
SCARS Institute’s Encyclopedia of Scams™ Published Continuously for 25 Years

What Are Internet Protocols
Internet protocols are a set of rules that govern the communication and exchange of data over the Internet. They define how data is formatted, transmitted, and received. Internet protocols are essential for the Internet to function, and they are used in a wide variety of applications, including web browsing, email, file sharing, and streaming video.
Here are some examples of common Internet protocols:
- TCP/IP (Transmission Control Protocol/Internet Protocol): TCP/IP is the suite of protocols that underlies the Internet. It is responsible for breaking down data into packets, transmitting the packets across networks, and reassembling the packets at the destination.
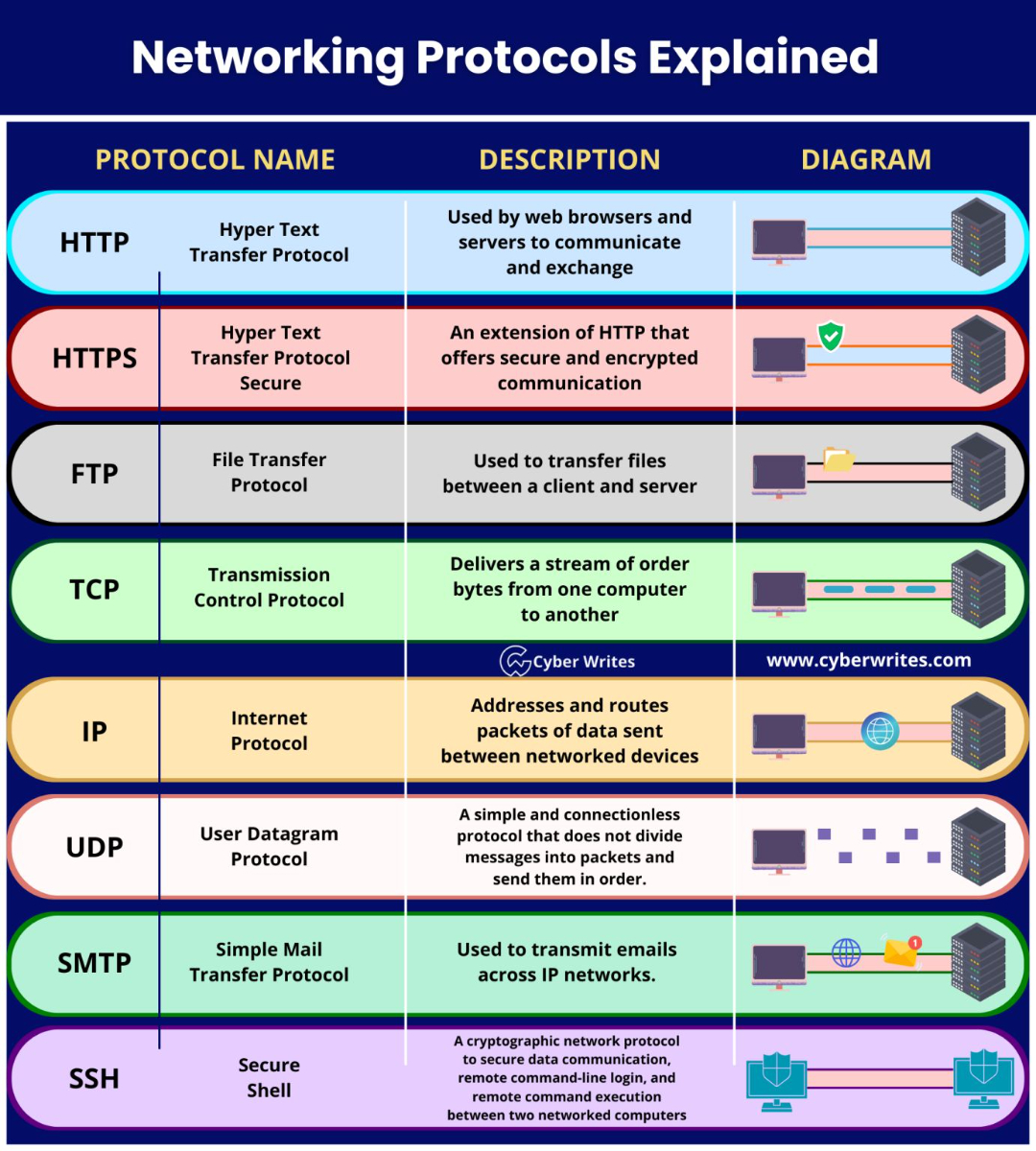
- HTTP (Hypertext Transfer Protocol): HTTP is the protocol used to transfer web pages and other resources over the Internet.
