’s trust. Once the attacker has gained the victim’s trust, they may try to blackmail them or trick them into revealing sensitive information.
- Honey potting: Honey potting involves creating a fake website or online service that is designed to attract victims. Once the victim has visited the website or online service, the attacker can try to infect their device with malware or steal their personal information.
- Baiting and switching: Baiting and switching involves advertising a product or service at a very attractive price, but then giving the customer something different when they try to purchase it. Baiting and switching is often used in online scams, but it can also be used in brick-and-mortar stores.
- Scareware: Scareware is a type of malware that attempts to scare users into installing it or paying for unnecessary services. Scareware may display fake error messages or warnings, or it may lock users out of their devices until they pay a fee.
- Pharming: Pharming is a type of attack that redirects users to a fake website without their knowledge. Phishing websites are often designed to look like legitimate websites, such as the websites of banks or government agencies. Once the user has been redirected to the fake website, the attacker can try to steal their personal information or infect their device with malware.
- Social engineering attacks against businesses: Social engineering attacks can also be used to target businesses. For example, attackers may try to trick employees into revealing sensitive information, such as passwords or customer data. Attackers may also try to trick employees into installing malware on their computers or transferring money to fraudulent accounts.
Social Engineering in Marketing & Advertising
Social engineering traps, attacks, or scams in marketing and advertising often exploit psychological tactics to manipulate consumers. Here’s a list of such tactics:
- Clickbait: Sensational headlines or images are used to lure users into clicking on a link, which often leads to misleading or irrelevant content.
- Fake Product Reviews: Fake reviews are posted to boost the reputation of a product or service, leading consumers to make purchasing decisions based on false information.
- Bait-and-Switch: Attractive offers are presented to attract customers, but when they engage, they are redirected to a different, less desirable product or service.
- False Urgency: Marketers create a sense of urgency by claiming limited-time offers or limited availability to pressure consumers into making quick decisions.
- Misleading Claims: Exaggerated or misleading claims about a product’s benefits or features are used to deceive customers.
- False Discounts: Marketers inflate the original price of a product to make it seem like a significant discount is being offered.
- Phishing Emails: Fraudulent emails are sent, often impersonating trusted brands or companies, to trick recipients into revealing personal information or making purchases.
- Influencer Scams: Fake influencers are used to endorse products or services, misleading consumers into thinking they are credible endorsements.
- Free Trial Traps: Companies offer free trials but require credit card information upfront, making it difficult for consumers to cancel before being charged.
- Subscription Traps: Consumers are unknowingly signed up for recurring subscriptions that are hard to cancel.
- Cookie Tracking: Websites use cookies to track users’ online behavior without their consent, often for targeted advertising.
- Social Media Scams: Deceptive ads or posts on social media platforms promote fake products or services, often using attractive images.
- Impersonation of Trusted Brands: Fraudsters create fake websites or ads that closely resemble trusted brands to deceive consumers.
- Gamification Scams: Marketers use addictive games or quizzes to collect personal data or encourage purchases.
- Native Advertising Deception: Ads that resemble editorial content are used to blur the lines between advertising and genuine content.
- False Guarantees: Companies offer money-back guarantees or risk-free trials that are difficult to claim or come with hidden conditions.
- Data Harvesting: Apps or surveys collect excessive personal data under the guise of providing a service or offer.
- Auto-Opt-Ins: Users are automatically opted into email lists or other communications without their consent.
- Fake Testimonials: Fictitious testimonials or endorsements are used to build trust.
- Unsubscribing Difficulties: Marketers make it intentionally challenging for consumers to unsubscribe from email lists.
- Impersonation of Authority Figures: Ads may impersonate experts, doctors, or celebrities to lend credibility to a product or service.
- Behavioral Targeting: Advertisers track users’ online behavior and target them with personalized ads without their explicit consent.
- Adware and Malvertising: Malicious ads or software are used to infiltrate users’ devices or compromise their security.
- Overpromising Results: Marketers exaggerate the potential benefits of a product or service to encourage sales.
- Telemarketing Scams: Unscrupulous telemarketers use high-pressure tactics and false claims to sell products or services.
- Robocalling: Automated calls deliver recorded messages to target consumers, often for fraudulent purposes.
- Phantom Merchants: Non-existent sellers or merchants are used to deceive consumers into making online purchases.
- Geo-Targeting Scams: Marketers use location data to display misleading offers tailored to a specific geographic area.
