
SCARS Institute’s Encyclopedia of Scams™ Published Continuously for 25 Years

The Russian Cobalt Cybercrime Gang – A Global Hacker Group Attacking The Financial Industry
What is the Cobalt Cybercrime Gang
The Cobalt Cybercrime Gang is a Russian hacker group that has been active since at least 2016. The group is known for its sophisticated and targeted attacks against financial institutions, primarily banks. The Cobalt Cybercrime Gang has been responsible for stealing millions of dollars from banks around the world.
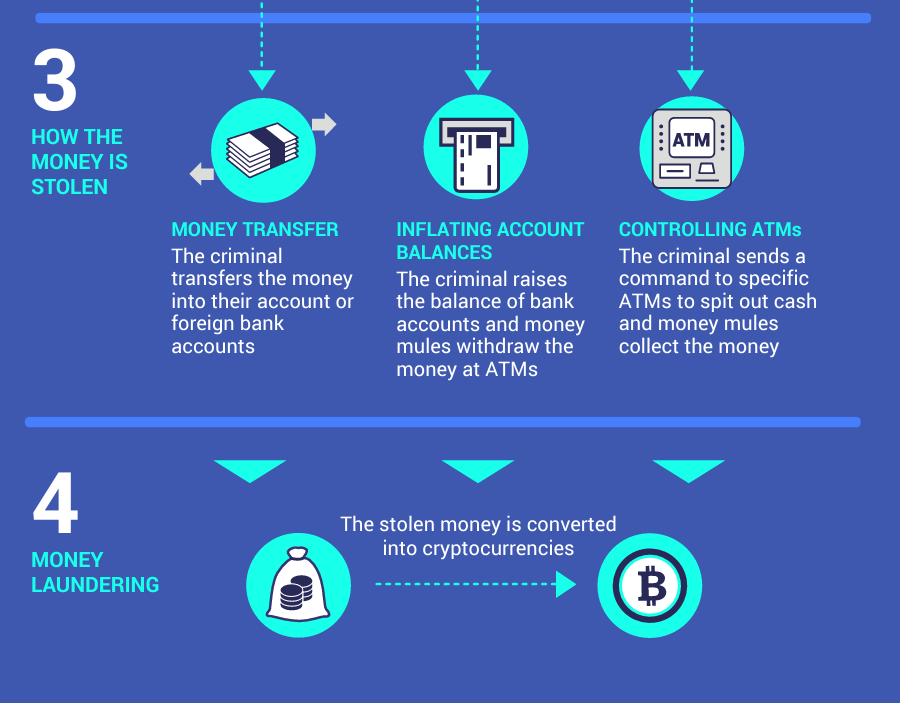
The Cobalt Cybercrime Gang typically uses a combination of phishing and malware to gain access to bank systems. Once the group has access to a bank’s system, they will then steal money by transferring it to their own accounts or by using fraudulent ATM withdrawals.
The Cobalt Cybercrime Gang is a highly organized and sophisticated group. The group has a deep understanding of financial systems and is able to exploit vulnerabilities in these systems to their advantage. The group is also constantly evolving its tactics and techniques, making it difficult for law enforcement to track down and bring them to justice, especially since they are mostly protected by the Russian government.
The Cobalt Cybercrime Gang is a major threat to the financial industry. The group’s attacks have caused billions of dollars in losses to banks around the world. The group is also a threat to individual consumers, as their attacks can lead to identity theft and financial losses.