- HTTPS (Hypertext Transfer Protocol Secure): HTTPS is a secure version of HTTP that uses encryption to protect data in transit.
- FTP (File Transfer Protocol): FTP is a protocol used to transfer files between computers over the Internet.
- SMTP (Simple Mail Transfer Protocol): SMTP is the protocol used to send and receive email.
Internet protocols work by defining a set of rules for how data is formatted, transmitted, and received. For example, the TCP/IP protocol defines how data is broken down into packets, how the packets are transmitted across networks, and how the packets are reassembled at the destination.
When you visit a website, your computer uses the HTTP protocol to request the web page from the server. The server then responds with the web page, which is transmitted to your computer using the TCP/IP protocol.
If you are using a secure website, such as a website that uses HTTPS, your computer will encrypt the data before sending it to the server. The server will then decrypt the data after receiving it. This helps to protect your data from being intercepted by unauthorized users.
Internet protocols are essential for the Internet to function. They provide a framework for computers to communicate with each other and to exchange data. Without Internet protocols, the Internet would not be possible.
Here are some additional benefits of using Internet protocols:
- Reliability: Internet protocols are designed to be reliable and to ensure that data is transmitted correctly.
- Efficiency: Internet protocols are designed to be efficient and to minimize the amount of bandwidth required to transmit data.
- Scalability: Internet protocols are designed to be scalable and to support the large number of devices and users that are connected to the Internet.
Internet protocols are a complex topic, but it is important to have a basic understanding of how they work. By understanding Internet protocols, you can better understand how the Internet works and how to troubleshoot problems that may arise.
Internet Protocols List
Here is a list of all Internet protocols, as defined by the Internet Assigned Numbers Authority (IANA):
- Application layer protocols:
- DNS (Domain Name System)
- FTP (File Transfer Protocol)
- HTTP (Hypertext Transfer Protocol)
- HTTPS (Hypertext Transfer Protocol Secure)
- IMAP (Internet Message Access Protocol)
- POP3 (Post Office Protocol 3)
- SMTP (Simple Mail Transfer Protocol)
- SSH (Secure Shell)
- Telnet
- Transport layer protocols:
- TCP (Transmission Control Protocol)
- UDP (User Datagram Protocol)
- Internet layer protocols:
- ICMP (Internet Control Message Protocol)
- IGMP (Internet Group Management Protocol)
- IP (Internet Protocol)
- IPv4 (Internet Protocol version 4)
- IPv6 (Internet Protocol version 6)
- Link layer protocols:
- ARP (Address Resolution Protocol)
- Ethernet
- PPP (Point-to-Point Protocol)
- Wi-Fi
This list is not exhaustive, and there are many other Internet protocols that are used for specific purposes. However, the protocols listed above are some of the most common and important Internet protocols.
Internet protocols are essential for the Internet to function. They provide a framework for computers to communicate with each other and to exchange data. Without Internet protocols, the Internet would not be possible.
DNS Protocol
The Domain Name System (DNS) protocol is a hierarchical and distributed naming system for computers, services, or any other resources connected to the Internet or a private network. It associates various information with domain names assigned to each of the participating entities. Most prominently, it translates domain names meaningful to humans (e.g., example.com) to the numerical Internet Protocol (IP) addresses needed for locating computer services and devices with the underlying network protocols. By providing a worldwide, distributed directory service, the Domain Name System has been an essential component of the functionality of the Internet since 1985.
DNS protocol works by translating domain names into IP addresses. When a user enters a domain name into a web browser, the browser sends a DNS query to a DNS server. The DNS server then looks up the IP address for the domain name in its database and returns the IP address to the browser. The browser then uses the IP address to connect to the website.