- Ad Fraud: Fraudulent clicks or impressions are generated to inflate ad metrics and costs for advertisers.
- Subscription Confirmation Deception: Users are tricked into subscribing or purchasing by unclear or deceptive subscription confirmation buttons.
Social Engineering By Categories
Social engineering attacks and scams come in various forms and are constantly evolving. Here’s a list of 60 known social engineering attack or scam types that fraudsters use to defraud individuals and businesses:
Exploiting Scam/Fraud/Crime Victims:
- Impersonating Support Groups
- Fake Investigation/Private Investigator Scams
- Fake Law Enforcement Investigation Scams
- Money Recovery Scams
- Cryptocurrency Tracing Scams
- Scammer Arrest Scams
- Court Ordered Restitution Scams
- Scammer Treat Scams
- Victim Sextortion Scams
- Victim Exposure Scams
- Threats of Physical Violence Scams
- Victim Travel Enticement
- Fake Marriage Scams
- Victim Blackmail Scams (dozens of Variants)
Phishing Scams:
- Email Phishing
- Spear Phishing
- Whaling (Targeting High-Profile Individuals)
- Vishing (Voice Phishing)
- Smishing (SMS Phishing)
- Tabnabbing (Exploiting Browser Tabs)
- Clone Phishing (Cloning Legitimate Emails)
- Invoice Phishing
Manipulative Impersonation:
- Relationship/Romance Scams/Online Dating Scams
- CEO Fraud/Business Email Compromise (BEC)
- Tech Support Scams
- Fake IT Department Calls
- Impersonating Government/Authorities (Police, IRS)
- Social Media Impersonation
- Catfishing (Creating Fake Online Identities – but not to scam, usually in am online dating context)
- Charity Impersonation Scams
- Fake Job Offers
- Online Marketplace Scams
- Bank Impersonation Scams
Pretexting and Posing as Trusted Entities:
- Pretexting (Creating False Scenarios)
- Fake Customer Support
- Fake Surveys and Questionnaires
- Utility Company Scams
- Bank Account Verification Scams
- Government Grant Scams
- Lottery and Prize Scams
- IRS Refund Scams
- Fake Investment Opportunities
- Loan Scams
Manipulating Human Psychology:
- Fear-Based Scams
- Urgency and Scarcity Scams
- Authority Exploitation
- Reciprocity (Promising Something in Return)
- Flattery Scams
- Social Validation (Using Social Proof)
- Psychological Manipulation via Social Media
- Emotional Blackmail
- Guilt-Tripping
- Victim Card
- Money Mules
Baiting and Malware Delivery:
- Downloadable Content Scams
- USB Drops (Leaving Infected USBs)
- Free Wi-Fi Scams
- Malvertising (Malicious Ads)
- Watering Hole Attacks (Compromising Trusted Websites)
- Clickjacking (Hiding Malicious Clicks)
- Ransomware Attacks
- Trojan Horse Attacks
- Keyloggers
- Spyware and Adware
Physical Social Engineering:
- Tailgating (Unauthorized Access to Buildings)
- Dumpster Diving (Searching for Sensitive Information)
- Shoulder Surfing (Stealing Information Over Shoulders)
- Impersonating Employees
- Eavesdropping
- Badge Cloning
- Elicitation (Gathering Information through Conversation)
- Reverse Social Engineering
- Piggybacking (Unauthorized Entry with Authorized Personnel)
- Physical Intrusions
Online Deception:
- Fake Social Media Profiles
- Impersonation of Trusted Brands
- Spoofed Websites (Mirror Sites)
- URL Padding (Adding Fake Characters to URLs)
- Credential Harvesting
- Credential Stuffing Attacks
- Credential Phishing (Collecting Login Details)
- Pharming (Redirecting Website Traffic)
- Man-in-the-Middle (MITM) Attacks
- Browser Hijacking
Email Manipulation:
- Email Spoofing
- Reply-to Attacks
- Domain Spoofing
- Display Name Deception
- Sender Policy Framework (SPF) Spoofing
- Email Bombs (Overwhelming Inboxes)
- Malicious Attachments
- Macro-Based Attacks
- Waterhole Email Attacks
- Business Email Impersonation
Psychological Exploitation:
- Confidence Scams
- Impersonation of Coworkers
- Family Emergency Scams
- Online Gaming Scams
- Friendship and Relationship Scams
- Fake Psychic Readings