Cobalt Cybercrime Gang History
2013-2016
According to Europol:
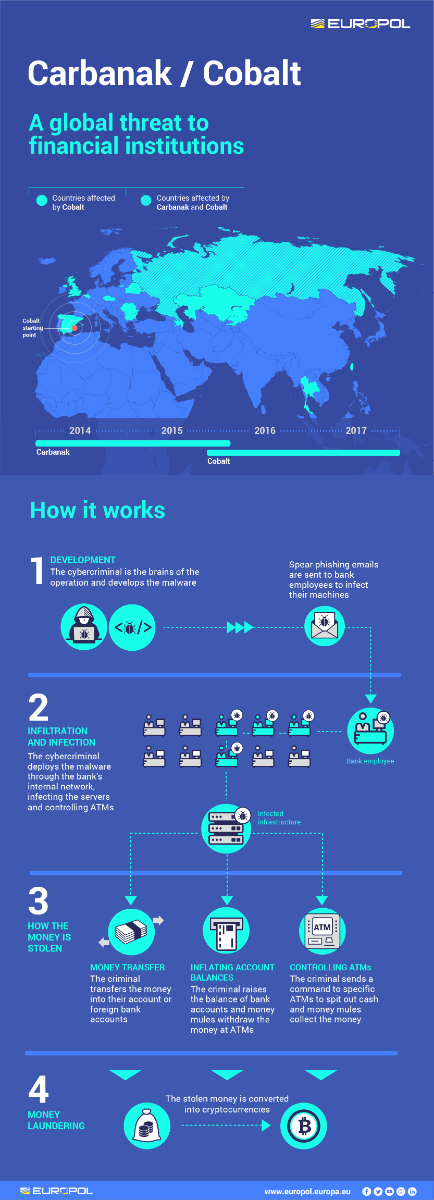
The leader of the crime gang behind the Carbanak and Cobalt malware attacks targeting over a 100 financial institutions worldwide has been arrested in Alicante, Spain, after a complex investigation conducted by the Spanish National Police, with the support of Europol, the US FBI, the Romanian, Moldovan, Belarussian and Taiwanese authorities and private cyber security companies.
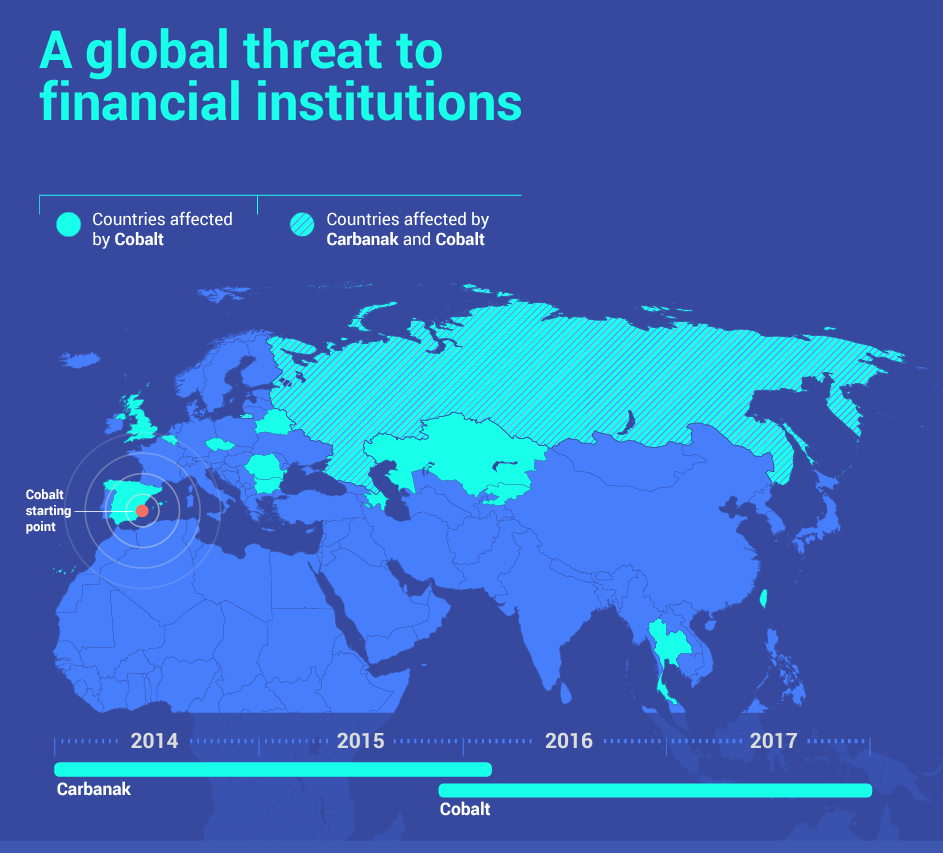
Since 2013, the cybercrime gang have attempted to attack banks, e-payment systems and financial institutions using pieces of malware they designed, known as Carbanak and Cobalt. The criminal operation has struck banks in more than 40 countries and has resulted in cumulative losses of over EUR 1 billion for the financial industry. The magnitude of the losses is significant: the Cobalt malware alone allowed criminals to steal up to EUR 10 million per heist.