DNS protocol is a hierarchical system, with root DNS servers at the top of the hierarchy. Root DNS servers contain a list of all top-level domains (TLDs), such as .com, .net, and .org. When a DNS server receives a query for a domain name, it first checks the root DNS servers to see if they contain the IP address for the domain name. If the root DNS servers do not contain the IP address, the DNS server will then query the TLD DNS servers for the domain name. This process continues until the DNS server finds the IP address for the domain name or determines that the domain name does not exist.
DNS protocol is a distributed system, with DNS servers located all over the world. This helps to ensure that DNS queries are resolved quickly and efficiently. When a DNS server receives a query for a domain name, it will first check its own cache to see if it already contains the IP address for the domain name. If the DNS server does not contain the IP address in its cache, it will then query other DNS servers until it finds the IP address or determines that the domain name does not exist.
DNS protocol is an essential part of the internet. It allows users to access websites and other resources by using domain names instead of IP addresses. DNS protocol is also used to resolve other types of addresses, such as email addresses and MX records.
Here are some of the benefits of using DNS protocol:
- It is a reliable and efficient way to translate domain names into IP addresses.
- It is a scalable system that can support the large number of devices and users that are connected to the internet.
- It is a distributed system, which helps to ensure that DNS queries are resolved quickly and efficiently.
- It is a free and open standard, which means that anyone can develop and implement DNS servers.
DNS protocol is an essential part of the internet and it is important to understand how it works. By understanding DNS protocol, you can better understand how the internet works and how to troubleshoot problems that may arise.
The FTP Protocol
The File Transfer Protocol (FTP) is a standard network protocol used for the transfer of files between computers over a TCP-based network, such as the Internet. FTP works by opening two connections between the computers trying to communicate with each other. One connection is designated for the commands and replies that get sent between the two clients, and the other channel handles the transfer of file content. During an FTP transmission, there are four commands used by the computers, servers, or proxy servers that are communicating. These are “send,” “get,” “change directory,” and “transfer.”
FTP is a client-server protocol that relies on two communication channels between the client and server: a command channel for controlling the conversation and a data channel for transmitting file content. Here is how a typical FTP transfer works:
- A user typically needs to log on to the FTP server, although some servers make some or all of their content available without a login, a model known as anonymous FTP.
- The client initiates a conversation with the server when the user requests to download a file.
- Using FTP, a client can upload, download, delete, rename, move, and copy files on a server.
FTP is a powerful tool that can be used to transfer files between computers over a network. It is a reliable and efficient protocol that can support the transfer of large files. FTP is also a versatile protocol that can be used to transfer files between computers of different types.
Here are some of the benefits of using FTP:
- It is a reliable and efficient way to transfer files between computers over a network.
- It is a scalable system that can support the transfer of large files.
- It is a versatile protocol that can be used to transfer files between computers of different types.
- It is a free and open standard, which means that anyone can develop and implement FTP servers.
FTP is an important protocol for businesses and individuals who need to transfer files between computers. It is a reliable and efficient protocol that can be used to transfer large files between computers of different types.
The HTTP & HTTPS Protocols
HTTP (Hypertext Transfer Protocol) is the protocol used to transfer web pages and other resources over the internet. It is a text-based protocol that uses a client-server architecture.
When a user visits a website, their browser sends an HTTP request to the web server. The web server then responds with the requested web page, which is transmitted to the user’s browser using the TCP/IP protocol.
HTTPS (Hypertext Transfer Protocol Secure) is a secure version of HTTP that uses encryption to protect data in transit. HTTPS is used by most websites today, including all major social media platforms, e-commerce websites, and banks.
When a user visits a website that uses HTTPS, their browser will establish a secure connection with the web server. This means that all data transmitted between the browser and the web server will be encrypted.
HTTPS is important because it protects users from a variety of attacks, such as man-in-the-middle attacks and eavesdropping.
Here is a comparison of HTTP and HTTPS:
- HTTP: No encryption – Transferring web pages and other resources over the internet – is being phased out
- HTTPS: Has encryption – Transferring sensitive data, such as credit card numbers and passwords – now taking over for HTTP
It is important to note that HTTPS is not a guarantee that a website is safe. However, it does make it much more difficult for attackers to steal your data.