- Fortune Telling Scams
- Fake Charities and Crowdfunding
- Psychic Healing Scams
- Emotional Manipulation via Text
Manipulating Urgency and Curiosity:
- Lottery Winnings Notifications
- Fake Security Alerts
- Account Compromise Alerts
- Prize Draw Scams
- Urgent Package Delivery Scams
- Fake Virus Alerts
- Data Breach Notifications
- Suspended Account Scams
- “Your Account Will Be Deleted” Messages
- “Secret Revealed” Scams
Scare Tactics:
- Fake Kidnapping Scams
- Hitman Threats
- Blackmail and Sextortion
- Fake Legal Threats
- IRS Tax Scams
- Threats of Criminal Charges
- False Medical Diagnosis
- “Compromising” Videos or Photos
- Fake Accusations of Misconduct
- Job Termination Threats
Manipulating Compassion and Empathy:
- Disaster Relief Scams
- Charity Scams After Tragedies
- Sick Relative Scams
- Orphanage Donation Scams
- Posing as Disabled Individuals
- Feigning Homelessness
- Posing as Veterans
- Pet Adoption Scams
- Fake Medical Treatment Requests
- “Help Me Escape” Scams
Manipulation of Trust and Authority:
- Fake Law Enforcement Calls
- Impersonating Government Agencies
- Fake IRS Audit Calls
- Utility Company Scams
- Tech Support Impersonation
- Bank Fraud Alerts
- Impersonating HR Departments
- Phony Legal Notices
- Government Grant Scams
- Jury Duty Scams
Trust-Based Scams:
- Friendship Investment Scams (Pig Butchering Scams)
- Pyramid Schemes
- Multi-Level Marketing (MLM) Scams
- Fake Investment Seminars
- Real Estate Investment Scams
- Ponzi Schemes
- Binary Options Scams
- High-Yield Investment Programs (HYIP)
- Pump-and-Dump Stock Scams
- Offshore Account Promotions
Impersonation via Phone and Email:
- Voicemail Phishing (Vishing)
- Caller ID Spoofing
- Robocalls with Urgent Messages
- Business Voicemail Scams
- Impersonation of Healthcare Providers
- Supplier Impersonation Scams
- Vendor Payment Diversion
- Invoice Redirection Fraud
- CEO Impersonation Scams
- Payroll Diversion Fraud
Psychological Manipulation Tactics:
- Gaslighting
- Guilt-Tripping Scams
- Flattery and Praise Scams
- False Friendship Scams
- Fake Accolades and Awards
- Love Bombing/Amygdala Hijacking
- Fake Success Stories
- Fear of Missing Out (FOMO)
- The “Trust Me” Scam
- Exploiting Reciprocity
Misinformation and Fake News:
- Disinformation/Urban Legend Campaigns
- Social Media Clickbait Scams
- Fake Health Cures and Remedies
- Misleading Product Claims
- False Celebrity Endorsements
- Fake News Websites
- COVID-19 Scams
- Misleading Weight Loss Ads
- Get-Rich-Quick Schemes
- Fake Expert Opinions
Exploiting Job Seekers:
- Fake Job Postings
- Work-From-Home Scams
- Resume Fraud
- Advance-Fee Employment Scams
- Identity Theft via Job Applications
- Fake Recruiting Agencies
- Training Fee Scams
- Pay-for-Job Offers
- Immigration Job Scams
- Scholarship and Education Scams
Impersonation via Communication:
- Impersonation of Religious Figures
- Fake Psychic Readings
- Clairvoyance Scams
- Mediumship Scams
- Fortune Telling Scams
- Psychic Healing Scams
- Impersonating Celebrities
- Fake Social Media Influencers
- Political Impersonation Scams
- Impersonating Customer Service
Exploiting Fears and Health Concerns:
- Health Insurance Scams
- Fake Health Products
- Miracle Cure Scams
- Fear-Based Medical Scams
- Weight Loss Product Scams
- Impersonation of Doctors
- Medical Billing Scams
- COVID-19 Vaccine Scams
- Health Research Participation Scams
- Genetic Testing Scams
Exploiting Trust in Educational Institutions:
- Fake Diplomas and Certifications
- Diploma Mill Scams
- Fake Online Universities
- Phony Degree Verification Services
- Student Loan Scams
- Scholarship Fraud
- Academic Cheating Services
- Fake Tutoring Programs
- Homework Help Scams
- Fake Study Abroad Programs
Manipulating Homeowners and Renters:
- Home Improvement Scams
- Fake Landlord Rental Scams
- Apartment Rental Scams
- Property Management Impersonation
- Rental Deposit Scams