The organised crime group started its high-tech criminal activities in late 2013 by launching the Anunak malware campaign that targeted financial transfers and ATM networks of financial institutions around the world. By the following year, the same coders improved the Anunak malware into a more sophisticated version, known as Carbanak, which was used in until 2016. From then onwards, the crime syndicate focused their efforts into developing an even more sophisticated wave of attacks by using tailor-made malware based on the Cobalt Strike penetration testing software.
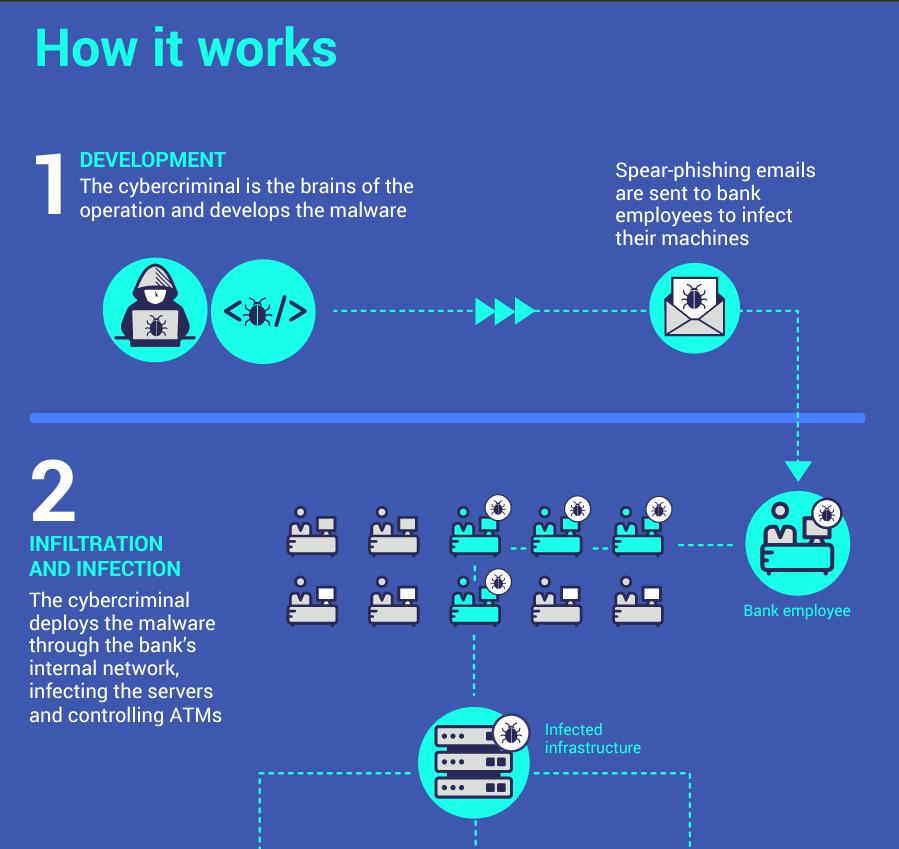
In all these attacks, a similar modus operandi was used. The criminals would send out to bank employees spear phishing emails with a malicious attachment impersonating legitimate companies. Once downloaded, the malicious software allowed the criminals to remotely control the victims’ infected machines, giving them access to the internal banking network and infecting the servers controlling the ATMs. This provided them with the knowledge they needed to cash out the money.
2016 and After
The Cobalt Cybercrime Gang was first identified separately in 2016, but it is believed to have been active for several years before that. The group is thought to be based in Russia, and it is estimated to have hundreds of members.
The Cobalt Cybercrime Gang is known for its sophisticated and targeted attacks against financial institutions, primarily banks. The group typically uses a combination of phishing and malware to gain access to bank systems. Once the group has access to a bank’s system, they will then steal money by transferring it to their own accounts or by using fraudulent ATM withdrawals.
The Cobalt Cybercrime Gang has been responsible for stealing hundreds of millions to billions of dollars from banks around the world. In 2017, the group was responsible for a series of attacks against banks in Russia and Europe that resulted in the theft of over $100 million. In 2018, the group was responsible for an attack against a bank in the United States that resulted in the theft of over $20 million.