Here are some of the benefits of using HTTPS:
- It protects users from a variety of attacks, such as man-in-the-middle attacks and eavesdropping.
- It builds trust with users.
- It improves search engine ranking.
- It is required for certain features, such as online payments.
If you are building a website, it is important to use HTTPS. It is a simple way to protect your users and improve your website’s security.
The IMAP & POP3 Email Protocols
IMAP (Internet Message Access Protocol) and POP3 (Post Office Protocol 3) are both protocols used to retrieve email messages from a remote server. However, there are some key differences between the two protocols.
IMAP is a newer protocol that allows users to view and manage their email messages on the server. Users can read, delete, and move messages without having to download them to their local computer. IMAP also supports multiple devices, so users can access their email from anywhere.
POP3 is an older protocol that downloads email messages to the user’s local computer. Once the messages have been downloaded, they are deleted from the server. POP3 does not support multiple devices, so users can only access their email from the computer where the messages have been downloaded.
Here is a table that summarizes the key differences between IMAP and POP3:
- IMAP: Supports multiple devices; Allows users to view and manage messages on the server – preferred for synchronization
- POP3: Downloads messages to the local computer; Deletes messages from the server when they are downloaded
Which protocol you choose depends on your needs. If you need to access your email from multiple devices or if you want to be able to view and manage your messages on the server, then IMAP is the better choice. If you only need to access your email from one device and you prefer to download your messages to your local computer, then POP3 is the better choice.
Here are some of the benefits of using IMAP:
- It allows users to view and manage their email messages on the server.
- It supports multiple devices, so users can access their email from anywhere.
- It is more efficient than POP3, as it does not need to download the entire message each time it is viewed.
Here are some of the benefits of using POP3:
- It is simpler to set up and use than IMAP.
- It is more efficient for users who only need to access their email from one device.
- It is more compatible with older email clients.
Overall, IMAP is the better choice for most users. It is more flexible and offers more features than POP3. However, POP3 may be a better choice for users who only need to access their email from one device and who prefer to download their messages to their local computer.
The SMTP Protocol
The Simple Mail Transfer Protocol (SMTP) is an Internet standard communication protocol for electronic mail transmission. Mail servers and other message transfer agents use SMTP to send and receive mail messages. User-level email clients typically use SMTP only for sending messages to a mail server for relaying and typically submit outgoing emails to the mail server on port 587 or 465 per RFC 8314. For retrieving messages, IMAP (which replaced the older POP3) is standard, but proprietary servers also often implement proprietary protocols, e.g., Exchange ActiveSync.
SMTP is a client-server protocol that uses a TCP/IP connection to transfer email messages. When a user sends an email, their email client will connect to the SMTP server of the recipient’s email address. The email client will then send the email message to the SMTP server, which will then deliver the message to the recipient’s email inbox.
SMTP is a text-based protocol, and the commands and responses are exchanged in plain text. This makes it easy to debug SMTP problems, but it also means that SMTP is vulnerable to eavesdropping.
To protect SMTP traffic from eavesdropping, many SMTP servers support STARTTLS encryption. STARTTLS encryption allows the client and server to negotiate an encryption protocol, such as TLS, to encrypt the traffic.
SMTP is a reliable and efficient protocol for sending email messages. It is used by billions of people around the world to send email every day.
Here are some of the benefits of using SMTP:
- It is a reliable and efficient protocol for sending email messages.
- It is supported by all major email clients and servers.
- It is easy to set up and use.
- It is secure, as it supports STARTTLS encryption.
Overall, SMTP is the best protocol for sending email messages. It is reliable, efficient, secure, and widely supported.
The SSH Protocol
SSH works by encrypting all traffic between the client and server, including the login credentials and any data that is transmitted. This makes it a very secure way to access remote computers and services.
SSH is a client-server protocol, and it uses a public-key cryptography system to authenticate the client and server. This means that the client and server do not need to share any secret passwords in order to establish a secure connection.
SSH is a very versatile protocol, and it can be used for a variety of purposes. Some of the most common uses of SSH include:
- Remote login: SSH allows users to log in to remote computers securely. This can be useful for system administration tasks, such as managing servers and troubleshooting problems.
- Remote file transfer: SSH also allows users to transfer files between computers securely. This can be useful for copying files between computers or for backing up data.