- Foreclosure Rescue Scams
- Real Estate Agent Impersonation
- Investment Property Scams
- Vacation Rental Frauds
- Timeshare Resale Scams
Exploiting Social Networking:
- Fake Friend Requests
- Catfishing on Social Media
- Social Media Contests Scams
- Impersonating Friends or Family
- Influencer Impersonation
- False Social Media Surveys
- Phishing via Social Media DMs
- Social Media Impersonation of Brands
- Phony Event Invitations
- Social Media Engagement Scams
Manipulating Fear of Legal Consequences:
- Lawsuit Threats
- Jury Duty Scams
- Arrest Warrant Scams
- Impersonating Legal Authorities
- Threats of Child Protective Services
- Defamation and Lawsuit Extortion
- Legal Document Forgery Scams
- Fake Subpoenas
- Fake Process Servers
- Impersonating Private Investigators
Manipulating Trust in Tech and Gadgets:
- Fake Tech Support Calls
- Tech Product Warranty Scams
- Fake Software Updates
- Impersonating Tech Companies
- Smartphone Cloning Scams
- Fake Tech Forums and Communities
- Tech Investment Frauds
- Fake Tech Gadgets for Sale
- Impersonating Tech Repair Services
- Phony IT Consultancy Services
Exploiting Vulnerabilities in Online Marketplaces:
- Fake Online Market Listings
- Counterfeit Goods Scams
- Escrow Service Impersonation
- Non-Delivery of Goods Scams
- Auction Fraud
- Merchandise Reshipping Scams
- Impersonating Online Sellers
- Advance-Fee Payment Scams
- Vehicle Sale Scams
- Online Rental Property Frauds
Manipulating Compassion for Animals:
- Pet Adoption Scams
- Fake Animal Welfare Organizations
- Puppy Mill Scams
- Pet Shipping Frauds
- Charity Scams for Animal Rescue
- Misrepresentation of Animal Breeds
- Impersonating Veterinary Services
- Fake Animal Shelter Donations
- Exotic Animal Sales Scams
- Endangered Species Exploitation
Exploiting Fear of Identity Theft:
- Identity Theft Protection Scams
- Social Security Number Scams
- Impersonating Credit Monitoring Services
- Fake Credit Repair Services
- Phishing for Personal Information
- Identity Theft Reporting Scams
- Impersonating Credit Bureaus
- Tax Identity Theft Scams
- Medical Identity Theft
- Child Identity Theft Scams
Manipulating Fear of Natural Disasters/Climate Change:
- Disaster Relief Donation Scams
- Impersonating FEMA and Red Cross
- Fake Emergency Alerts
- Natural Disaster Insurance Scams
- Hurricane Preparedness Scams
- Wildfire Evacuation Frauds
- Earthquake Safety Scams
- Tornado Shelter Scams
- Flood Prevention Scams
- Emergency Generator Scams
- Climate Change Fraud
Exploiting Fear of Immigration Issues:
- Immigration Fraud Scams
- Impersonating Immigration Authorities
- Visa Lottery Scams
- Asylum Seeker Exploitation
- Fake Green Card Services
- Marriage Fraud Scams
- Impersonating Immigration Lawyers
- Human Trafficking Deceptions
- Visa Overstay Threats
- Immigration Detention Scams
Exploiting Fear of Health Issues:
- Health Scare Scams
- Fake Medical Studies
- Online Prescription Drug Scams
- Impersonating Health Insurers
- Health Insurance Cancellation Threats
- Medical Device Fraud
- Dental and Orthodontic Scams
- Impersonating Health Clinics
- Alternative Medicine Scams
- Weight Loss Surgery Scams
Manipulating Fear of Legal Trouble:
- Immigration Consequences Scams
- Impersonating Legal Aid Services
- Fake Legal Documents
- Court Summons Scams
- Impersonating Lawyers
- Threats of Custody Battles
- Child Support Payment Scams
- Divorce Settlement Frauds
- Marriage Annulment Scams
- Fake Lawsuits and Settlements
Exploiting Fear of Tax Issues:
- IRS Tax Debt Scams
- Impersonating Tax Agencies
- Threats of Tax Audits
- Fake Tax Refunds
- Tax Evasion Accusations
- Tax Preparer Fraud
- Tax Shelter Scams
- Inheritance Tax Scams
- Property Tax Frauds
- Fake Tax Exemptions
Manipulating Fear of Religious Consequences:
- Religious Blackmail
- Impersonating Religious Leaders
- Threats of Excommunication
- Guilt-Tripping through Religion