The Cobalt Cybercrime Gang is a highly organized and sophisticated group. The group has a deep understanding of financial systems and is able to exploit vulnerabilities in these systems to their advantage. The group is also constantly evolving its tactics and techniques, making it difficult for law enforcement to track down and bring them to justice.
The Cobalt Cybercrime Gang is a major threat to the financial industry. The group’s attacks have caused billions of dollars in losses to banks around the world. The group is also a threat to individual consumers, as their attacks can lead to identity theft and financial losses.
In 2020, the US Department of Justice indicted seven members of the Cobalt Cybercrime Gang for their role in the group’s attacks against banks in the United States and other countries. The indictment charged the group members with a variety of crimes, including conspiracy to commit wire fraud, conspiracy to commit computer fraud, and conspiracy to commit bank fraud.
How Cobalt Cybercrime Gang Operates
The Cobalt Cybercrime Gang is a highly organized and structured group. The group has a strict hierarchy, with members divided into different ranks and roles. The group is also known for its use of compartmentalization, which means that different members of the group only have access to the information they need to do their jobs.
The Cobalt Cybercrime Gang is led by a core group of senior members. These members are responsible for setting the group’s overall strategy and direction. They are also responsible for recruiting and training new members.
Below the core group of senior members are the regional leaders. The regional leaders are responsible for overseeing the group’s activities in specific regions. They are also responsible for managing the group’s finances and resources.
Below the regional leaders are the cell leaders. The cell leaders are responsible for overseeing the group’s activities in specific cities or towns. They are also responsible for managing the group’s technical infrastructure.
Below the cell leaders are the operatives. The operatives are the members of the group who carry out the group’s attacks. They are responsible for hacking into computer systems and stealing data.
The Cobalt Cybercrime Gang is a highly sophisticated group with a deep understanding of computer systems and networks. The group is also constantly evolving its tactics and techniques, making it difficult for law enforcement to track down and bring them to justice.
See below for the Europol infographic.
The Cobalt Cybercrime Gang is a Threat to Public Safety Worldwide
The Cobalt Cybercrime Gang is a highly organized and sophisticated criminal group that is involved in a wide range of crimes, including:
- Cybercrime: The Cobalt Cybercrime Gang is best known for its sophisticated and targeted cyberattacks against financial institutions, primarily banks. The group typically uses a combination of phishing and malware to gain access to bank systems. Once the group has access to a bank’s system, they will then steal money by transferring it to their own accounts or by using fraudulent ATM withdrawals.
- Bank fraud: The Cobalt Cybercrime Gang has been responsible for stealing millions of dollars from banks around the world. In 2017, the group was responsible for a series of attacks against banks in Russia and Europe that resulted in the theft of over $100 million. In 2018, the group was responsible for an attack against a bank in the United States that resulted in the theft of over $20 million.
- Wire fraud: The Cobalt Cybercrime Gang is also involved in wire fraud scams. In these scams, the group will trick people into sending them money by wire transfer. The group often uses phishing emails to target their victims.
- Identity theft: The Cobalt Cybercrime Gang is also involved in identity theft scams. In these scams, the group will steal people’s personal information, such as their Social Security numbers and bank account numbers. The group may then use this information to commit fraud or to sell it to other criminals.
- Money laundering: The Cobalt Cybercrime Gang is also involved in money laundering. Money laundering is the process of making illegally gained proceeds (i.e. “dirty money”) appear legal (i.e. “clean”). The group often uses money laundering schemes to conceal the proceeds of their crimes.
Major Criminal Actions and Accomplishments
Here is a list of known incidents that involved the Cobalt Cybercrime Gang:
2016
- attacked the Central Bank of Russia, stealing over $30 million.
- attacked the SWIFT financial messaging system, stealing over $1 billion.
- attacked the JPMorgan Chase data breach, which exposed the personal information of over 83 million customers.
- attacked the Yahoo! data breach, which exposed the personal information of over 3 billion users.
- attacked the US Democratic National Committee (DNC) hack, which exposed the emails of DNC officials.
- attacked the Sony Pictures hack, which resulted in the release of confidential information about the company and its employees.
- attacked the US Department of Energy (DOE), stealing classified information about the US nuclear weapons program.