- Tunneling: SSH can be used to tunnel other traffic through a secure connection. This can be useful for accessing websites or services that are blocked by a firewall.
- Port forwarding: SSH can be used to forward ports from a remote computer to a local computer. This can be useful for running applications on a remote computer that require access to a specific port on the local computer.
SSH is a powerful and versatile protocol that can be used for a variety of purposes. It is a very secure way to access remote computers and services, and it is widely supported by all major operating systems.
Here are some of the benefits of using SSH:
- It is a very secure way to access remote computers and services.
- It is very versatile and can be used for a variety of purposes.
- It is widely supported by all major operating systems.
- It is easy to set up and use.
Overall, SSH is a great choice for anyone who needs to access remote computers and services securely. It is a powerful and versatile protocol that is easy to use and widely supported.
The Telnet Protocol
Telnet (short for Teletype Network) is a client-server protocol that provides a text-based interface to remote computers. It is one of the oldest internet protocols that comes from the Teletypes days, and it is still widely used today for system administration and troubleshooting tasks.
Telnet works by opening a TCP/IP connection between the client and server. The client then sends commands to the server, and the server responds with output. The client can then display the output to the user or interact with the server in other ways.
Telnet is a text-based protocol, which means that it does not support graphics or other complex data types. This makes it a simple and efficient protocol, but it also means that it is not suitable for all applications.
Telnet is also not a secure protocol. All traffic between the client and server is transmitted in plain text, which makes it vulnerable to eavesdropping and other attacks.
Despite its limitations, Telnet is a useful tool for system administrators and other technical users. It is a simple and reliable way to access remote computers and perform tasks such as managing servers, troubleshooting problems, and transferring files.
Here are some of the benefits of using Telnet:
- It is a simple and efficient protocol.
- It is widely supported by all major operating systems.
- It is easy to set up and use.
Here are some of the drawbacks of using Telnet:
- It is not a secure protocol.
- It is a text-based protocol, which means that it does not support graphics or other complex data types.
Overall, Telnet is a useful tool for system administrators and other technical users. However, it is important to be aware of its limitations, such as its lack of security.
Here are some tips for using Telnet securely:
- Use a VPN to encrypt all traffic between the client and server.
- Use strong passwords and change them regularly.
- Be careful about what commands you run on the remote server.
- Only enable Telnet access for authorized users.
If you are not comfortable with the security risks associated with Telnet, you may want to consider using a more secure protocol, such as SSH.
The TCP & UDP Protocols
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are both transport layer protocols that are used to send data over the internet. However, there are some key differences between the two protocols.
TCP is a connection-oriented protocol, which means that it establishes a connection between the sender and receiver before sending any data. This connection ensures that all data is delivered reliably and in the correct order. TCP also uses flow control and congestion control mechanisms to ensure that the sender does not overwhelm the receiver with data.
UDP is a connectionless protocol, which means that it does not establish a connection between the sender and receiver before sending any data. This makes UDP faster than TCP, but it also makes it less reliable. UDP does not guarantee that all data will be delivered, or that it will be delivered in the correct order. UDP also does not use flow control or congestion control mechanisms.
TCP is the preferred protocol for most applications, such as web browsing, email, and file transfer. It is important to use a reliable protocol for these applications to ensure that data is not lost or corrupted.
UDP is the preferred protocol for applications where speed is more important than reliability, such as online gaming and streaming video. UDP is also used for some network management protocols, such as ICMP and SNMP.
Here are some examples of when to use TCP:
- Web browsing
- File transfer
- Online banking
- Video conferencing
Here are some examples of when to use UDP:
- Online gaming
- Streaming video
- Voice over IP (VoIP)
- Network management protocols
Overall, TCP and UDP are both important protocols that are used for a variety of purposes. TCP is the preferred protocol for most applications, but UDP is the preferred protocol for applications where speed is more important than reliability.
The ICMP & IGMP Protocols
ICMP (Internet Control Message Protocol) and IGMP (Internet Group Management Protocol) are both network layer protocols that are used to diagnose and manage network communication.
ICMP is used to send error messages and other control messages between network devices. For example, ICMP can be used to report that a packet was lost or that a destination host is unreachable. ICMP is also used to send ping messages, which can be used to test the connectivity between two network devices.