- Religious Cult Recruitment
- Offering Fake Religious Blessings
- Divine Retribution Scams
- False Faith Healing
- Fake Religious Pilgrimages
- Religious Charity Scams
Exploiting Fear of Environmental Issues:
- Greenwashing Scams (Fake Eco-Friendly Products)
- Impersonating Environmental Organizations
- Fake Carbon Offset Programs
- Pollution Control Scams
- Renewable Energy Investment Frauds
- Climate Change Charity Scams
- Fake Environmental Awards
- Phony Eco-Friendly Certifications
- Impersonating Eco-Activists
- Environmental Disaster Donation Scams
Manipulating Fear of Legal Documents:
- Impersonating Notaries
- Fake Legal Contracts
- Loan Agreement Scams
- Business Partnership Frauds
- Real Estate Purchase Scams
- Divorce Papers Manipulation
- False Child Custody Documents
- Adoption Scams
- Marriage License Frauds
- Impersonating Court Clerks
- Home Ownership Title Fraud
Exploiting Fear of Personal Safety:
- Personal Threat Scams
- Home Invasion Threats
- Impersonating Stalkers
- Hostage Scams
- Carjacking Threats
- Kidnapping Threats
- Impersonating Abusers
- Cyberbullying Threats
- Threats of Physical Harm
- Online Harassment Threats
Manipulating Fear of Natural Phenomena:
- Weather Disaster Scams
- Impersonating Meteorologists
- Storm and Tornado Threats
- Earthquake Prediction Scams
- Tsunami Threats
- Fake Flood Warnings
- Impersonating Seismologists
- Volcanic Eruption Threats
- Hurricane Tracking Scams
- Impersonating Climate Scientists
Exploiting Fear of Social Rejection:
- Social Exclusion Threats
- Friendship Termination Scams
- Impersonating Friends or Family Members
- Fake Social Media Shaming
- Impersonating Influential Friends
- Social Media Account Hacking Threats
- Online Reputation Damage Threats
- Job Termination Threats
- Impersonating Coworkers
- Threats of Ending Romantic Relationships
Manipulating Fear of Family Issues:
- Family Disownment Threats
- Child Custody Threats
- Impersonating Family Members
- Inheritance Disputes
- Sibling Rivalry Exploitation
- Parental Neglect Accusations
- Impersonating Child Protective Services
- Grandparent Scams
- Adoption Termination Threats
- Threats of Spousal Separation
Exploiting Fear of Isolation:
- Impersonating Support Groups
- Threats of Losing Friends
- Impersonating Online Communities
- Threats of Social Isolation
- Loneliness Exploitation
- Impersonating Mental Health Professionals
- False Support Hotlines
- Threats of Abandonment
- Impersonating Therapists
- Cult Recruitment Threats
Manipulating Fear of Economic Loss:
- Impersonating Employers
- Threats of Job Loss
- Impersonating Debt Collectors
- Fake Bill Collection Threats
- Threats of Financial Ruin
- Impersonating Tax Agencies
- Business Closure Threats
- Impersonating Bank Officials
- Investment Portfolio Threats
- Threats of Asset Seizure
Exploiting Fear of Reputation Damage:
- Impersonating PR Firms
- Threats of Public Embarrassment
- Blackmail with Sensitive Information
- Impersonating Journalists
- Fake News Article Threats
- Impersonating Whistleblowers
- Reputation-Tarnishing Threats
- Impersonating Online Reviewers
- False Defamation Claims
- Social Media Smear Campaigns
Avoiding Social Engineering
Here are some tips on how to avoid social engineering traps:
- Avoid impulsive actions. Social engineering is designed to get you to respond instantly without thinking. By avoiding impulsive actions you can give yourself time to think it through.
- Be suspicious of unsolicited contact. If you receive an email, phone call, or text message from someone you don’t know, be wary. Attackers often try to contact people out of the blue in order to catch them off guard.
- Don’t give out personal information. Never give out your personal information to someone you don’t know and trust. This includes things like your name, address, phone number, Social Security number, and credit card number.
