2016 Internet Crime Report
The United States Department of Justice’s Internet Crime Complaint Center (IC3) Releases Their Annual Report Highlighting Trends in Internet Crime
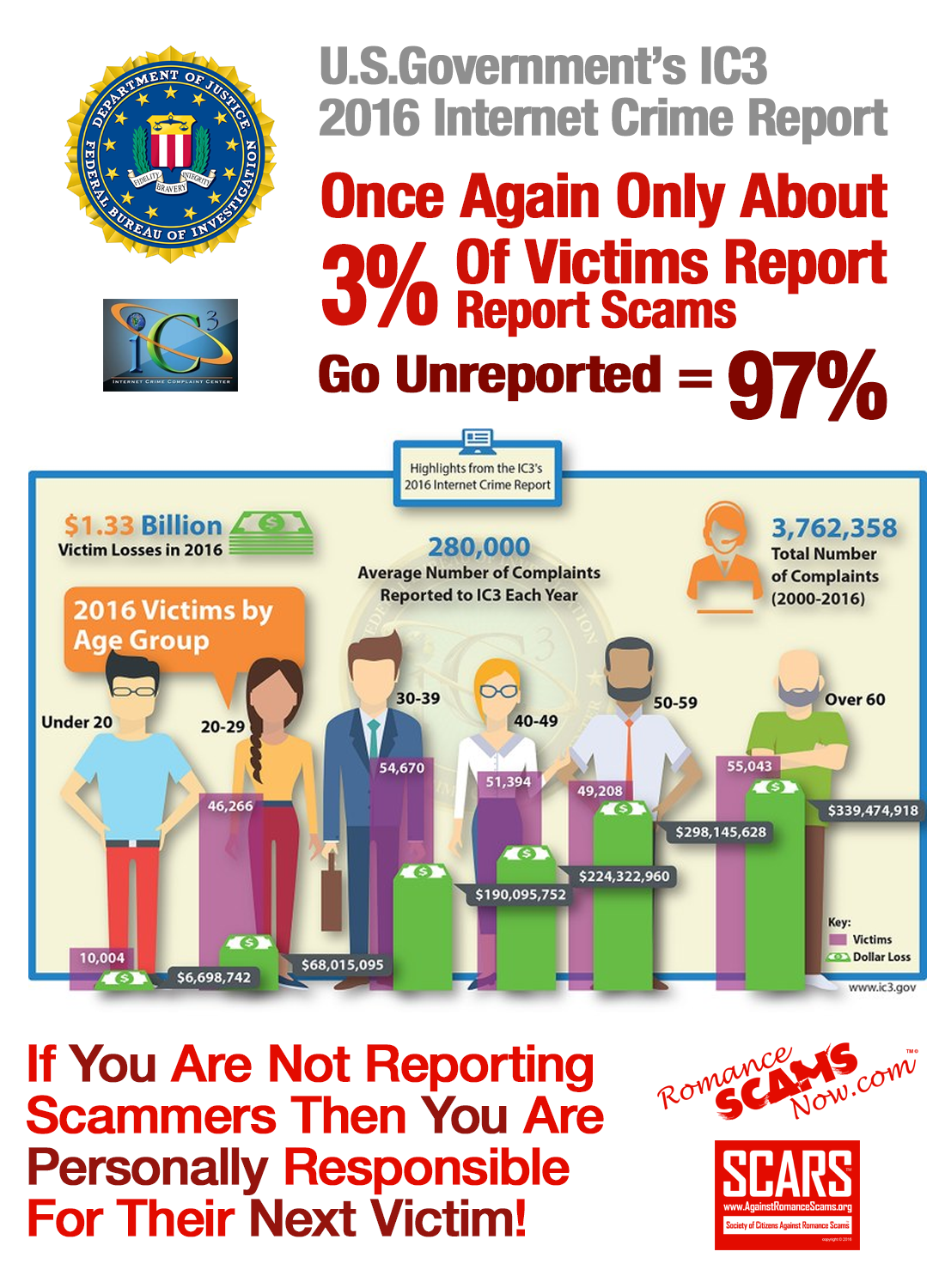
As usual, only about 3% of victims will report their crime to the government. So the result is that 97% of the numbers are unknown to them.
The result of the constant under-reporting by victims is that government neither fully understands the scope and magnitude of these crime, and they also do not know how to prioritize resources to stop them. The result is that every victim that fails to report these crimes is further enabling the scammers and online criminals to go after another person.
Think about that for a moment?
By not reporting the crime YOU are allowing the scammers and the criminals to get away with it.
Here are the highlights from the IC3 Report:
Giving someone access to your computer is like giving out a key to your front door. A computer can have your bank account information, family photos, and other private documents and data—information that fraudsters would like to steal. That’s why tech support fraud has become a significant trend in online crime, according to the 2016 Internet Crime Report from the FBI’s Internet Crime Complaint Center (IC3).
In tech support fraud cases, criminals convince unsuspecting victims to provide remote access to their computer by calling and posing as tech support personnel from a legitimate company. The criminal can then simply charge your credit card for a fake anti-virus product, or, in more sinister situations, they can steal your personal information or install malware. More than 10,000 incidents of tech support fraud were reported to the IC3 in 2016, with victims losing nearly $8 million. Though anyone can be a victim, older computer users are the most vulnerable targets.
“They’ll trick you into letting them into your computer,” said IC3 Unit Chief Donna Gregory. “You open the door and allow them in. You may think you’re just watching them install a program to get rid of a virus, but they are really doing a lot of damage behind the scenes.”
In addition to tech support fraud, the other major fraud categories last year were business e-mail compromise, ransomware, and extortion.
The IC3 receives complaints on a variety of Internet scams and crimes, and it has received more than 3.7 million complaints since it was created in 2000. In 2016, the IC3 received a total of 298,728 complaints with reported losses in excess of $1.3 billion. The IC3 uses the information from public complaints to refer cases to the appropriate law enforcement agencies and identify trends. The IC3’s extensive database is also available to law enforcement. Internet users should report any Internet fraud to IC3, no matter the dollar amount. Additional data helps the FBI and law enforcement gain a more accurate picture of Internet crime.
The IC3 publishes the Internet Crime Report annually to increase public awareness of current trends in Internet crime. For this report, the IC3 has also created a separate state-by-state breakdown that allows users to select their state from a dropdown menu so they can review local trends in Internet crime. The top states for reported dollar amounts lost to Internet fraud in 2016 were California ($255 million), New York ($106 million), and Florida ($89 million).
Though Internet crime is a serious threat, there are ways to help keep yourself safe online. The IC3 recommends computer users update their anti-virus software and operating system. Additionally, the Internet is an especially important place to remember the old adage: If it sounds too good to be true, it probably is.
“Be aware of what you are clicking on and also what you’re posting on social media. Always lock down your social media accounts as much as possible,” Gregory said. “Try to use two factor authentication, and use safe passwords or things more difficult to guess. The tougher the password, the harder it is for someone to crack.”
If you would like to read the actual PDF report CLICK HERE »
For more information or to submit a complaint, visit www.ic3.gov AND also report it at www.Anyscam.com or this website too!



Leave A Comment