IGMP is used to manage multicast groups. A multicast group is a group of network hosts that want to receive the same multicast traffic. IGMP allows hosts to join and leave multicast groups, and it also allows routers to know which multicast groups are on their networks.
ICMP and IGMP are both important protocols for maintaining and troubleshooting networks. ICMP helps to ensure that network devices are communicating properly, while IGMP helps to ensure that multicast traffic is delivered efficiently.
Here are some examples of when ICMP and IGMP are used:
- ICMP:
- A router sends an ICMP error message to a host to report that a packet was lost.
- A host sends an ICMP ping message to another host to test the connectivity between the two hosts.
- IGMP:
- A host sends an IGMP join message to a router to join a multicast group.
- A router sends an IGMP leave message to a host to leave a multicast group.
Overall, ICMP and IGMP are both essential protocols for the proper functioning of the internet. They help to ensure that network devices are communicating properly and that multicast traffic is delivered efficiently.
The IP, IPv4 and IPv6 Protocols
The Internet Protocol (IP) is the suite of protocols that underlies the internet. It is responsible for breaking down data into packets, transmitting the packets across networks, and reassembling the packets at the destination.
IPv4 (Internet Protocol version 4) is the current version of IP that is used by most of the internet today. IPv4 uses 32-bit addresses, which limits the number of possible addresses to about 4.3 billion. This is becoming a problem as the internet continues to grow and more devices are connected to it.
IPv6 (Internet Protocol version 6) is the next generation of IP that is designed to address the limitations of IPv4. IPv6 uses 128-bit addresses, which provides a much larger address space. IPv6 also includes other features that make it more efficient and scalable than IPv4.
Here is a summary of the key differences between IPv4 and IPv6:
IPv4
- 32-bit addresses
- 4.3 billion possible addresses
- Widely used today
- Becoming limited
IPv6
- 128-bit addresses
- 340 undecillion possible addresses (1,000,000,000,000,000,000,000,000,000)
- Still under deployment
- More efficient and scalable
- Supports mobility
- Enhanced security features
IPv6 is the future of IP. It is a more powerful and versatile protocol than IPv4. As more devices are connected to the internet, IPv6 will become essential for ensuring that the internet remains reliable and scalable.
Here are some of the benefits of using IPv6:
- Larger address space
- More efficient and scalable
- Supports mobility
- Enhanced security features
Overall, IPv6 is the better choice for new networks and devices. It is more modern, more flexible, and more secure than IPv4.
The ARP & PPP Protocols
ARP (Address Resolution Protocol) is a protocol used to map Internet Protocol (IP) addresses to Media Access Control (MAC) addresses. MAC addresses are uniquely assigned to network devices, and they are used to identify devices on a local network. IP addresses are used to identify devices on the internet.
ARP works by sending a broadcast message to all devices on the local network. The broadcast message contains the IP address of the device that the sender is trying to reach. All devices on the local network receive the broadcast message, but only the device with the matching IP address will respond.
The response to an ARP broadcast message contains the MAC address of the device with the matching IP address. The sender of the ARP broadcast message then stores the MAC address in its ARP cache. This allows the sender to send messages directly to the device without having to send broadcast messages.
PPP (Point-to-Point Protocol) is a protocol used to establish a point-to-point connection between two devices. PPP is often used to connect a computer to a dial-up modem or a digital subscriber line (DSL) modem.
PPP works by establishing a three-way handshake between the two devices. The three-way handshake allows the devices to negotiate the parameters of the connection, such as the authentication protocol and the data link protocol.
Once the three-way handshake is complete, the devices can start exchanging data. PPP can be used to carry a variety of different protocols, such as TCP/IP, IPX, and NetBEUI.
ARP and PPP are both important protocols for networking. ARP is used to map IP addresses to MAC addresses, and PPP is used to establish point-to-point connections between two devices.
Here are some of the benefits of using ARP and PPP:
- ARP:
- It allows devices to communicate with each other on a local network without having to know each other’s MAC addresses.
- It is a simple and efficient protocol.
- PPP:
- It provides a reliable and secure way to establish a point-to-point connection between two devices.
- It can be used to carry a variety of different protocols.