- Be wary of requests for money or gifts. If someone asks you for money or gifts, especially if you don’t know them well, be wary. Attackers often try to trick people into giving them money or gifts by pretending to be someone they’re not.
- Do your research. If you’re unsure about the legitimacy of something, do your research. Look up the company or organization online and see if they have a good reputation. You can also check with friends and family to see if they’ve heard of the company or organization.
- Use strong passwords and enable two-factor authentication. Strong passwords and two-factor authentication can help to protect your accounts from being hacked. Use different passwords for different accounts and make sure your passwords are strong and difficult to guess. Two-factor authentication adds an extra layer of security to your accounts by requiring you to enter a code from your phone in addition to your password when you log in.
- Be careful about what information you share online. Don’t overshare personal information on social media or other websites. Be careful about what links you click on and what attachments you open.
Here are some additional Social Engineering Tips:
- Educate yourself about social engineering attacks. The more you know about social engineering attacks, the better equipped you will be to spot them. There are many resources available online and in libraries that can teach you about social engineering attacks.
- Be skeptical. If something sounds too good to be true, it probably is. Be skeptical of any offers or claims that seem too good to be true.
- Take your time. Don’t feel pressured to make a decision right away. Take your time to think about any offer or claim before you take any action.
- Trust your intuition. If something feels wrong, it probably is. If you have a bad feeling about something, don’t do it.
SCARS Resources:
- Getting Started Right: ScamVictimsSupport.org
- Sextortion Scam Victims: Sextortion Victims Support – The Essentials (scamvictimssupport.org)
- For New Victims of Relationship Scams newvictim.AgainstScams.org
- Subscribe to SCARS Newsletter newsletter.againstscams.org
- Sign up for SCARS professional support & recovery groups, visit support.AgainstScams.org
- Join our Scam Survivors United Chat & Discussion Group facebook.com/groups/scam.survivors.united
- Find competent trauma counselors or therapists, visit counseling.AgainstScams.org
- Become a SCARS Member and get free counseling benefits, visit membership.AgainstScams.org
- Report each and every crime, learn how to at reporting.AgainstScams.org
- Learn more about Scams & Scammers at RomanceScamsNOW.com and ScamsNOW.com
- Scammer photos ScammerPhotos.com
- SCARS Videos youtube.AgainstScams.org
- Self-Help Books for Scam Victims are at shop.AgainstScams.org
- Donate to SCARS and help us help others at donate.AgainstScams.org
- Worldwide Crisis Hotlines: https://blog.opencounseling.com/suicide-hotlines/
Other Cyber Resources
- Block Scam Domains: Quad9.net
- Global Cyber Alliance ACT Cybersecurity Tool Website: Actionable Cybersecurity Tools (ACT) (globalcyberalliance.org) https://act.globalcyberalliance.org/index.php/Actionable_Cybersecurity_Tools_(ACT)_-_Simplified_Cybersecurity_Protection
- Wizer Cybersecurity Training – Free Security Awareness Training, Phishing Simulation and Gamification (wizer-training.com)
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment below!
Do You Need Support?
Get It Now!
SCARS provides the leading Support & Recovery program for relationship scam victims – completely FREE!
Our managed peer support groups allow victims to talk to other survivors and recover in the most experienced environment possible, for as long as they need. Recovery takes as long as it takes – we put no limits on our support!
SCARS is the most trusted support & education provider in the world. Our team is certified in trauma-informed care, grief counseling, and so much more!
To apply to join our groups visit support.AgainstScams.org
We also offer separate support groups for family & friends too.
Become a
SCARS STAR™ Member
SCARS offers memberships in our STAR program, which includes many benefits for a very low annual membership fee!
SCARS STAR Membership benefits include:
- FREE Counseling or Therapy Benefit from our partner BetterHelp.com
- Exclusive members-only content & publications
- Discounts on SCARS Self-Help Books Save
- And more!
To learn more about the SCARS STAR Membership visit membership.AgainstScams.org
To become a SCARS STAR Member right now visit join.AgainstScams.org
To Learn More Also Look At Our Article Catalogs
Scam & Crime Types
More SCARS
- ScamsNOW Magazine – ScamsNOW.com
- ContraEstafas.org
- ScammerPhotos.com
- AnyScam.com – reporting
- AgainstScams.org – SCARS Corporate Website
- SCARS YouTube Video Channel














There are so many ways to get scammed it’s scary and overwhelming.