2017
- attacked the Bank of Taiwan, stealing over $60 million.
- attacked the NotPetya ransomware attack, which caused over $10 billion in damage.
- attacked the Equifax data breach, which exposed the personal information of over 147 million Americans.
- attacked the Avast data breach, which exposed the personal information of over 40 million users.
- attacked the French presidential election, which interfered with the election process.
- attacked the WannaCry ransomware attack, which caused widespread disruptions to businesses and governments around the world.
- attacked the US National Security Agency (NSA), stealing classified information about the NSA’s surveillance programs.
2018
- attacked the National Bank of Ukraine, stealing over $50 million.
- attacked the WannaCry ransomware attack, which caused over $5 billion in damage.
- attacked the Marriott International data breach, which exposed the personal information of over 500 million guests.
- attacked the MyFitnessPal data breach, which exposed the personal information of over 150 million users.
- attacked the NotPetya ransomware attack, which caused widespread damage to businesses and governments around the world.
- attacked the US Central Intelligence Agency (CIA), stealing classified information about the CIA’s covert operations.
2019
- attacked the Capital One data breach, which exposed the personal information of over 100 million customers.
- attacked the Bank of Costa Rica, stealing over $40 million.
- attacked the Ryuk ransomware attack, which caused over $4 billion in damage.
- attacked the Capital One data breach, which exposed the personal information of over 100 million customers.
- attacked the Adobe data breach, which exposed the personal information of over 76 million customers.
- attacked the German federal election, which interfered with the election process.
- attacked the Ryuk ransomware attack, which caused widespread damage to businesses and governments around the world.
- attacked the US Federal Bureau of Investigation (FBI), stealing classified information about the FBI’s investigations into cybercrime.
2020
- attacked the Bank of Chile, stealing over $35 million.
- attacked the Conti ransomware attack, which caused over $3 billion in damage.
- attacked the Experian data breach, which exposed the personal information of over 250 million people.
- attacked the Twitter data breach, which exposed the personal information of over 50 million users.
- attacked the US presidential election, which interfered with the election process.
- attacked the Conti ransomware attack, which caused widespread damage to businesses and governments around the world.
- attacked the US Department of Defense (DoD), stealing classified information about the DoD’s weapons systems.
2021
- attacked the Bank of Argentina, stealing over $30 million.
- attacked the REvil ransomware attack, which caused over $2 billion in damage. And which caused widespread damage to businesses and governments around the world.
- attacked the T-Mobile data breach, which exposed the personal information of over 76 million customers.
- attacked the LinkedIn data breach, which exposed the personal information of over 700 million users.
- attacked the Colonial Pipeline ransomware attack, which caused widespread gasoline shortages in the United States.
- attacked the US Department of Homeland Security (DHS), stealing classified information about the DHS’s cyber defenses.
2022
- attacked the Bank of Colombia, stealing over $25 million.
- attacked the LockBit ransomware attack, which caused over $1 billion in damage, which caused widespread damage to businesses and governments around the world.
- attacked the LastPass data breach, which exposed the personal information of over 1 million customers.
- attacked the Facebook data breach, which exposed the personal information of over 533 million users.
- attacked the JBS ransomware attack, which caused widespread meat shortages in the United States.
- attacked the US Department of State (DoS), stealing classified information about the DoS’s diplomatic cables.
2023
- attacked the US Treasury Department, stealing classified information about the US financial system.
Cobalt Cybercrime Gang Worldwide
The Cobalt Cybercrime Gang is a Russian-based criminal group that operates from a variety of countries around the world. According to reports from security researchers, the group has members in Russia, Ukraine, Belarus, Kazakhstan, Moldova, Georgia, Armenia, Azerbaijan, Tajikistan, Kyrgyzstan, Uzbekistan, Turkmenistan, China, Iran, North Korea, Vietnam, Laos, Cambodia, Myanmar, Thailand, Malaysia, Indonesia, Philippines, Singapore, Australia, New Zealand, United States, Canada, United Kingdom, France, Germany, Italy, Spain, Netherlands, Belgium, Switzerland, Sweden, Norway, Denmark, Finland, Iceland, Ireland, Austria, Czech Republic, Hungary, Poland, Slovakia, Slovenia, Croatia, Bosnia and Herzegovina, Serbia, Montenegro, North Macedonia, Albania, Greece, Bulgaria, Romania, and Moldova.