Overall, ARP and PPP are two important protocols that are used to facilitate communication between devices on a network.
The Ethernet & WiFi Protocols
Ethernet and Wi-Fi are two of the most common networking protocols in use today. Ethernet is a wired protocol that uses cables to connect devices to a network, while Wi-Fi is a wireless protocol that uses radio waves.
Ethernet is a very reliable and fast protocol, making it ideal for applications such as gaming, streaming video, and file sharing. It is also relatively inexpensive to install and maintain. However, Ethernet can be inconvenient in some situations, such as when connecting devices in different rooms or in a public space.
Wi-Fi is a very convenient protocol, as it allows devices to connect to a network without the need for cables. This makes it ideal for applications such as browsing the web, checking email, and using social media. Wi-Fi is also relatively easy to set up and use. However, Wi-Fi can be less reliable and slower than Ethernet, and it can be more susceptible to interference.
Here is a summary of the key differences between Ethernet and Wi-Fi:
Ethernet
- Wired protocol
- Reliable and fast
- Inexpensive to install and maintain
- Can be inconvenient in some situations
Wi-Fi
- Wireless protocol
- Convenient
- Easy to set up and use
- Can be less reliable and slower than Ethernet
- Can be more susceptible to interference
Which protocol is better for you depends on your needs. If you require a reliable and fast connection, then Ethernet is the better choice. If you need a convenient connection, then Wi-Fi is the better choice.
Here are some examples of when to use Ethernet:
- In a business or organization where high performance is required
- In a home or other place where cables are not practical or desirable
- For connecting devices that do not have Wi-Fi support, such as printers and servers
Here are some examples of when to use Wi-Fi:
- In a home or other place where cables are not practical or desirable
- For connecting devices that have Wi-Fi support, such as laptops, smartphones, and tablets
- For connecting devices to a public Wi-Fi network, such as in a coffee shop or airport
Overall, Ethernet and Wi-Fi are both important networking protocols that have different strengths and weaknesses. The best protocol for you depends on your specific needs.
-/ 30 /-
What do you think about this?
Please share your thoughts in a comment below!
Table of Contents
- Internet & Cybersecurity Basics
- What Are Internet Protocols
- Internet Protocols List
- DNS Protocol
- The FTP Protocol
- The HTTP & HTTPS Protocols
- The IMAP & POP3 Email Protocols
- The SMTP Protocol
- The SSH Protocol
- The Telnet Protocol
- The TCP & UDP Protocols
- The ICMP & IGMP Protocols
- The IP, IPv4 and IPv6 Protocols
- The ARP & PPP Protocols
- The Ethernet & WiFi Protocols
LEAVE A COMMENT?
Recent Comments
On Other Articles
- SCARS Institute Editorial Team on The Story Of Kira Lee Orsag (aka Dani Daniels) [Updated]: “There is NO evidence and she is not, she is a victim too. Sebastian, stop letting your anger think for…” Mar 6, 23:18
- on The Story Of Kira Lee Orsag (aka Dani Daniels) [Updated]: “There is real evidence that behind these two people there is something that not many people know. This woman is…” Mar 4, 03:58
- on Signs of Good & Bad Scam Victim Emotional Health: “ty this helps me with knowing why I cant quit eating when I am not hungry and when I crave…” Mar 2, 20:43
- on The SCARS Institute Top 50 Celebrity Impersonation Scams – 2025: “You should probably add Lawrence O’donnell as a scam also. I clicked on a site on tic tok for msnbc,…” Mar 2, 08:41
- on Finally Tax Relief for American Scam Victims is on the Horizon – 2026: “I just did my taxes for 2025 my tax account said so far for romances scam we cd not take…” Feb 25, 19:50
- on Reporting Scams & Interacting With The Police – A Scam Victim’s Checklist [VIDEO]: “Yes, this is a scam. For your own sanity, just block them completely.” Feb 25, 15:37
- on Danielle Delaunay/Danielle Genevieve – Stolen Identity/Stolen Photos – Impersonation Victim UPDATED 2024: “She goes by the name of Sanrda John now” Feb 25, 10:26
- on Reporting Scams & Interacting With The Police – A Scam Victim’s Checklist [VIDEO]: “So far I have not been scam out of any money because I was aware not to give the money…” Feb 25, 07:46
- on Love Bombing And How Romance Scam Victims Are Forced To Feel: “I was love bombed to the point that I would do just about anything for the scammer(s). I was told…” Feb 11, 14:24
- on Dani Daniels (Kira Lee Orsag): Another Scammer’s Favorite: “You provide a valuable service! I wish more people knew about it!” Feb 10, 15:05
ARTICLE META
Important Information for New Scam Victims
- Please visit www.ScamVictimsSupport.org – a SCARS Website for New Scam Victims & Sextortion Victims
- Enroll in FREE SCARS Scam Survivor’s School now at www.SCARSeducation.org
- Please visit www.ScamPsychology.org – to more fully understand the psychological concepts involved in scams and scam victim recovery
If you are looking for local trauma counselors please visit counseling.AgainstScams.org or join SCARS for our counseling/therapy benefit: membership.AgainstScams.org
If you need to speak with someone now, you can dial 988 or find phone numbers for crisis hotlines all around the world here: www.opencounseling.com/suicide-hotlines
A Note About Labeling!