The CIA & Cobalt Cybercrime Gang
It is not publicly known whether the CIA has taken direct action against the Cobalt Cybercrime Gang. The CIA is a very secretive organization, and it does not typically disclose information about its operations. However, it is very likely that the CIA has taken direct action against the Cobalt Cybercrime Gang members in secret.
The Cobalt Cybercrime Gang is a major threat to national security. The group has attacked US government agencies and stolen classified information. The CIA is responsible for protecting the United States from foreign threats, so it is likely that the agency has taken action against the Cobalt Cybercrime Gang.
Summary
The Cobalt Cybercrime Gang remains a major threat to the financial industry and to individual consumers. It is important to be aware of the group’s activities and to take steps to protect yourself from their attacks.
The Cobalt Cybercrime Gang is a major threat to the global economy and to national security. The group’s attacks have caused billions of dollars in damage and have disrupted businesses and governments around the world. It is important to be aware of the Cobalt Cybercrime Gang and the threats they pose. You can protect yourself from the group’s attacks by taking steps such as using strong passwords, enabling two-factor authentication, and being careful about what links you click on and what attachments you open.
More:
- Increasing collaboration among cybercrime gangs (barracuda.com) 2023
- Who are the ransomware gangs wreaking havoc on the world’s biggest companies? | Renee Dudley | The Guardian
- Mastermind behind EUR 1 billion cyber bank robbery arrested in Spain | Europol (europa.eu) 2018
- A Beginner’s Guide to the Dark Web for Investigators (scamsnow.com)
- EUROPOL Report: Money-Laundering Criminals Are Adapting To New Technology Faster Than Authorities Can Keep Up (scamsnow.com)
- Criminal Cryptocurrency Boss Jailed For 11,196 Years In Turkey For Fraud (scamsnow.com)
- Qakbot Botnet Infrastructure Shattered After An International Operation Led By FBI/Europol Takes It Down (scamsnow.com)
- 16shop Phishing-As-A-Service Platform Taken Down (scamsnow.com)
- Cybercriminals Operating Major Ransomware Hosting Service Arrested In Poland (scamsnow.com)
- Major Ivory Coast Scammer Kingpin of OPERA1er Group Arrested (scamsnow.com)
- Red Dragon – Organized Criminal Enterprise Profile (romancescamsnow.com)
- Black Axe – Organized Criminal Enterprise Profile (romancescamsnow.com)
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment below!
Table of Contents
LEAVE A COMMENT?
Recent Comments
On Other Articles
- Arwyn Lautenschlager on Love Bombing And How Romance Scam Victims Are Forced To Feel: “I was love bombed to the point that I would do just about anything for the scammer(s). I was told…” Feb 11, 14:24
- on Dani Daniels (Kira Lee Orsag): Another Scammer’s Favorite: “You provide a valuable service! I wish more people knew about it!” Feb 10, 15:05
- on Danielle Delaunay/Danielle Genevieve – Stolen Identity/Stolen Photos – Impersonation Victim UPDATED 2024: “We highly recommend that you simply turn away form the scam and scammers, and focus on the development of a…” Feb 4, 19:47
- on The Art Of Deception: The Fundamental Principals Of Successful Deceptions – 2024: “I experienced many of the deceptive tactics that romance scammers use. I was told various stories of hardship and why…” Feb 4, 15:27
- on Danielle Delaunay/Danielle Genevieve – Stolen Identity/Stolen Photos – Impersonation Victim UPDATED 2024: “Yes, I’m in that exact situation also. “Danielle” has seriously scammed me for 3 years now. “She” (he) doesn’t know…” Feb 4, 14:58
- on An Essay on Justice and Money Recovery – 2026: “you are so right I accidentally clicked on online justice I signed an agreement for 12k upfront but cd only…” Feb 3, 08:16
- on The SCARS Institute Top 50 Celebrity Impersonation Scams – 2025: “Quora has had visits from scammers pretending to be Keanu Reeves and Paul McCartney in 2025 and 2026.” Jan 27, 17:45
- on Scam Victims Should Limit Their Exposure To Scam News & Scammer Photos: “I used to look at scammers photos all the time; however, I don’t feel the need to do it anymore.…” Jan 26, 23:19
- on After A Scam, No One Can Tell You How You Will React: “This article was very informative, my scams happened 5 years ago; however, l do remember several of those emotions and/or…” Jan 23, 17:17
- on Situational Awareness and How Trauma Makes Scam Victims Less Safe – 2024: “I need to be more observant and I am practicing situational awareness. I’m saving this article to remind me of…” Jan 21, 22:55
ARTICLE META
Important Information for New Scam Victims
- Please visit www.ScamVictimsSupport.org – a SCARS Website for New Scam Victims & Sextortion Victims
- Enroll in FREE SCARS Scam Survivor’s School now at www.SCARSeducation.org
- Please visit www.ScamPsychology.org – to more fully understand the psychological concepts involved in scams and scam victim recovery
If you are looking for local trauma counselors please visit counseling.AgainstScams.org or join SCARS for our counseling/therapy benefit: membership.AgainstScams.org
If you need to speak with someone now, you can dial 988 or find phone numbers for crisis hotlines all around the world here: www.opencounseling.com/suicide-hotlines
A Note About Labeling!