We often use the term ‘scam victim’ in our articles, but this is a convenience to help those searching for information in search engines like Google. It is just a convenience and has no deeper meaning. If you have come through such an experience, YOU are a Survivor! It was not your fault. You are not alone! Axios!
A Question of Trust
At the SCARS Institute, we invite you to do your own research on the topics we speak about and publish, Our team investigates the subject being discussed, especially when it comes to understanding the scam victims-survivors experience. You can do Google searches but in many cases, you will have to wade through scientific papers and studies. However, remember that biases and perspectives matter and influence the outcome. Regardless, we encourage you to explore these topics as thoroughly as you can for your own awareness.
Statement About Victim Blaming
SCARS Institute articles examine different aspects of the scam victim experience, as well as those who may have been secondary victims. This work focuses on understanding victimization through the science of victimology, including common psychological and behavioral responses. The purpose is to help victims and survivors understand why these crimes occurred, reduce shame and self-blame, strengthen recovery programs and victim opportunities, and lower the risk of future victimization.
At times, these discussions may sound uncomfortable, overwhelming, or may be mistaken for blame. They are not. Scam victims are never blamed. Our goal is to explain the mechanisms of deception and the human responses that scammers exploit, and the processes that occur after the scam ends, so victims can better understand what happened to them and why it felt convincing at the time, and what the path looks like going forward.
Articles that address the psychology, neurology, physiology, and other characteristics of scams and the victim experience recognize that all people share cognitive and emotional traits that can be manipulated under the right conditions. These characteristics are not flaws. They are normal human functions that criminals deliberately exploit. Victims typically have little awareness of these mechanisms while a scam is unfolding and a very limited ability to control them. Awareness often comes only after the harm has occurred.
By explaining these processes, these articles help victims make sense of their experiences, understand common post-scam reactions, and identify ways to protect themselves moving forward. This knowledge supports recovery by replacing confusion and self-blame with clarity, context, and self-compassion.
Additional educational material on these topics is available at ScamPsychology.org – ScamsNOW.com and other SCARS Institute websites.
Psychology Disclaimer:
All articles about psychology and the human brain on this website are for information & education only
The information provided in this article is intended for educational and self-help purposes only and should not be construed as a substitute for professional therapy or counseling.
While any self-help techniques outlined herein may be beneficial for scam victims seeking to recover from their experience and move towards recovery, it is important to consult with a qualified mental health professional before initiating any course of action. Each individual’s experience and needs are unique, and what works for one person may not be suitable for another.
Additionally, any approach may not be appropriate for individuals with certain pre-existing mental health conditions or trauma histories. It is advisable to seek guidance from a licensed therapist or counselor who can provide personalized support, guidance, and treatment tailored to your specific needs.
If you are experiencing significant distress or emotional difficulties related to a scam or other traumatic event, please consult your doctor or mental health provider for appropriate care and support.
Also read our SCARS Institute Statement about Professional Care for Scam Victims – click here to go to our ScamsNOW.com website.
















Thank you for your comment. You may receive an email to follow up. We never share your data with marketers.