We often use the term ‘scam victim’ in our articles, but this is a convenience to help those searching for information in search engines like Google. It is just a convenience and has no deeper meaning. If you have come through such an experience, YOU are a Survivor! It was not your fault. You are not alone! Axios!
A Question of Trust
At the SCARS Institute, we invite you to do your own research on the topics we speak about and publish, Our team investigates the subject being discussed, especially when it comes to understanding the scam victims-survivors experience. You can do Google searches but in many cases, you will have to wade through scientific papers and studies. However, remember that biases and perspectives matter and influence the outcome. Regardless, we encourage you to explore these topics as thoroughly as you can for your own awareness.
Statement About Victim Blaming
SCARS Institute articles examine different aspects of the scam victim experience, as well as those who may have been secondary victims. This work focuses on understanding victimization through the science of victimology, including common psychological and behavioral responses. The purpose is to help victims and survivors understand why these crimes occurred, reduce shame and self-blame, strengthen recovery programs and victim opportunities, and lower the risk of future victimization.
At times, these discussions may sound uncomfortable, overwhelming, or may be mistaken for blame. They are not. Scam victims are never blamed. Our goal is to explain the mechanisms of deception and the human responses that scammers exploit, and the processes that occur after the scam ends, so victims can better understand what happened to them and why it felt convincing at the time, and what the path looks like going forward.
Articles that address the psychology, neurology, physiology, and other characteristics of scams and the victim experience recognize that all people share cognitive and emotional traits that can be manipulated under the right conditions. These characteristics are not flaws. They are normal human functions that criminals deliberately exploit. Victims typically have little awareness of these mechanisms while a scam is unfolding and a very limited ability to control them. Awareness often comes only after the harm has occurred.
By explaining these processes, these articles help victims make sense of their experiences, understand common post-scam reactions, and identify ways to protect themselves moving forward. This knowledge supports recovery by replacing confusion and self-blame with clarity, context, and self-compassion.
Additional educational material on these topics is available at ScamPsychology.org – ScamsNOW.com and other SCARS Institute websites.
Psychology Disclaimer:
All articles about psychology and the human brain on this website are for information & education only
The information provided in this article is intended for educational and self-help purposes only and should not be construed as a substitute for professional therapy or counseling.
While any self-help techniques outlined herein may be beneficial for scam victims seeking to recover from their experience and move towards recovery, it is important to consult with a qualified mental health professional before initiating any course of action. Each individual’s experience and needs are unique, and what works for one person may not be suitable for another.
Additionally, any approach may not be appropriate for individuals with certain pre-existing mental health conditions or trauma histories. It is advisable to seek guidance from a licensed therapist or counselor who can provide personalized support, guidance, and treatment tailored to your specific needs.
If you are experiencing significant distress or emotional difficulties related to a scam or other traumatic event, please consult your doctor or mental health provider for appropriate care and support.
Also read our SCARS Institute Statement about Professional Care for Scam Victims – click here to go to our ScamsNOW.com website.















Thank you for your comment. You may receive an email to follow up. We never share your data with marketers.